
UKRAINIAN CATHOLIC UNIVERSITY
BACHELOR THESIS
Designing user interface for "Automated
convenience store" mobile application
based on user experience
Author:
Oksana OLENIUK
Supervisor:
Oleksiy DATSIV
A thesis submitted in fulfillment of the requirements
for the degree of Bachelor of Science
in the
Department of Computer Sciences
Faculty of Applied Sciences
Lviv 2019

iii
Declaration of Authorship
I, Oksana OLENIUK, declare that this thesis titled, “Designing user interface for "Au-
tomated convenience store" mobile application based on user experience” and the
work presented in it are my own. I confirm that:
• This work was done wholly or mainly while in candidature for a research de-
gree at this University.
• Where any part of this thesis has previously been submitted for a degree or
any other qualification at this University or any other institution, this has been
clearly stated.
• Where I have consulted the published work of others, this is always clearly
attributed.
• Where I have quoted from the work of others, the source is always given. With
the exception of such quotations, this thesis is entirely my own work.
• I have acknowledged all main sources of help.
• Where the thesis is based on work done by myself jointly with others, I have
made clear exactly what was done by others and what I have contributed my-
self.
Signed:
Date:
v
UKRAINIAN CATHOLIC UNIVERSITY
Faculty of Applied Sciences
Bachelor of Science
Designing user interface for "Automated convenience store" mobile application
based on user experience
by Oksana OLENIUK
Abstract
In the retail grocery market, there is a high level of competition, redundancy in trad-
ing space and a high threat from online stores. In the struggle for buyers, stores are
looking for ways to improve the quality of work using innovative technology.
What is innovation? It is a way an entrepreneur creates new resources which
generate revenue or provides existing resources with increased potential for profit
multiplication.
One of the most well-known innovations in the retail sector is self-service tech-
nology (SST). SST is a technology that allows the buyer to get the service regardless
of the direct involvement of the shop staff in providing this service . At the moment,
there are many successful examples of shops that implement modern technologies,
and with them, they wholly or partially automate the traditional flow of activities.
Good examples are projects from Amazon (AmazonGo) and Auchan (Auchan
minute).
There are many options for such implementation. For example, a registered user
can log in to the store using the mobile application. Scan QR Code on products
with a smart-phone, pay via the app, and after confirming leave the store. Also, the
payment problem could be solved with the self-service cash register, which reads
the product bar code.
Potentially, such a store in Ukraine could use men and women from young adult
to middle-aged how are familiar with the smartphones and desire to buy 2-3 on-the-
go products. Such solutions will give people the opportunity at any time to get the
purchases in a modern way with a user-friendly UI / UX interface, with virtually no
queues.
From a financial point of view, such retail sales reduce the cost of maintaining the
store and make it impossible to steal purchases and cash by cashiers. Also, showing
confidence in the buyer branding the network as open, honest and modern, which
can be interesting to potential users.
Analysis of existing solutions, working examples, technologies and patterns could
provide the answer if it is relevant to run the business of this area or provide autom-
atization generally or partly.
vii
Acknowledgements
I want to express my gratitude Oleksiy Datsiv and Oles Dobosevych who supervised
and directed my research for this thesis. Special thanks to Yaroslav Prytula for hints
about economic analysis.
Also, this work would not be possible without my team and customer Victor
which provided primary analysis for Automated Convenience Store as a part of
Business Analyst course.
Finally, I am grateful to the Ukrainian Catholic University for the undergraduate
program, which allowed me to become part of the university, overcome difficulties,
use the opportunities offered by the university, and feel the unique atmosphere of
kindness.
ix
Contents
Declaration of Authorship iii
Abstract v
Acknowledgements vii
1 Related works 1
1.1 Self-service technology . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
1.2 Decision-making model for using innovations . . . . . . . . . . . . . . 1
1.3 RFID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
2 Food Retail Problems 3
2.1 Perspective of the Store . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2.2 Perspective of the Customer . . . . . . . . . . . . . . . . . . . . . . . . . 3
2.2.1 Problems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2.2.2 Analysis of customer perception of technological innovation . . 4
2.3 Conclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
3 Existing Solutions 5
3.1 RFID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
3.2 Mobile solutions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
3.3 Another self-service equipment . . . . . . . . . . . . . . . . . . . . . . . 5
4 The proposed solution 7
4.1 Registration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
4.2 Exit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
4.3 Add a product to the grocery basket . . . . . . . . . . . . . . . . . . . . 7
4.4 Payment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
4.5 Entrance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
4.6 Additionally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
4.7 Trust system . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
4.7.1 Bank of court decisions . . . . . . . . . . . . . . . . . . . . . . . 8
4.7.2 Receiving personal data . . . . . . . . . . . . . . . . . . . . . . . 10
4.7.3 Questionnaire . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
4.8 Economic feasibility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
4.8.1 Mathematical model . . . . . . . . . . . . . . . . . . . . . . . . . 11
4.8.2 Net profit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
4.8.3 Payback period . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
4.8.4 IRR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
4.8.5 NPV . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
4.8.6 Conclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
4.9 Additionally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
4.9.1 Equip several traditional cash desks . . . . . . . . . . . . . . . . 16
x
4.9.2 Staff Assistance . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
4.9.3 Increasing the effectiveness of surveillance cameras . . . . . . . 16
