
Web Security Service
Policy Guide
Revision:NOV.07.2020
Symantec Web Security Service/Page 2
Copyrights
Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom”
refers to Broadcom Inc. and/or its subsidiaries.
Copyright © 2020 Broadcom. All Rights Reserved.
The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com.
Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function,
or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any
liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein,
neither does it convey any license under its patent rights nor the rights of others.
Policy Guide/Page 3

Symantec WSS Policy Guide
The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product,
the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community.
With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to
create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users.
If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four
categories: Phishing, ProxyAvoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the
additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global
allows/denials to individual users at specific times from specific locations.
PDFPart One
The WSS portal provides several policy editors, plus enhancements if you obtain add-on licenses. To familiarize you with how
the WSS evaluates the various policies, the first part of this document presents a policy introduction. Each sections provides a
brief introduction and discusses policy evaluation in the order that the WSS processes web transactions.
PDFPart Two
The remainder of the document expands on policy concepts and policy editors, plus add-on solutions such as Cloud Firewall
Service and CASB. It includes high-level use case examples.
Table Of Contents
Symantec WSS Policy Guide 4
PDFPart One 4
PDFPart Two 4
Table Of Contents 4
WSS High Performance Policy Tuneup—Begin Here 11
Policy Overviews 11
Web Use 11
SSLInterception 12
Location Policy (Authentication) 12
Threat Protection 12
Policy Testing Best Practices 13
WSS Policy Custom Shop 01—Bypass 14
Why Bypass Certain Destinations? 14
Technical Requirements 14
Portal Locations 14
Best Practices 14
Policy Guide/Page 4

Symantec Web Security Service/Page 5
WSS Policy Custom Shop 02—SSLInterception 15
Why Intercept SSLTraffic? 15
Technical Requirements 15
Portal Location 15
Use Case 15
WSS Policy Custom Shop 03—Authentication Exemptions/Locations 18
What is Authentication Exemption? 18
What is LocationPolicy? 19
WSS Policy Custom Shop 04—Content Filtering 21
What is Content Filtering? 21
Technical Requirements 21
Portal Location 21
About the Editor 21
Use Case 22
WSS Policy Custom Shop 05—ThreatProtection 25
What is Content Analysis? 25
Technical Requirements 25
What is Malware Analysis? 25
Technical Requirements 26
About the ThreatProtection Policy Editor 26
About Exemptions 26
WSS Policy Custom Shop 06—RiskScore 28
What is Risk Score? 28
Technical Requirements 28
Portal Location 28
Enhanced Threat Protection Policy Editor 28
Strategic PolicyExample 29
WSS Policy Custom Shop 07—Geolocation 31
What is Geolocation? 31
Technical Requirements 31
Portal Location 31
Enhanced Policy Editors 31
Strategic PolicyExample 32
WSS Policy Custom Shop 08—WebIsolation 33
What is WebIsolation? 33
Technical Requirements 33
Portal Location 33
About the Editor 33
WSS Policy Custom Shop—Roll Out 35
Policy In Review 35
Full Help Topics 35
About Web Security Service Policy 37
About the Traffic Evaluation Order 37
SSL Policy 39
About Scanning Encrypted Traffic 40

