
Wildcard and SAN:
Understanding Multi-Use
SSL Certicates
LEVERAGING MULTI-USE DIGITAL CERTIFICATES TO SIMPLIFY CERTIFICATE
MANAGEMENT AND REDUCE COSTS

2
Wildcard and SAN: Understanding
Multi-Use SSL Certicates
W
hen you employ web-based services on the Internet, SSL
certicates are the industry standard for authentication
and security. Depending on how you plan to use SSL certicates,
multi-use certicates can provide greater exibility than traditional
certicates. Multi-use certicates protect multiple Fully Qualied
Domain Names (FQDNs) and subdomains, lowering your
administrative costs and simplifying certicate installation,
management, and deployment.
About Digital Certicates
The best way to prove your identity on the Internet is to use
a digital certicate. A digital certicate relies on a trusted
third-party authority, or Certicate Authority, to verify your identity
and then uses a chain of trust that begins with you and works up
to the trusted authority to validate your identity. This chain of
trust provides veriable security on the internet. Digital
certicates provide:
PROOF OF AUTHENTICITY
Digital certicates demonstrate and validate the authenticity of
the source of the web content.
INTEGRITY
Digital certicates make it difcult to modify content in transit
because the content is encrypted.
AVAILABILITY
Digital certicates enable the availability of secure information
exchange online. By providing a constant verication service,
Certicate Authorities identify bad risks for certicates and
mitigate those risks through a series of lists and checks.
CONFIDENTIALITY
SSL encrypts data both in the content itself and in the transport
mechanism that is used to send the data to a destination on the
Internet, ensuring condentiality.
A SSL trust mark or site seal lets your customers know
that a Certicate Authority has authenticated and
veried your organization.
Using SSL to Move HTTPS
Organizations that process transactions on the Internet, or offer
Internet-based services, rely on digital certicates to validate that
they are who they claim to be, ensuring trust in their services.
Most organizations add certicates to their Internet-facing servers
to ensure accurate proof of their identity.
2005-00-00
SECURED
BY
2012-00-00
When a customer accesses a web page that is hosted on a
server with a digital certicate, their web browser automatically
detects the certicate and modies the session. The session
moves from an “open” session that uses Hypertext Transfer
Protocol (HTTP) to a secure HTTP (HTTPS). HTTPS allows for
the encryption of all the data sent between the user’s computer
and the server.
Secure Sockets Layer
Secure Socket Layer (SSL) provides HTTPS data encryption.
SSL creates an encryption tunnel between the client and the
server that protects the transfer of data from one point to the
other during the communication exchange. You know you are
using SSL when the web address starts with https:, and your
browser displays a closed padlock in its status bar, and/or you
see a green background in the address bar. Note that the green
background in the address bar and the padlock are hallmarks of
an Extended Validation (EV) SSL certicate. Extended Validation
certicates provides the highest level of authentication available
for a SSL certicate. Because EV SSL authentication standards
require strict issuance and management processes established
by the CA/Browser Forum, EV SSL Certicates provide an extra
layer of protection for online businesses and their customers.
3
Protecting Servers and Services with
SSL Certicates
To enable SSL on an externally facing server, an organization
must purchase a certicate from a trusted Certication Authority
(CA). The organization purchases one certicate for each service
that it plans to protect (e.g. email, instant messaging, mobile
device management, and web-based interactions).
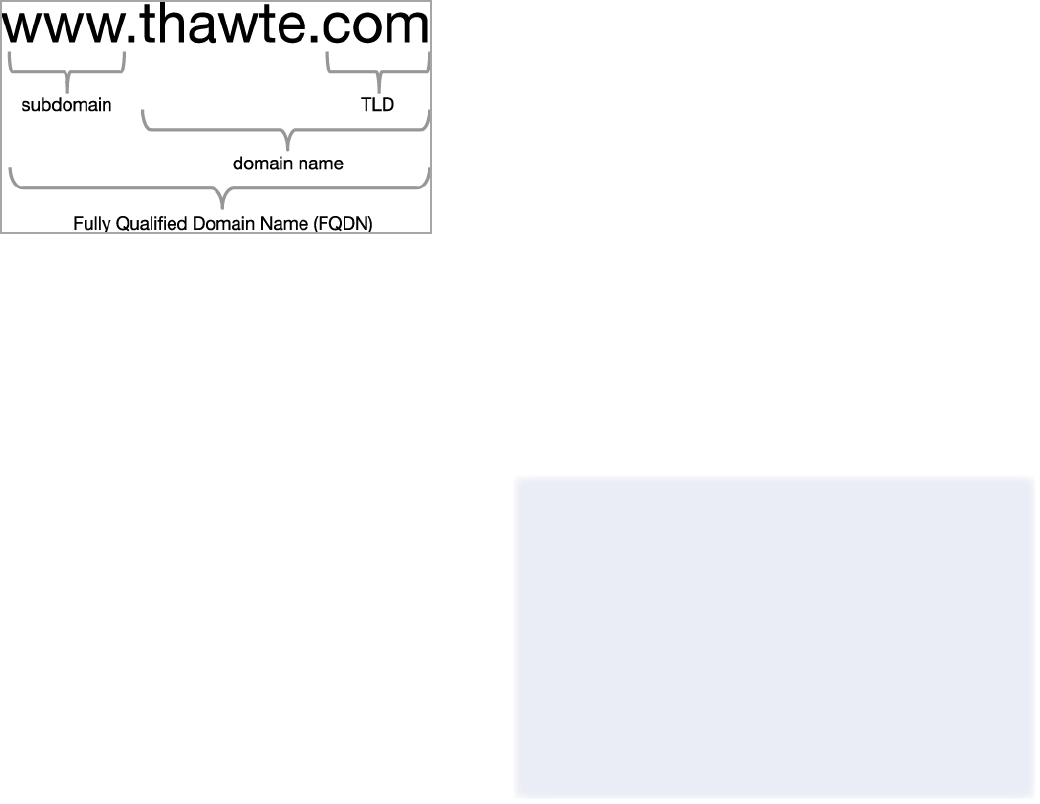
An SSL certicate contains the service’s Fully Qualied Domain
Name (FQDN) and ties a service’s domain name to the server.