4.9.4 Loyalty program . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
4.10 Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
4.10.1 Registration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
4.10.2 Login . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
4.10.3 Profile update . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
4.10.4 Password reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
4.10.5 Add credit card . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
4.10.6 History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
4.10.7 Shopping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
4.11 Low fidelity prototypes . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
4.12 Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Bibliography 29
xi
List of Figures
4.1 Feature model Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
4.2 Flowchart: Registration . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
4.3 Flowchart: Log in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
4.4 Flowchart: Profile update . . . . . . . . . . . . . . . . . . . . . . . . . . 19
4.5 Flowchart: Password reset . . . . . . . . . . . . . . . . . . . . . . . . . . 20
4.6 Flowchart: Add credit card . . . . . . . . . . . . . . . . . . . . . . . . . 21
4.7 Flowchart: History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
4.8 Flowchart: Shopping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
4.9 UserFlow: Login . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
4.10 UserFlow: Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
4.11 UserFlow: Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
4.12 UserFlow: Shop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
xiii
List of Tables
3.1 Comparative analysis: RFID - Bar code - QR code. . . . . . . . . . . . . 6
4.1 Assumption of financial model . . . . . . . . . . . . . . . . . . . . . . . 12
4.2 CAPEX: 1st Traditional Store . . . . . . . . . . . . . . . . . . . . . . . . 13
4.3 CAPEX: 1st Automated convenience store . . . . . . . . . . . . . . . . 13
4.4 Net Profit: Comparison between Automated Convenience Store and
Traditional Shop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
4.5 Payback period: Comparison between Automated Convenience Store
and Traditional Shop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
4.6 IRR: Comparison between Automated Convenience Store and Tradi-
tional Shop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
4.7 NPV : Comparison between Automated Convenience Store and Tra-
ditional Shop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
4.8 CAPEX: N Traditional Store . . . . . . . . . . . . . . . . . . . . . . . . . 15
4.9 CAPEX: N Automated convenience store . . . . . . . . . . . . . . . . . 15
4.10 Net Profit for 10 shops: Comparison between Automated Convenience
Store and Traditional Shop . . . . . . . . . . . . . . . . . . . . . . . . . . 16
4.11 Payback period for 10 shops: Comparison between Automated Con-
venience Store and Traditional Shop . . . . . . . . . . . . . . . . . . . . 16
xv
List of Abbreviations
SST Self - Service Technologies
RFID Radio - freguency identification
ATM Automated Teller Machine
SMS Short Message Service
CVV Card Verification Value
QR code Quick Responce code
PL Profit and Loss
NPV Net Present Value
IRR Internal Rate of Return
1
Chapter 1
Related works
1.1 Self-service technology
The most critical factor for the success of innovation, and especially innovation in
the self-service field and others in which a person works closely with innovation,
is the need to study the human perception of technology and its current knowl-
edge and skills in this topic. "Intentions to Use Self-Service Technologies: A Con-
fluence of Multiple Attitudes" (Curran, Meuter, and Surprenant, 2003)conducts an
in-depth study of how consumers relate to technology, as well as the attitude of ser-
vice providers to the use of this technology. The research described and tested three
structural models that describe the consumer behavior patterns, their intentions to
use technologies. Having verified such models, one can understand which the user
will select and which ones they will be most familiar to use.
1.2 Decision-making model for using innovations
The next step is to communicate and integrate the innovation to future consumers
in the proper way using the most effective procedure. The problem is that typically
in a case with innovation there is no one unique way to provide the success of the
innovation."Decision-making model for using innovations" (Rogers, 1995) give us
the most important steps of diffusion of innovation which should be counted. This
paper describes Everett Rogers four main elements in the diffusion of innovations,
such as the innovation itself, communication channels, time, and a social system.
The study corrects the steps to introduce innovation in the grocery retail business,
as it explains the psychology of the consumer.
1.3 RFID
"RFID handbook fundamentals" provides information about the functionality of RFID
technology at physical and IT-related principles underlying this field. Also, books
provide an overview of various technologies which could be applied for food retails
(Finkenzeller, 2010).
The aim of this paper "Radio frequency identification and food retailing in the
UK" (Jones et al., 2005)is to provide an overview of radio frequency identification
(RFID) technology and describe the advantages and disadvantages of using technol-
ogy for food retailers. The main focus of this paper is the use of RFID on different
stages throughout the supply chain, accurately to monitor temperature and food
safety in the food industry.
3
Chapter 2
Food Retail Problems
2.1 Perspective of the Store
The first impetus of implementing self-check technology is the need to change the
work process of the retail network.
The inner store needs:
• Reduce maintenance costs for store personnel;
• Increase in user loyalty. The user who has found the profit of using the SST
will encourage other buyers;
• Increase sales volume of the intimate goods;
• Reduce store dependence of fast staff changing process;
• Increase speed of paying for goods;
• Increase the space for goods in the store;
• Reduce the number of shoplifting crimes. (Ivanov and Mayorova, 2015)
The external store needs:
• Limitation of the staff work during the weekend and the holidays by law.
• Limitation of understanding between the staff and customers through lan-
guage barriers.
2.2 Perspective of the Customer
2.2.1 Problems
When introducing SST, an important step is to study the user’s desire in the retail
field. Example:
• Faster service;
• Getting pleasure from buying ("wow effect");
• Purchasing without the help of the staff (Davidson, Bates, and Bass, 2002).