Policy Guide/Page 6
Distribute WSS Root Certificate to Endpoints 44
BestPractice—Replacing a Certificate 44
Procedure—Obtain Certificate and Propagate 44
Related Topics 45
Install SSL Root Certificate for Chrome Browsers 46
Install SSL Root Certificate for Mozilla Firefox Browsers 48
Install SSL Root Certificate for Microsoft Internet Explorer Browsers 50
Install SSL Root Certificate for Safari Browsers 51
Create SSL Policy 52
Technical Requirement 52
Procedures 54
Deploy a Self Managed Certificate for SSLInterception 58
About Integrating HSM 58
Frequently Asked Questions 58
Technical Requirements 59
Troubleshoot Dropped SSL Connections 68
Filter Content 69
About Content Filtering 70
Control User Access to Web Content 72
About the Default Policies 72
Step 1—Review the current Content Filtering policies and adjust if necessary. 73
Step 2—After WSS begins processing data, monitor employee web use activity. 73
Step 3—(Optional) Configure an exception page that users see when they browse to a blocked web destination. 73
About the Content Filtering Rule Editor 74
Content Filter Policy Construct 74
AND/OR Constructs 75
Group and Global Rows 75
Group ARules 75
Group B Rules 76
Global Rules 76
Create Custom Content Filtering Rules 78
Construct and Editor Tutorials 78
Activate Policy 84
Exempt URLs from Permanently Blocked Categories 85
Prevent a Domain From Routing to WSS 86
Notes 86
Procedure—Manually Add Domain Entries 86
Import IPAddress Entries From a Saved List 87
Prevent IP/Subnet From Routing to the Web Security Service 88
Notes 88
Procedure—Manually Add IPAddresses 88
Import IPAddress Entries From a Saved List 89
Modify the Default Response Page 90
Procedure 91
Troubleshooting Assistance 93

Symantec Web Security Service/Page 7
Customize the Response Pages 94
Portal Location 94
Use Cases 94
BestPractices 94
The Editor 95
Examples 96
Web Application Policy 99
About Controlling Web Application Access 100
Always Block or Always Allow a Web Application 100
Allow a WebApplication But Block an Action 100
Define Who Can Access WebApplications 101
Web Application Category Reference 102
About the CloudSOC Integration 103
CASBGatelets Topography 103
About the Traffic Evaluation Order 105
Current Limitations 106
Integrate With CloudSOC 107
Technical Requirements 107
Procedure 107
CASB Gatelets Solution Only 108
Delete the CloudSOC Integration 110
Set Default WebApplication Policy toAllow 112
Reference 112
Set Default WebApplication Policy toBlock 114
Reference 114
Define a User-Based Web ApplicationsPolicy 116
Use Case 116
Malware Policy 120
About Malware Scanning 121
BaseLevel 121
Basic Level Protection 122
Malware Analysis Standard Service 123
MASSLicense Protection 123
MalwareAnalysis Advanced Service 123
Supported Common Documents and File Types 123
ProtectYour Network From Web Threats 126
Content Analysis 126
Malware Analysis 126
Malware Exemptions andPolicy 127
Geolocation-Based Polices 127
Web Isolation 127
Threat Protection Policy Editor 128
Malware Policy From Risk Score 130
Web Isolation Policy Based on Risk Score 132
RiskScore Reporting 132

Policy Guide/Page 8
Exempt a Source From Malware Scan 134
Exemptable Sources 134
Exemption Levels 134
Procedures 134
Change Exemption Scanning Level 136
Exempt a Destination From Malware Scan 138
Exemptable Destinations 138
Exemption Levels 138
Procedures 138
Exempt Files From Error Handling 141
About Web Isolation 142
What is Web Isolation? 142
Protect Endpoints from Attack 142
Topography 143
About the Two Web Isolation License Types 144
Geolocation—The Advanced WebSecurity Add-On 144
About Web Isolation and UPE 144
About Web IsolationOperations 144
Traffic 145
Enable Web Isolation 146
Procedure 146
Step 1—Enable Web Isolation 147
Step 2—Define an Isolation Policy Rule 147
Isolation Based on Risk Scores 148
Monitor Licensed Capacity 149
Web Isolation Reporting 149
Skype for Business Issue 150
About Web Isolation With UPE 151
Technical Requirements 151
Limitations 151
Supported Deployments 151
Web Isolation PolicyTemplate 154
Technical Requirements 154
About the PolicyObjects 154
UPEand Web Isolation Policy Template 154
About SSLInterception of Mobile Traffic (UPE) 155
About FailureModes 155
About Geolocation Policies 156
Supported Methods 156
Reporting 156
Exception Pages 156
User Privacy 157
CFS Policy 158
About the Cloud Firewall Service 159
Licensing and Use Cases 159