This combination makes it possible for a browser (or another
agent) to compare the domain name that the service accesses
with the domain name of the certicate.
Maintaining SSL Certicates
Certicates last for a nite period of time: typically one, two,
or three year periods. To avoid maintenance every year, it
is recommended you purchase certicates that are valid for
extended periods of time.
It’s also convenient to select static service names because each
time a service name changes, the certicate must change on
each server that provides the service. These strategies reduce
the workload associated with periodic renewal and installation of
certicates on your servers.
Services that use subdomain names (names that use the
same root, or domain name, but have a different prex, or
subdomain name) have an additional maintenance overhead.
Because subdomain names are embedded into SSL certicates,
organizations usually buy one certicate per service. If the
organization protects numerous services with unique certicates,
this can become expensive and timeconsuming to manage.
Types of Multi-Use SSL Certicates
Two types of multi-use SSL certicates can greatly reduce the
complexity of managing SSL for services and subdomains.
• A Wildcard Certicate allows you to secure multiple
subdomains under a single unique FQDN. Using
one wildcard certicate not only simplies certicate
management, but also lowers your administrative costs
while providing immediate protection to current and
future subdomains.
• A single Subject Alternative Name (SAN) Certicate can
secure multiple FQDNs. SAN certicates provide exibility
when your websites do not share the same domain name.
Unlike Wildcard Certicates, SAN certicates have the
additional benet of being able to support deployments that
require Extended Validation (EV) certicates.
Wildcard Certicates
Wildcard certicates are regular SSL Certicates that support
the wildcard character “
*
” as a prex to the FQDN, allowing it
to secure multiple services. Wildcard certicates do not include
specic service names and always contain a wildcard character
that prexes the domain name.
A wildcard certicate can be more exible than using multiple
single purpose certicates because you can apply the wildcard
certicate to a number of different services. You can also add,
change, or replace services without needing to update the
certicate or purchase new certicates.
A single wildcard certicate–like *.thawte.com–can
secure the following domains:
www.thawte.com
nance.thawte.com
mail.thawte.com
sip.thawte.com
register.thawte.com
However, it cannot secure:
www.thawte.ca
mail.test.thawte.com

4
For example, suppose you want to protect servers that run an
instant communication protocol like Session Initiation Protocol
(SIP) and an email service. With single-use certicates, you
need two certicates because you have to embed the name of
each service into each certicate. As long as the domain is the
same, however, you can secure both domains with one wildcard
certicate. So the wildcard *.thawte.com can secure both sip.
thawte.com and mail.thawte. com with just one certicate.
Using a wildcard character as a placeholder in the domain
name embedded into the certicate makes the certicate more
exible. You can also apply it to any number of services since
the wildcard character can represent any subdomain name,
simplifying the certicate management process.
Because wildcard certicates manage multiple subdomains and
the services names they support, they can be less secure than
SAN certicates. We do not recommend their use as the primary
certicate solution for enterprises. When you deploy a wildcard
certicate, always make sure that you implement strong logical
and physical policies to protect your assets.
Subject Alternative Name (SAN) Certicates
Subject Alternative Name (SAN) certicates enable you to include
multiple FQDNs in one certicate. Unlike wildcard certicates that
can support an unlimited number of prex or subdomain names
as long as the domain name remains the same, SAN certicates
only support the FQDNs entered into the certicate. Depending
on the issuing Certicate Authority, SAN certicates can support
100 or more different FQDNs in one certicate.