4 Chapter 2. Food Retail Problems
2.2.2 Analysis of customer perception of technological innovation
According to E. Rogers, potential consumers of innovation can be divided into five
categories based on personal inclination for innovation: innovators, early followers,
early majority, late majority.
According to Rogers, for successful innovation, the interconnection between dif-
ferent groups of consumers is required, as when communication between the groups
is exchanged information about the innovation.
Therefore, adaptation during the work of the newest organizations is important.
For a better understanding of the process of user perception of innovation, the model
of innovation diffusion by E. Rodgers is considered. This model consists of 5 stages:
• Value - the consumer receives information about innovation;
• Recovery - the consumer formulates positive or negative changes to innova-
tions based on previous experience of such technology (for example, an ATM)
and knows about current innovation;
• Decision - the consumer decides on who will use the innovation;
• Testing - the consumer uses innovation;
• Approval - the consumer conducts analysis and knowledge of the roads of his
correct decision on the use of innovation.
According to E. Rogers, the diffusion rate of innovation depends on five factors
at the stage of decision making on the use of innovation:
• Relative advantage - innovation is perceived as an improved version of the
traditional alternative;
• Compatibility - the level of perception of innovation in the existing system
of consumer values based on cultural differences, experience, demographic
indicators (level of education, gender, age) and present needs;
• Complexity - the complexity of learning and the use of innovation;
• Simplicity of testing - the ability to divide innovation into parts and conduct a
consumer test of a separate part or reduced model;
• Communicative - the possibility of distributing innovations among consumers
through communication.
2.3 Conclusion
During the research for a relevant SST, you need to analyze the popularity of the
selected technology in the market under investigation. This indicator is essential for
the company at the stage of integrating the SST to search for software and additional
equipment, and the level of consumer awareness in the chosen technology allows the
company to reduce the cost of training for the use of SST. It is also essential to inform
about the benefits to the consumer when using the SST, to provide a test version and
training the staff in the early days.
5
Chapter 3
Existing Solutions
3.1 RFID
Today grocery retailers use bar codes that denote products. This technology has
greatly simplified the system of product identification and accounting. They are
very cheap, but they have disadvantages: insufficient memory and inability to re-
program. The best solution for data transfer is a microprocessor smart card, which
allows you to place the chip in a plastic card for further interaction with the reader.
However, mechanical contact is not appropriate in the case of TC. Contactless data
transmission between the device and the reader is more flexible. Technology that
implements this procedure is called RFID.
As with any new technology, there are challenging and opportunities associated
with RFID technology. Some of the major challenges in implementing this technol-
ogy include its unreliability in the retail environment, readability range, readability
accuracy, heterogeneous standards, costs and problems of processing. Despite all
challenges, RFID is a promising technology that can be used in a variety of ways:
supply management, temperature monitoring and food safety in the food industry.
Using RFID technology can increase efficiency and productivity by providing better
inventory to reduce food spoilage. Integration of RFID tags with sensors can pro-
vide food processors with a means of controlling the temperature or quality of food
products. Establishing common standards and the cost-effective implementation of
this technology can lead to widespread use of RFID in the food industry. (Bose et al.,
2009)
3.2 Mobile solutions
Using this solution, the user scans the product with the help of a mobile phone dur-
ing the purchase selecting process. With a mobile phone, the user can scan products
and put them in a virtual basket. During the payment process, the user may be
offered to bring the phone to the reader and pay with additional software, or add
a bank card to the mobile application and pay from a mobile phone. Conclusions.
With the help of this solution, the capacity of the shop increases substantially, as
there is no need to outline the goods on the cash register.
3.3 Another self-service equipment
The self-service cashier assumes scanning and payment of the goods without the
intervention of the shop staff. One of the solutions is cash register equipment con-
trolling weights, checking the pressure of goods. Weights compare the actual weight
of the purchase with the weight of all products pre-entered into the database. There