Symantec Web Security Service/Page 9
Supported Connectivity Matrix 163
CFS Traffic Overviews 163
About the CFS Policy Editor 167
Technical Requirements 167
Limitations 167
About theCFS Policy Editor 167
CFS Policy Construct 167
Global Rules 168
Create Custom CFS Rules 169
CFS Policy Planning and Examples 181
Plan CFS Policy Enforcement 181
Example Planning Use Case 181
Example Policies 183
Default Deny Policy? 184
Policy: How Do I? 185
Service 185
Content 185
User-Related 185
Define Object Lists to Use in Custom Policy 186
GeolocationObjects 189
Modify the Default Response Page 190
Procedure 191
Troubleshooting Assistance 193
Customize the Response Pages 194
Portal Location 194
Use Cases 194
BestPractices 194
The Editor 195
Examples 196
Provide Browsing Coaching to Users 199
Policy Example—Prevent Unauthenticated User Access to Content 201
Allow Individuals Access to Blocked Content 203
Create Policy From a Reported User 205
Create Policy Based on Reporting Usernames 209
Advanced Policy Example—Set Web Access Times 211
Policy Example—Define Policy For Mobile Users 213
Policy Example—Block Application Actions 214
Force Safe Searches 216
Policy Reference 217
Reference:Updated Content Filtering Categories 218
Reference:Role-BasedAccess Fields 223
Reference: File Types Detected by Advanced Policy 224

Policy Guide/Page 11
WSS High Performance Policy Tuneup—Begin Here
Next to routing traffic to the Web Security Service, defining policies is the most important aspect of your web security solution.
If the WSS is the vehicle body, the various policy editors comprise the engine.
The following series of topics walks you through policy configurations using the analogy of stopping at specialized
shops
to
customize and fine tune your policy engines.
The journey begins with high-level overviews, then proceeds to each shop-topic in the logical order of consideration as suggby
Symantec professionals. The audience for this task is network/security professionals who have admin access to the WSS.
Tip:Some policy editors are included with the WSS base Web Security license; other requires
add-on licenses. Each topic denotes requirements.
Policy Overviews
The following sections provide high-level policy overviews.
Web Use
Policy controls are flexible and allow you to apply global settings or granular rules for web content categories, web applications,
threat protection, and web isolation. For example, you can determine what happens to requests based on the role of requester.
In the above example, WSS policy is defined to achieve the following:
n A—Allow a network subnet, which requires the highest performance level possible, to bypass WSS malware scanning,
but explicitly block another specific destination. For example, you do not want Group B allowed access to sensitive
locations that have company IP.
n B—Allow the Sports website category, but deny Gambling sites.
n C—Allow access the Facebook social networking web application but within Facebook block games; allow webmail
applications.

Symantec Web Security Service/Page 12
SSLInterception
Create and enable SSL policy to ensure WSS correctly intercepts and exempts SSLtraffic. Intercepting SSL traffic allows WSS
to decrypt HTTPSconnections, examine the contents, and perform policy checks. Exempting SSL traffic allows traffic to remain
encrypted.
Location Policy (Authentication)
WSS Authentication Policy enables you to define the authentication method employed depending on the fixed Firewall/VPN
(IPsec) or Explicit Proxy location. This is helpful when you have a mix of authentication methods. For example, the Auth
Connector provides authorization and authentication for all connections through on-premises firewall devices, but you employ a
SAML IdP for remote locations connecting through Explicit Proxy.Or, if a location does not have access to an Auth Connector or
SAMLIdP, enable CaptivePortal.
Threat Protection
Protection your network from threats can involve up to four different policy components.
n Content Analysis—Without any additional configuration, WSS provides protection against malware and malicious web
content designed to harm networks or obtain private user information. You can define policy that is more granular; for
example, allow or deny specific destinations for specific user groups. Additional licensing enables deeper malware
analysis.
n Risk Scoring—Allow or block access to content that has been rated Cautionary Risky, Moderately Risky, or Risky levels.
You can also define custom risk score-based policy.
n Geolocation—Allows you to create policy based on from what country or to what country a content request occurs.