A SAN certicate includes the standard Subject Name eld,
which supports a single primary web-based service name. The
subject name is what the certicate secures, as listed in the
example below in the component elds. It consists of a Common
Name, Organization, Organizational Unit, Locality, State, and
Country. It has an additional eld–the Subject Alternative Name
(SAN) eld–for additional service names. You can install a SAN
certicate on several servers, where it supports internal and
external service delivery.
SAN EXAMPLE
One SAN certicate can protect:
yourbusiness.co.uk
mybusiness.com
yourbusiness.net
products.yourbusiness.com
support.products
yourbusiness.com
Subject Alternative Name (SAN) certicates are also called Unied
Communications Certicates (UCC) because they were primarily
designed to support real-time communications infrastructures.
SAN certicates, or UCCs, are useful when organizations want to
use different root or domain names to run Internet-facing services.
For example, an organization that provides internal (sip.thawte.
net) and external domain (sip.thawte.com) unied communications
services can use a single SAN certicate to secure both FQDNs.
The organization would need two wildcard certicates because
thawte.net and thawte.com are different domains.
Another way to use a SAN certicate is when you validate secure
internal and external services.

5
You might have both an internal and external SIP service for
instant messaging: internal sip.thawte.com and external sip.
thawte.net. In this situation, you must have a certicate on each
server in the internal and external service to allow your users
to work whether they are in the ofce or on the road. The same
scenario applies for instant messaging infrastructures where you
want to encrypt both internal and external messages. Note that
servers cannot include two certicates for the same purpose.
SAN certicates are also useful for Application Service Providers
(ASP) who host applications for multiple clients with each client
using their own domain name. By using a SAN certicate, ASPs
can use a single certicate to support multiple clients. Note that
the site seal and certicate are only for the primary domain name
entered in the certicate and do not include any of the other
domain names. The certicate includes all of the domain names
veried at the time of purchase.
SAN certicates have the same issues as single-purpose
certicates. When the actual service names are embedded into
the certicate, your services must always use the same name
otherwise you have to change the certicate. Because the
certicate is a multi-use certicate, you change it on each of the
servers that host the certicate-supported service. When you
want to add services to provide further functionality to your users,
you must update the SAN certicate with the new service names.
While SAN certicates are useful for supporting unied
communications deployments, keep these caveats in mind:
• SAN certicates do not support wildcard characters.
For this reason, you need to add subdomain names as
unique domain name entries in the certicate at the point
of purchase. Each time you want to add a new domain
name or you remove an old one, you need to update
and re-deploy the certicate to each host server.
• When hosting web sites for multiple clients, ASPs should
be aware that all domain names are visible in a SAN
certicate. If the ASP does not want one site to appear
connected to another, use a different kind of certicate.
Making the Selection
Multi-use certicates can secure multiple web services using
a single certicate. To accomplish this, these certicates either
add a subject alternate name eld to the common single-use
certicate or use a wildcard to replace the subdomain or prex
name in the certicate.
Multi-use certicates save money and simplify management by
including multiple names within the same certicate or replacing
service names with a wildcard. Use SAN certicates when you
need multiple domain names for each service.
WILDCARD CERTIFICATES
Use a wildcard certicate when you want:
• a single domain name for all services
• a single domain and multiple subdomains that cover
all services
SAN CERTIFICATES
Use a SAN certicate when you want:
• unique domain names for each service
• the option of providing Extended Validation protection
In Summary
Most organizations use a least one public domain name and one
private domain name to segregate their internal and external
name spaces. In this case, only SAN certicates work.
For organizations that only use one single public domain name
the wildcard certicate may be a good option.
Multi-use certicates make it much easier to deploy multiple
secure services both internally and externally and have distinct
advantages in lowering costs and reducing resources. This ease
of deployment is particularly useful in environments that include
several services such as mail, instant messaging, web, mobile
device management, and File Transfer Protocol. If this is the
situation that applies for your organization, then your best choice
is a multi-use certicate designed to t your needs.

6
Wildcard vs. SAN Certicates
The following table provides you with an overview of the differences between the SAN and wildcard certicates.
Certicate Feature Wildcard SAN Comment
Multiple secure domain
support
Yes Yes Both certicate types support multiple secure domain names. Wildcard
supports multiple sub domains to one domain, per certicate. SAN-
enabled certicates can support multiple domain names; the limitation is
the number of SANs per certicate established by the CA.
UCC or SAN support Yes Both certicate types support multiple uses.
Microsoft Exchange Server, Microsoft Ofce Communications Server and
Microsoft System Center Mobile Device Manager use SAN.
Number of Fully
Qualied Domain
Names (FQDNs)
1 Multiple Wildcard certicates only support one single domain name, but a
nearly unlimited number of subdomains. SAN-enabled Certicates can
support multiple domains, multiple host names, etc. The limitation is
the amount of SAN’s per certicate. This limitation is established by the
Certication Authority.