6 Chapter 3. Existing Solutions
are also examples of introducing RFID technology in conjunction with self-service
cash desks. Such cash desks have unique places for messaging with products and
devices for reading RFID tags that are on these products. In this way, reading the
labels from all the products takes place in seconds.
Characteristics of tech-
nology
RFID Bar code Qr code
The need for a label in
direct visibility
Reading even
hidden tags
Reading without
direct visibility is
not possible
Reading without
direct visibility is
not possible
The amount of memory From 10 to
512,000 bytes
Up to 100 bytes Up to 3,072 bytes
Ability to overwrite
data and reuse
Possible Impossible Impossible
Reading range Up to 100 m Up to 4 m Up to 1 m
Simultaneous identifi-
cation of several objects
Up to 200 labels
per second
Impossible Depends on the
reader
Resistance to the envi-
ronment: mechanical,
temperature, moisture
Increased dura-
bility and resis-
tance
Depends on ma-
terial to be ap-
plied
Depends on ma-
terial to be ap-
plied
The expiration date of
the label
More than 10
years
Depends on
printing method
and material
Depends on
printing method
and material
Security and counter-
feit protection
Possible, but not
simple
Felt easily Felt easily
Damaged label work Impossible Complicated Complicated
Identification of objects
in motion
Possible Complicated Complicated
Propensity to interfer-
ence in the form of elec-
tromagnetic fields
Possible Impossible Impossible
Dimension (size) Medium and
small
Small Small
Price Medium and
high
Low Low
Independent manufac-
turing
Impossible Possible Possible
TABLE 3.1: Comparative analysis: RFID - Bar code - QR code.
7
Chapter 4
The proposed solution
The proposed solution is a combination of several existing solutions, namely, the
concept of "mobile shopping", RFID technology and traditional access control sys-
tems (turnstiles and anti-theft gate). The presence of a mobile phone with a high-
quality camera is required. The presence of a mobile application on the phone is
needed. User Journey-stages:
• Registration;
• Exit;
• Adding a product to the grocery basket;
• Payment;
• Entrance.
4.1 Registration
Pre-registration of a potential Automated convenience store user is required to re-
duce the risk of penetration into the shop of thieves or other suspicious persons who
may cause material or reputational harm to Automated convenience store. Registra-
tion is a necessary step to enter the store. When registering, the buyer must indicate:
Mobile phone (verified by entering into the application code with SMS); Personal
data: name, surname, date of birth, city (verified by writing off and returning 1
UAH from the bank card account); Bank Card number, CVV code, expiration date);
The user may be refused for registration and creating a personal profile wherefore
the user can be refused within the permission to enter the store. In the case of com-
pleting the registration, the user obtains the appropriate % of the trust.
4.2 Exit
While entering the store, the user should open the application. The application gen-
erates a unique secret key that is transmitted from the user’s application in Mace
Reader in the form of a QR-code or transmitted through the Bluetooth connection
protocol. After the successful opening of the session, the authorized user passes
through the turnstile.
4.3 Add a product to the grocery basket
Adding a product to the grocery basket can be done by scanning the QR code for the
QR reader in the mobile application.

8 Chapter 4. The proposed solution
4.4 Payment
The payment is made using a mobile application. Registration guarantees at least
one bank card in the application. Optionally, the user can add another bank card.
4.5 Entrance
On the Output, the system must identify the user account and close the session. So
we know who goes out of the store. The process is carried out with the following
verification. The application shows a unique secret key that is transmitted from the
user’s application in Mace Reader in the form of a QR-code or transmitted via the
Bluetooth connection protocol. After a successful closing session, an authorized user
passes through the turnstile and Anti-theft Shop System ("frame").
4.6 Additionally
The responsible person could select the products of the higher class and some of the
goods which could be marked with RFID tags. After passing the identification on
the output, the system knows the list of paid goods, which may include products
with RFID tags. Accordingly, if the frame sees a product that has an RFID tag, and
there is no product affixed to this RFID tag in the list of paid goods, an alarm will
trigger. After successful passing of the Buyer, who has an RFID-tagged product in
the list of paid purchases, the system finds the goods on the unique id RFID-tag and
deactivates its operation.
4.7 Trust system
4.7.1 Bank of court decisions
It is advisable to conduct a preliminary registration, without which buyers can not
enter the store. It could reduce the risk of penetration of thieves or other suspicious
persons into the store.
In most countries (including Ukraine:State Register of Court Decisions), there
are open registries of court cases, through which it is possible to obtain information
about court decisions regarding citizens of this country by name, surname, date of
birth, etc. It is worth to understand that there are different types of proceedings:
• Criminal
• In cases of an administrative offense
• Civilian
• Household
• Administrative
• Constitutional [5]
According to the type of offense, it is advisable to make your system for assessing the
potential danger from the buyer’s side for the store. Having information about past
violations of the buyer’s store may refuse the buyer in the registration or inform

4.7. Trust system 9
the security guard after passing through the identification at the entrance that the
dangerous buyer is in the store.
Let’s consider an example Obtaining public information about a person, for her
name: presence in search of the Ministry of Internal Affairs, the presence of the party
defendant in the case in administrative, criminal and economic processes (since
February 2016), the presence of debtors on alimony.
API used: OpenDataBot API
Information about the person: "Ткаченко Катерина Володимирiвна"
1 import j so n
2
3 name = input ( )
4
5 key = "MwMPpuQ6hW" # temperary API key
6
7 resp = r e qu e sts . g et ( " ht t ps :// opendatabot . com/a pi/v2/
8 person ? apiKey= " + key + "&pib=" +name )
9
10 data = res p . j s on ( )
11
12 wanted = ’W’
13 s e s s i o n s = ’S ’
14 corru pt = ’C ’
15
16 # pa rser
17 def f il te r_ by _n am e ( received_name ) :
18 i f name in received_name :
19 r et ur n True
20
21 def p ar se r ( data , i d e n t i f i c a t o r ) :
22 d a t a _ l i s t = [ ]
23 f o r item in range ( 0 , le n ( data ) ) :
24 val ues = l i s t ( data [ item ] . v alue s ( ) )
25 person_name = find_name ( values , i d e n t i f i c a t o r )
26 i f filte r_ by _n am e ( person_name ) :
27 t r = t r u s t _ c o u n t e r ( va lues [ 1 ] , i d e n t i f i c a t o r )
28 d a t a _ l i s t . append ( va lues )
29 d a t a _ l i s t . append ( t r )
30 ret u rn d a t a _ l i s t
31
32 def find_name ( data , i d e n t i f i c a t o r ) :
33 i f i d e n t i f i c a t o r == wanted or i d e n t i f i c a t o r == c orr up t :
34 person_name = data [ 1 ]
35 e l i f i d e n t i f i c a t o r == s e s s i o n s :
36 involved = data [ 3 ] . s p l i t ( ’ , ’ )
37 person_name = involved [ 1 ] . s p l i t ( ’ : ’ ) [ 1 ]
38 e l s e :
39 person_name = [ ]
40 ret u rn person_name
41
42 def trus t_by_form a ( forma ) :
43 # add yours custom co unter
44 ret u rn counter
45
46 def t r u s t _ b y _ i d e n t i f i c a t o r ( i d e n t i f i c a t o r ) :
47 counter = 0
48 i f i d e n t i f i c a t o r == wanted or i d e n t i f i c a t o r == co rr upt :
49 coun ter += 100
50 r et ur n co unter
51
52 def t r u s t _ count e r ( forma , i d e n t i f i c a t o r ) :
53 r et ur n trust_ by_fo rma ( forma ) + t r u s t _ b y _ i d e n t i f i c a t o r ( i d e n t i f i c a t o r )