Policy Guide/Page 13
n WebIsolation—A client-less solution that enables employees to safely browse the internet on any device using any
browser. Web Isolation executes web sessions away from endpoints, sending only safely rendering information to
users' browsers, thereby preventing malware from reaching your network and devices. Web pages are rendered and
isolated as graphics for display on the end user’s browser.
Policy Testing Best Practices
n The enterprise network that you are administering will likely have more than one connectivity method and is accessed
by a mix of on-premises employees and employees connecting remotely explicitly or through installed agent.
n Symantec recommends preparing more than one test client.
n As you define and test policy, analyze the results side-by-side from different types of user classes.
Ready to visit the first custom policy shop?
n Proceed to "WSS Policy Custom Shop 01—Bypass" on page14.

Symantec Web Security Service/Page 14
WSS Policy Custom Shop 01—Bypass
This topic is the first in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order. IMPORTANT—This topic only applies to locations that use the ExplicitProxy and WSSAgent WSS
connectivity methods. All other access methods ignore any bypass domain configurations.If you do not employ either of these
methods, proceed to the next topic.
Why Bypass Certain Destinations?
As important for you to consider what goes through your policy engines is to consider what should
not
. Preventing destinations
that do not require security from routing through the WSS ensures reports derived from policy transactions do not contain
unnecessary. This keeps your policy engines running efficiently.
Consider the following typical destinations to bypass:VPNs; internal sites and IP addresses (such as intranets); trusted sites;
or any destinations that would skew web use reporting. On occasion, you might temporarily add an IP address or domain entry to
the bypass list while you troubleshoot a connection.
Technical Requirements
n WSS Admin credentials.
n No add-on license required.
n Explicit Proxy and/or WSSAgent connections.
Portal Locations
Connectivity >Bypassed Traffic >Bypassed IP/Subnets and Bypassed Domains tabs.
Best Practices
n When you create a bypass entry, provide a description in the Comments.
n Keep the list as short and manageable as possible. For example, create list objects that contain all test IP addresses
instead of creating single entries.
n Schedule and perform regular audits on the lists to ensure all business needs are met.
Ready to visit the next custom policy shop?
n Proceed to "WSS Policy Custom Shop 02—SSLInterception" on page15

Policy Guide/Page 15
WSS Policy Custom Shop 02—SSLInterception
This topic is the second in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
Why Intercept SSLTraffic?
By default the WSS does not intercept inbound HTTPS traffic from destination web locations and applications. With the default
configuration, the WSS applies content filtering policy to the furthest extent possible; however, it cannot apply policies to
transactions that require deeper inspection, such as web application controls or malware scanning. Enabling SSLinterception
allows the WSS deep-level inspection components—Content Analysis and Malware Analysis—to decrypt HTTPSconnections,
examine the contents, and perform policy checks.
Technical Requirements
n WSS Admin credentials.
n No add-on license required.
n Download and distribute the WSS root certificate to all endpoints.
Portal Location
Policy >TLS/SSLInterception.
Use Case
The SSLpolicy engine provides the flexibility to perform specific exceptions to the deeper level scanning, which enables you to
balance the scales of privacy and security. In most organizations, known financial and health care web sites are exempted
from SSL inspection to protect their end user’s privacy.
By default, WSS does not intercept the following.
n HTTPS traffic that is categorized as Brokerage/Trading, FinancialServices, and Health, because this content
usually involves private, sensitive personal account information.
n Applications that are listed in the SSLBypass List or Mobile App Bypass list because their traffic is known to break
due to certificate pinning issues.
Beyond the default exemptions, your organization might elect or be required to exempt other categories, groups, or even
specific web destinations from SSLinterception. Consider an education organization. The EduExample school uses the