Domain name
ownership
1 Multiple An organization must own, or be authorized to use, any and all domains
in the certicate’s subject. The Wildcard product and SAN functionality are
subject to these basic requirements.
Domain name format *.name.com Multiple Wildcard certicates use a single name format (*.name.com). SAN
certicates can use any FQDN.
Name exibility Yes In a Wildcard certicate, only the subdomain can change. Additionally,
a subdomain must exist in place of the wildcard character; for example,
https://*.thawte.com cannot secure https://thawte.com. By contrast, a
certicate for https://www.thawte.com can support a SAN of https://thawte.
com or https://www.thawte.org.
Cost control Yes Wildcards allow for future-proong. You don’t need to buy additional
certicates later as long as you are securing subdomains under
one domain.
Secure private key Yes Yes Both certicate types include a secure private and public key pair.
However, if you use a single wildcard certicate on multiple servers and
one server is compromised, all servers become compromised. For this
reason, each server hosting a wildcard certicate should have its own
version of the certicate with its own private key. The same issue is
possible with SAN certicates. Make sure you keep the private key secure
at all times.
Best PKI practice: Multiple servers sharing one key pair are prone to a
single point of failure. We recommend unique key pairs in multi-server
scenarios, where possible.

7
Certicate Feature Wildcard SAN Comment
Simplicity of
management
Yes Yes Wildcard certicates are easier to manage than SAN certicates because
they support any subdomain. SAN certicates must be updated each time
a new domain is added or an old domain is dropped.
Note that due to the convenient nature of wildcard certicates, you have to
keep careful track of the subdomains that the certicate secures. Keeping
a close record of supported subdomains helps eliminate the chance that a
“rogue” subdomain exists.
Strong physical policy or access control measures to limit who can add/
change/remove host headers are also recommended to eliminate the
possibility of rogue subdomains.
Domain-only
authentication
Because the wildcard certicate supports unlimited subdomains, it is not
available in domain-only format. SAN certicates are also not available in
domain-only format because they include multiple domains.
SHA-1 Yes Yes SHA-1 (a secure hash algorithm) is supported on both types of certicate.
Organizational validated
authentication
Yes Yes Both types of certicate are only available in organizational validated
format, which is more trustworthy than domain-only certicates.
Organizational validated authentication certicates require both domain
validation and organization validation.
SSL encryption Yes Yes Both certicate types support 128-bit and better encryption.
Number of domains
secured
Unlimited
subdomains
Specied
FQDNs
Wildcard certicates validate virtually an unlimited number of subdomains
that are based on the same domain name (though for example, *.thawte.
com does not secure group.test.thawte.com). SAN certicates support
only the domain names entered in the certicate. The number of domains
supported in a SAN certicate depends on the certicate authority.
Extended validation Yes Extended Validation SSL Certicates (EV SSL) instill customer condence
by enabling web browsers to display the green address bar, one of the
most trusted and recognized security indicators available.
Site seal Yes Yes Wildcard site seals are assigned to the domain name. SAN site seals are
assigned to the primary domain name in the certicate.
Mobile device support Yes Yes Note that some older devices, for example, Windows Mobile version 5,
do not support the wildcard character. Check with your vendors to see if
updates are available to support wildcard certicates. All devices support
the SAN certicate.

8
© 2013 Thawte, Inc. All rights reserved. Thawte, the thawte logo, and other trademarks, service marks, and designs are registered or unregistered trademarks
of Thawte, Inc. and its subsidiaries and afliates in the United States and in foreign countries. All other trademarks are property of their respective owners.
Certicate Feature Wildcard SAN Comment
Browser compatibility 99+% 99+% All modern browsers support both types of certicates.
Validity duration Multi-Year Multi-Year Both certicate types are available for multi-year spans.
Warranty Yes Yes Certicate providers can provide warranties for both types of certicates.
Shared hosting usage Yes You can only use SAN certicates for shared hosting because they support
multiple domain names.
Quality assurance
testing usage
Yes Yes Wildcard certicates can only be used in QA testing environments that use
the same domain name. SAN certicates can be used in environments
that use either the same domain name or multiple domain names.
• Via phone
– US toll-free: +1 888 484 2983
– UK: +44 203 450 5486
– South Africa: +27 21 819 2800
– Germany: +49 69 3807 89081
– France: +33 1 57 32 42 68
• Email sales@thawte.com
• Visit our website at
https://www.thawte.com/log-in
To learn more, contact our sales advisors:
Protect your business and translate
trust to your customers with high-
assurance digital certicates from
Thawte, the world’s rst international
specialist in online security. Backed by
a 17-year track record of stability and
reliability, a proven infrastructure, and
world-class customer support, Thawte
is the international partner of choice
for businesses worldwide.