10 Chapter 4. The proposed solution
54
55 def w r i t e _ f i l e ( i d e n t i f i c a t o r , out_data , f i l e ) :
56 f i l e . w ri te ( i )
57 f i l e . w ri te ( s t r ( out_data ) )
58 f i l e . w ri te ( "\n " )
59
60
61 i f __name__ == ’ __main__ ’ :
62 main ( )
LISTING 4.1: Python example
As a result, we will get a document with user information:
wanted[[’43336870’, ’Ткаченко Катерина Володимирiвна’, ’02.04.1983’, ’13.05.2014’,
’female’, ’СТ.408 Ч.1’, ”, ’ГОЛОВНЕ УПРАВЛIННЯ НАЦIОНАЛЬНОЇ ПОЛIЦIЇ
В АВТОНОМНIЙ РЕСПУБЛIЦI КРИМ ТА М. СЕВАСТОПОЛI’, ’лицо, скрывающееся
от органов прокуратуры’, ’не застосовувався, ’, ’В розшуку з 13.05.2014’, ’1’], 100]
sessions[[’Степаненко О.М.’, ’Цивiльнi справи’, ’711/2512/17’, ’Позивач: Пiдгорецький
Євген Валентинович , вiдповiдач: Ткаченко Катерина Володимирiвна’, ’про розiрвання
шлюбу ’, ’2017-05-16 12:00:00’, ’active’], 0]
4.7.2 Receiving personal data
The user audit is conducting in the judicial decision database. Before the review, it is
necessary to obtain personal data of the user. With the help of this data, the system
will create a request for the judicial decision database. These data can be obtained by
adding fields at registration form: name, surname, city, date of birth. But there is a
risk that the user can make incorrect data in error or knowingly. To minimize the risk
and increase the quality of the user experience of using a mobile app, you can apply
the practice of Authorization hold. The authorization hold or pre-authorization is
a practice of checking electronic transactions initiated by a debit or credit card and
keeping that transaction inaccessible at check-in. The main reason for using such
a practice is that there is a two-step process in the payment process, consisting of
permission and settlement with the time lag between them. For example, this system
uses hotels that can freeze the amount on the card and pay after. In our case, the
amount of the transaction will change to the time of calculation. Accordingly, we can
make a flat-rate check, for example, 1 dollar, to make sure the card is legal and that
the customer has the funds. With this check, you can also get personal information
about the user (name and surname).
4.7.3 Questionnaire
To ensure that the shop is visited only by honest buyers, it is also possible to use
the practice of banks in lending, namely, classic scoring. This model allows you to
understand how much a person in the future may be able to repay the lending and
its potential risk to the store. Built on socio-demographic parameters of the buyer,
such as age, gender, education, seniority, time of residence in the region.
4.8 Economic feasibility
In order to determine the appropriate equipment it is necessary to calculate the prof-
itability of the implementation of innovation. Determining the main economic indi-
cators will help you find out if the company is benefiting from the introduction of
innovations.

4.8. Economic feasibility 11
To date, more than a half of thefts in stores are held with the participation of
shop staff. Regard this, in store without staff, the higher profitability of the store is
forecasted.
Also, with the removal of cash from the store room there is free space for the
layout of an additional range of goods compared with the traditional store. Which
leads to:
• Reducing the markup on the product, by reducing the cost of the store
• Wider assortment
• Increase the average check
4.8.1 Mathematical model
Description of the mathematical model. A comparative mathematical model was
made to compare important parameters between the Automated Convenience Store
and the Traditional Shop.
Standard conventions. We consider that all the parameters in two types of stores
are the same, except those that are compared. They are irrelevant, and we do not
consider them into details due to the uselessness (see Table TABLE 5.1: Assumption
of financial model). We consider that the two stores that were analyzed are in the
same places on the streams of potential buyers, have the same area, the same range,
the equal payments for rent, communal, electricity, etc.
It is also significant that, in comparison, the difference is not only the difference
between a single ordinary store and a single Automated Convenience Store and a
comparison of the networks of such stores.