Symantec Web Security Service/Page 16
FACTS website, which provides education services. EduExample wants to exempt this site because it uses student and
teacher personal information.
1. Expand the SSLInterception Policy area.
2. In Row 3, where the other default exemptions are, click the edit icon.
3. Add the FACTS site.
a. In the Conditions area, Add a Destination.
b. Select Domain/URL.
c. Select New Domain/URL.
Policy Guide/Page 17
d. Add https://factsmgt.com and click Save.
e. Save the rule.
4. If not already done, at the top of the page toggle SSLInterception to enabled.
5. Click Activate.
Ready to visit the next custom policy shop?
n Proceed to "WSS Policy Custom Shop 03—Authentication Exemptions/Locations" on page18

Symantec Web Security Service/Page 18
WSS Policy Custom Shop 03—Authentication Exemptions/Locations
This topic is the third in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
To keep the engines running efficiently, the system might not require authorization to specific destinations or from specific
locations. The WSS has two distinct authentication policy modules:Exemption and Location Policy (including CaptivePortal).
What is Authentication Exemption?
Some network issues or business decisions might require that specific sources are exempt from authorization to any or specific
destinations.
Captive Portal or SAML authentication methods, which are
redirection-based
methods, display a separate window for users to
enter their credentials to continue. Some network issues might prevent the client systems from displaying these windows.
n CORS-related issues.
n Authentication looping with cloud-based IdP servers.
n The source device (for example, a legacy server) is not compatible with redirection-based authentication.
n A web application API call is not compatible with redirection-based authentication.
To mitigate this, add destinations and sources that you want exempted from authorization challenges.

Policy Guide/Page 19
What is LocationPolicy?
WSS Authentication Policy enables you to define the authentication method employed depending on the fixed Firewall/VPN
(IPsec) or Explicit Proxy location. This is helpful when you have a mix of authentication methods. For example, the Auth
Connector provides authorization and authentication for all connections through on-premises firewall devices, but you employ a
SAML IdP for remote locations connecting through Explicit Proxy.Or, if a location does not have access to an Auth Connector
or SAMLIdP, enable CaptivePortal.
Technical Requirements
n WSS Admin credentials.
n Firewall/VPN and/or Explicit Proxy connectivity method(s) with locations defined (Connectivity >Locations).
n Auth Connector deployed; SAML implementation; or both.
Portal Location
Identity >Authentication Policy.
Use Case
n Your enterprise locations are global and employ different authentication methods.
o
The Firewall/VPNconnectivity method with the Auth Connector at global, regional headquarter locations.
o
Explicit Proxy with Okta as the SAMLIdP at regional satellite offices.
o
Micro-office with Explicit Proxy on a public ISP—requires CaptivePortal and a 12-hour auth challenge refresh
interval.

Policy Guide/Page 21
WSS Policy Custom Shop 04—Content Filtering
This topic is the fourth in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
To prevent engine damage, you want to filter out fuel additives before they enter the engine.
What is Content Filtering?
The Content Filter Policy Editor is where you shape your acceptable web use policies. To ensure adherence and security,
define policies that restrict or allow network and web elements such as IP addresses, content filtering categories, web
applications, and actions.
Technical Requirements
n WSS Admin credentials.
n No add-on license required.
Portal Location
Policy > Content Filtering.
About the Editor
Continuing the analogy, the policy editor is a dual-chamber engine. The first noticeable aspect is that two sections comprise
the editor: Group Aand Group B. When you add a new rule, WSS automatically places the rule in the correct evaluation order,
as some rules
must
be in A or B. However, the best practice is that you understand the order importance.
n Group A—The rules cannot
depend
on the content returned from the web destination; thus, if the rule matches, the
content never reaches the Origin Content Server (OCS). An example here is a rule that contains an action LOGIN to a
specific website.
n Group B—If no rule in Group A triggers a policy action, WSS checks rules in Group B, which
might
depend on returned
content. Rules in Group B can execute on traffic before it reaches the web destination, such as a blocked IP address or
content filter category. However, if any rules contain actions that must execute on returned content, they are placed in
Group B. This includes actions such as policy based on file type, an Allow verdict with web use coaching, and Block
verdicts with password override.