12 Chapter 4. The proposed solution
Name Automated Conve-
nience Store
Traditional Store
Average check: $ 4 $ 3,7
Number of customers (DAY): 100 100
Average salary for shop em-
ployees (MONTH):
$ 296 $ 296
Average salary for develop-
ers (MONTH):
$ 3000 -
Time for application develop-
ment (WEEKS):
16 -
Employment at the time of
application development:
6 employees -
• IOS developer 1
• Android developer 1
• Backend developer 1
• Tester 1
• Embedded developer 0.5
• Project Manager 0.5
• Designer 0.5
• Devops engineer 0.5
Employment at the time of
work of the store:
5.5 employees 8 employees
• Technical support 0.5 0.5
• Cleaner 0.5 0.5
• Warehouse commissar 0.5 0.5
• Accountant 0.5 0.5
• Marketer 0.5 0.5
• Call Center Operator 1 1
• Merchandiser 1 1
• Guardian 1 1
• Cashier - 3
TABLE 4.1: Assumption of financial model

4.8. Economic feasibility 13
TABLES 5.2 and 5.3 compare amounts that the owner should spend for goods
and/or services that will be used for more than one year.
Name Price per item Number of items Total sum
Fiscal registrar $370 3 $1,111
ash register $259 3 $778
Cash boxes $37 3 $111
POS terminal $556 3 $1,667
Cashier’s box $1,037 3 $3,111
Barcode scanner $111 3 $333
Customer display $100 3 $300
Total sum $7,411
TABLE 4.2: CAPEX: 1st Traditional Store
Name Price per item Number of items Total sum
Application $15,360 1 $15,360
Security system $6,698 1 $6,698
Turnstile $1,481 2 $2,962
Total sum $25,021
TABLE 4.3: CAPEX: 1st Automated convenience store
4.8.2 Net profit
Net profit shows the number of earnings for the store for a year. It is measured in
money.
Per YEAR, USD Automated Conve-
nience Store
Traditional Store
Revenue $ 146,667 $ 133,333
Trade margin, percentage 5 % 5 %
Net profit $ 7,333 $ 6,667
Employees - $ 1,630 -$ 2,370
Profit $ 5,704 $ 4,296
TABLE 4.4: Net Profit: Comparison between Automated Conve-
nience Store and Traditional Shop
4.8.3 Payback period
The payback period is inversely proportional to the IRR. Measured in time - year,
month. Shows the period for which the project earns the capital invested in it. Or
this is the period from the date of capital investment to the time of the return of that
capital through profit.

14 Chapter 4. The proposed solution
Per YEAR, USD Automated Convenience
Store
Traditional Store
Investments $25,021 $7,411
Payback 4,3 1,7
TABLE 4.5: Payback period: Comparison between Automated Con-
venience Store and Traditional Shop
4.8.4 IRR
IRR - The rate of return on investment, measured in percentages per annum, shows
the percentage of income earned by an investment per year. It is inversely propor-
tional to the payback period. 1 / IRR = payback period or 1 / payback period = IRR
Per YEAR, USD Automated Convenience
Store
Traditional Store
IRR 22.80 % 57.97 %
TABLE 4.6: IRR: Comparison between Automated Convenience Store
and Traditional Shop
4.8.5 NPV
NPV is the current value of the investment for the period. The calculation formula
takes into account:
• The initial investment in money
• The domestic interest rate of discounting which takes into account inflation or
the alternative internal cost of money
• Dimension % per annum. (10% per annum)
• Investment horizon - the period in years for which the NPV is calculated in the
model (5 years)
The fate of the project on a distant horizon may be the liquidation or sale of a busi-
ness. And our model of business sales on the far horizon for the cost of 5-year profits.
(Market value of the business in Ukraine). The NPV is measured in cash and shows
how indicated the method of investing is better than the baseline (we have 10%).

4.8. Economic feasibility 15
Per YEAR, USD Automated Con-
venience Store
Traditional Store
NPV 10%, 5 YEARS & SOLD
0 YEAR -$ 25,021 -$ 7,111
1 YEAR $5,704 $4,296
2 YEAR $5,704 $4,296
3 YEAR $5,704 $4,296
4 YEAR $5,704 $4,296
5 YEAR $5,704 $4,296
SELL COSTS $ 22,815 $ 17,185
TABLE 4.7: NPV : Comparison between Automated Convenience
Store and Traditional Shop
4.8.6 Conclusion
Taking into account assumptions, we can make conclusions that there is no economic
feasibility to open one Automated Convenience Store in comparison with the Tradi-
tional Shop. The most significant factor in our business mathematical model is the
shift from comparing single stores to network comparisons. Already with the num-
ber of stores in the network larger than 10, the apparent advantage of the store is the
trust in the traditional model. With an increase in the number of stores, the benefit
of the new over the old-fashioned is becoming more and more evident.
TABLES 5.8 and 5.9 compare amounts that the owner should spend for goods
and/or services that will be used for more than one year.
Name Price per item Number of items Total sum
Fiscal registrar $370 3 $1,111
ash register $259 3 $778
Cash boxes $37 3 $111
POS terminal $556 3 $1,667
Cashier’s box $1,037 3 $3,111
Barcode scanner $111 3 $333
Customer display $100 3 $300
Total sum $7,411
TABLE 4.8: CAPEX: N Traditional Store
Name Price per item Number of items Total sum
Turnstile $1,481 2 $2,962
Total sum $2,962
TABLE 4.9: CAPEX: N Automated convenience store
As you can see, the cost of opening each subsequent Traditional Store is equal
to the opening price of the first store of this type.In the opening of a Automated
convenience store, costs will be significantly reduced.
The result of the investigation and the building the financial model shows us that
creating Automated Convenience Store has no economic feasibility. If we are sure
that we are doing a chain of stores - Automated Convenience Store is one of the best
solutions in innovations and food retail automatization (see Tables 5.10 and 5.11).

16 Chapter 4. The proposed solution
Per YEAR, USD Automated Conve-
nience Store
Traditional Store
Revenue $ 1,466,6677 $1,333,333
Trade margin, percentage 5 % 5 %
Net profit $73,333 $66,667
Employees - $16,296 -$ 23,704
Profit $ 57,037 $42,963
TABLE 4.10: Net Profit for 10 shops: Comparison between Auto-
mated Convenience Store and Traditional Shop
Per YEAR, USD Automated Convenience
Store
Traditional Store
Investments $54,651 $81,522
Payback 0,04 1,9
TABLE 4.11: Payback period for 10 shops: Comparison between Au-
tomated Convenience Store and Traditional Shop
4.9 Additionally
4.9.1 Equip several traditional cash desks
The development of new technology can cause stress to buyers, therefore the store
should be equipped with several cashiers with traditional cashiers. This will allow
the store not to lose customers who do not have cashless money, with a low battery
in the phone, in a hurry, etc.
4.9.2 Staff Assistance
At first, buyers may have difficulty studying new technology, so it is advisable to
consider training and customer support by shop staff.
4.9.3 Increasing the effectiveness of surveillance cameras
According to statistics, 73 percentage of the thieves do not plan to steal something in
advance. The buyer is stealing when he sees the opportunity to take something left
unnoticed. To increase the effectiveness of surveillance cameras, you can set a screen
with a broadcast from the surveillance cameras or set the camera at the entrance to
the store in a prominent place to indicate that the person is being monitored. You
can also add personalization items after scanning a QR code at the entrance, which
may also be helpful in pushing the idea of getting something for free.
4.9.4 Loyalty program
Having extensive marketing information about a group of buyers, you can sell it
further. Getting information from the buyer’s receipt can learn about his habits and
tastes. In the future, the buyer offers goods of related categories with targeted dis-
counts. For example, when purchasing information on cigarettes, the buyer can offer
goods in this category with a discount (alternatives to tobacco products).

4.10. Requirements 17
4.10 Requirements
Feature model Diagram - the high-level forward design diagram (drawing before
coding the application) providing in the software features.
FIGURE 4.1: Feature model Diagram
User Story is a short description of a software feature from an end-user perspec-
tive which is focused on the aim or result which the feature will provide to the user.
A User Story template often uses the following type of format: As a <role>, I want
<feature> so that <reason>.
Usually, User Story is she is paired with Acceptance Criteria. They are the con-
ditions that a software product must satisfy to be accepted by system level function-
ality. User Story is present with the help of the flowchart. The flowchart is a block
diagram is a common type of schemes describing algorithms or processes in which
individual steps are depicted as blocks of various shapes.

18 Chapter 4. The proposed solution
4.10.1 Registration
As a User I want to be able to register so that I have access to the application content.
The system registers the user by phone number, a third party must send a confirma-
tion code, the user enters the code, and the system determines the correctness of the
code match and confirms the possession of the person by this phone number. The
user must create and confirm a password. User must add at least one credit card.The
system should send a request for withdrawal of 1 UAH to check the account status
and validity of card data. When adding a new card and personal information, the
system determines the name and surname and requests the base of court decisions.
When detecting artillery damage, the user account is blocked. The phone is entered
in the ban.
FIGURE 4.2: Flowchart: Registration