Symantec Web Security Service/Page 22
Where possible, the editor indicates where the rule belongs. For example, the Contents and Limits construct contains a File
Type element. Because this element requires a response from the OCS is required, any rule containing File Types must be in
Group B. The editor indicates as such.
Use Case
Salesforce is a cloud application that is used by many enterprises.
n John Sales atExample Corp sends a request for salesforce.com.
n After the previous policy (shop) checks, the request arrives at the Content Filter dual-chamber engine.

Policy Guide/Page 23
n Group A rules check for a whitelisting (no) and if user John.Sales@example.com is allowed access to Salesforce (he
is).
n Group B rules check for any content limits (no) and if the business/economy content category—in which Salesforce is
categorized as—is blocked (no).
n Barring any down—line policy blocks, John Sales is granted access to the Salesforce platform.
After reviewing reports, Example Corp has discovered that too many employees are consuming work hours playing online
games and IT Security adds a rule to block the Games category. However, further discussions revealed that just a simple
global block rule would not suffice. The executives want access to gaming sites. Furthermore, the Marketing group often
conducts social gatherings with customers after at the conclusion of training seminars. This includes game competitions for
prizes.
Revisiting the engine flow, the following occurs.
n Maya, the CEO, logs into her World Of Warcraft account.
o
No rules in Group A trigger.
o
In Group B, the Games category is allowed for her User account. She is allowed access.
n Jose in theMarketing group requests an online gaming portal at 4:58 PM local time.

Symantec Web Security Service/Page 24
o
No rules in Group A trigger.
o
In Group B, the Contents and Limits policy construct checks the time policy; it is not yet after the defined work
hours andJose's request is declined. At 5:05 local time, he performs the request again and now it is after work
hours and the request is allowed.
n Bobby sends a request for the Steam gaming site.
o
Bobby is neither an executive nor in the Marketing group.
o
Bobby's request makes it to the global Games category block rule and he is denied.
The above rules as constructed in the editor.
Ready to visit the next custom policy shop?
n Proceed to "WSS Policy Custom Shop 05—ThreatProtection" on page25

Policy Guide/Page 25
WSS Policy Custom Shop 05—ThreatProtection
This topic is the fifth in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
The engine is running smoothly, but we do not want the diagnostic systems to become infected with malware.A premium
package provides even deeper scanning.
What is Content Analysis?
At this point in the web transaction, the request has made its way to WSS (not on the Bypass list) and continued through the
content protection policies—white lists and category checks. The next check the WSS policy performs is Content Analysis. If
the request includes objects, such as files, stylesheets (CSS), java scripts, or any related objects that could possible contain
virus hashes
, WSS performs scans of these objects as well as static and dynamic code analysis.
Technical Requirements
n WSS Admin credentials.
n No add-on license required.
What is Malware Analysis?
Without any additional configuration, WSS provides protection against malware and malicious web content designed to harm
networks or obtain private user information. The service leverages the Global Intelligence Network™ (GIN), which is driven by a
community of users that numbers into the tens of millions. As these users browse web content, scanned content receives a
category rating. The database is updated in real time. The WSS policy checks against this database.
The default and unalterable Content Filtering policy prevents access to malicious content websites. These blocked categories
are located in these sub-groups:
n Security >Security Concerns: Spam
n Security >Security Threats:Malicious Outbound Data/Botnets, Malicious Sources/Malnets, Phishing, Proxy
Avoidance
n Legal Liability >Liability Concerns: Child Pornography
Malware Analysis works in conjunction with your Content Filtering policy. For example, Content Filtering policy allows a
request to the Social Media category, but Malware Analysis then detects a the requested file contains a virus, the download is
denied, and the client receives an exception page explaining the deny.
Additional licensing provides real-time sandboxing, post-delivered detonation capabilities and admin notifications.