4.10. Requirements 19
4.10.2 Login
As a User I want to be able to log into app so that I have access to the application
content.The system should authenticate the user when he log in using his password
and phone number.
in.png in.png in.png
FIGURE 4.3: Flowchart: Log in
4.10.3 Profile update
As a User, I want to be able to update my personal information so that it is going to
be up to date. The system should provide the possibility to update information.
FIGURE 4.4: Flowchart: Profile update
20 Chapter 4. The proposed solution
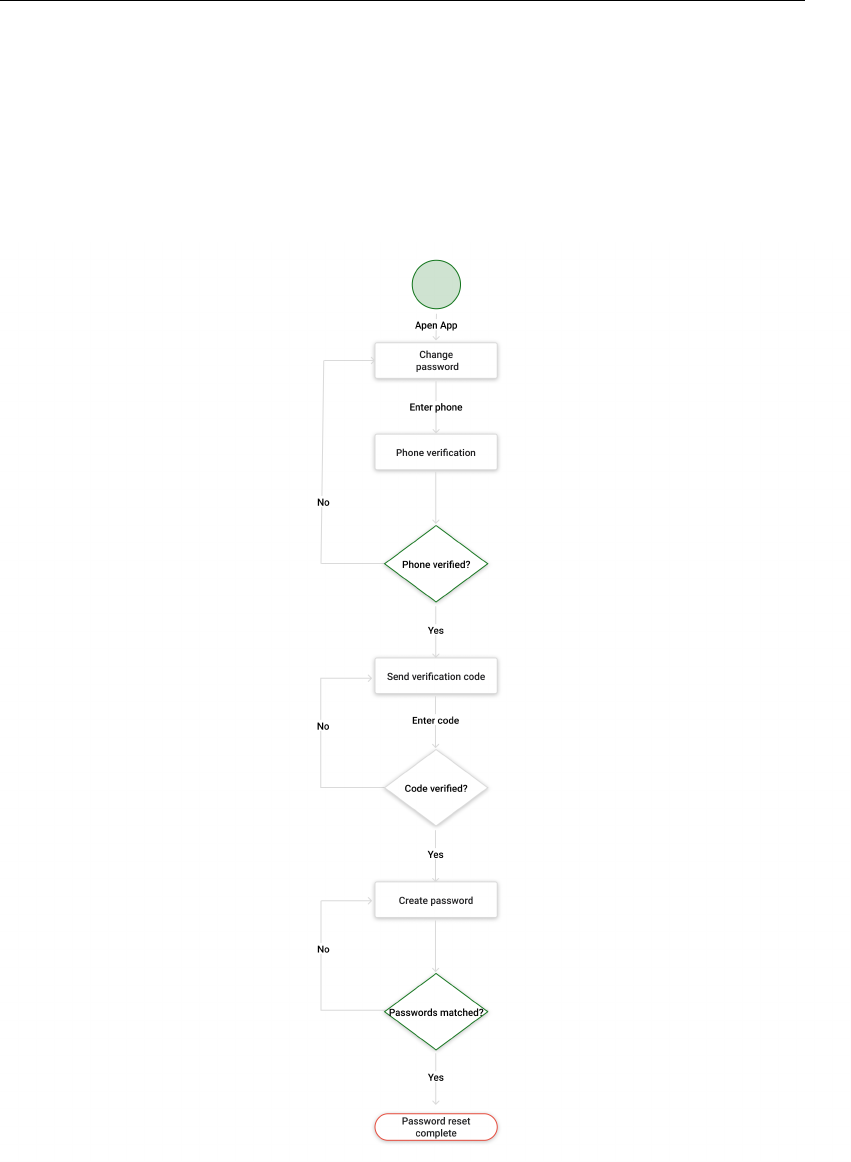
4.10.4 Password reset
As a User I want to be able to recover my password.The system provides the possi-
bility to change password by phone number, a third party must send a confirmation
code, the user enters the code, and the system determines the correctness of the code
match and confirms the possession of the person by this phone number. The user
must create and confirm a password.
FIGURE 4.5: Flowchart: Password reset

4.10. Requirements 21
4.10.5 Add credit card
As a User I want to be able to add several payment cards so that I can pay by one
of them for purchases.The system should provide the possibility to enter the: card
number, CVV code, date. The system should send a request for withdrawal of 1
UAH to check the account status and validity of card data. When adding a new
card, the system determines the name and surname and requests the base of court
decisions. When detecting artillery damage, the user account is blocked. The phone
is entered in the ban.
FIGURE 4.6: Flowchart: Add credit card

22 Chapter 4. The proposed solution
4.10.6 History
[h] As a User I want to be able to observe information of my completed orders so
that I see all completed orders details sorted from newest to oldest one. The system
should provide a possibility to observe the list of orders.
FIGURE 4.7: Flowchart: History

4.10. Requirements 23
4.10.7 Shopping
As an User I want to be able to enter the store using my phone and an app Using an
app after authentication user can enter the store through scanning QR-code by mace
reader As a User I want to be able to use the scanner so that I can scan the QR code
of the purchases via application so that I can observe the added items in the list of
purchases. System should provide the possibility to delete items from the list. As a
User I want to be able to pay for the purchases with desired payment card so that I
can choose the payment card from the list of added credit cards.The system should
provide a possibility to choose the payment card before the withdrawal of payment.
As an User I want to be able to exit the store using my phone and an app.Using an
app after authentication user can enter the store through scanning QR-code by mace
reader.
FIGURE 4.8: Flowchart: Shopping

24 Chapter 4. The proposed solution
4.11 Low fidelity prototypes
FIGURE 4.9: UserFlow: Login

4.11. Low fidelity prototypes 25
FIGURE 4.10: UserFlow: Menu

26 Chapter 4. The proposed solution
FIGURE 4.11: UserFlow: Register

4.11. Low fidelity prototypes 27
FIGURE 4.12: UserFlow: Shop
29
Bibliography
Bose, Indranil et al. (2009). “Managing RFID projects in organizations”. In: European
Journal of Information Systems 18.6, pp. 534–540.
Curran, James M, Matthew L Meuter, and Carol F Surprenant (2003). “Intentions
to use self-service technologies: a confluence of multiple attitudes”. In: Journal of
Service Research 5.3, pp. 209–224.
Davidson, William R, Albert D Bates, and Stephen J Bass (2002). “The retail life cy-
cle”. In: Retailing: The evolution and development of retailing 55.6, pp. 89–96.
Finkenzeller, Klaus (2010). RFID handbook: fundamentals and applications in contactless
smart cards, radio frequency identification and near-field communication. John Wiley
& Sons.
Ivanov, Gennady and Elena Mayorova (2015). “Intangible assets and competitive
advantage in retail: case study from Russia”. In: Asian Social Science 11.12, p. 38.
Jones, Peter et al. (2005). “Radio frequency identification and food retailing in the
UK”. In: British Food Journal 107.6, pp. 356–360.
Rogers, E.M. (1995). “Elements of diffusion”. In: Diffusion of innovations, pp. 1–37.