Symantec Web Security Service/Page 26
Technical Requirements
n WSS Admin credentials.
n No add-on license required.
n Optional add-on licenses: Malware Analysis Standard or Advanced.
About the ThreatProtection Policy Editor
Use the ThreatProtectionPolicy Editor to further customize your protection strategy. For example, you might—
n Elect to have a stronger file type protection strategy for mobile users.
n Allow specific users or groups access to permanently blocked categories.
n Allow access to uncategorized content.
n Define policies that depend on multiple conditions. For example, the rules triggers if for a specific group that accesses
from a specific location (ANDconstruct). You can also create OR constructs.
Navigate to Policy > ThreatProtection.
As with the Content Filter editor, the ThreatProtectioneditor contains policy rows grouped by A and B.
n A—These rules do not depend on content returned from the destination.
n B—These rules might depend on returned content.
About Exemptions
As with other policy engines, you can define exemptions—known safe destinations that are excluded from Content Analysis.
Policy > Content & Malware Analysis> Scanning Exemptions area.
Symantec Web Security Service/Page 28
WSS Policy Custom Shop 06—RiskScore
This topic is the sixth in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
The engine is running smoothly, but we do not want the diagnostic systems to become infected with malware.This is a value-
add shop.
What is Risk Score?
Policy by Risk Score is an extension of the ThreatProtection policy. The Global Intelligence Network feed, which populates the
WSS content categories databases, also provides
risk scores
assigned to all websites. Scores range from 1 to 10; a site with a
1 rating is deemed Very Likely Safe while a 10 rating is Malicious. This allows you to define even more granular threat policies.
Technical Requirements
n WSS Admin credentials.
n Advanced Web Security with Risk Controls and Web Applications add-on license.
Portal Location
Policy > ThreatProtection.
Enhanced Threat Protection Policy Editor
With the entitlement license activated, the Threat Protection policy editor now has three default rules after the G3 rule.

Policy Guide/Page 29
Strategic PolicyExample
With the combination of content filtering, content and malware analysis, and risk scores, you have to components to craft
custom policy to address almost any business requirement. Consider the following scenario.
n Example Corp puts on a NewHire Boot Camp at a semi-remote retreat; the WiFi is not strong.
n The Training Team wants to download their YouTube videos so they can play them locally versus streaming during the
conference.
n The Training Team contacts IT and complains that they cannot access the application required to download the videos.
n You investigate and discover that the application, youtubedownloader, is categorized at Suspicious and is known to
contain adware/spyware.
How can you modify policy to allow the Training Team access while maintaining security for the entire organization?
STEP 1
In the Content Filter policy editor (Policy > Content Filtering), add a rule that allows theTraining group access to the
youtubedownloader.com domain.
The editor places this rule in Group B.
STEP 2
Return to the Threat Protection editor.

Symantec Web Security Service/Page 30
n Add youtubedownloader.com to the whitelist (TrustedDestinations).
n Add the same allow rule you created in the Content Filtering policy (allowing Training access to
youtubedownloader.com).
1. The request reaches the content policy; because Training is allowed, the request continues to threat protection.
2. The request sees in Group A that youtubedownloader.com is in the white list. So, it does not move on to the rule below
that would block the site because of the 7 risk score. A separate rule is not necessary because all other employees are
blocked (Suspicious category) in the Content Filter policy.
Ready to visit the next custom policy shop?
n Proceed to "WSS Policy Custom Shop 07—Geolocation" on page31

Policy Guide/Page 31
WSS Policy Custom Shop 07—Geolocation
This topic is the seventh in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
The engine is running smoothly, but we want our GPS to keep us out of danger.This is a value-add shop.
What is Geolocation?
Allows you to create policy based on from what country or to what country a content request occurs. Block potentially
unwanted sites if corporate policy does not allow business transactions with certain nation states. This is also valuable for
reporting and investigation purposes if unusual traffic is detected going to a specific nation state. Create a granular subset of
rules that allow or block based on required corporate policy.
Technical Requirements
n WSS Admin credentials.
n Advanced Web Security with Risk Controls and Web Applications add-on license.
Portal Location
Geolocation options are available in both the Policy >Content Filtering and Policy > ThreatProtectioneditors.
Enhanced Policy Editors
With the entitlement license activated, the Content Filter and ThreatProtection editors have Geolocation available in both the
Sources andDestinations constructs.

Symantec Web Security Service/Page 32
Strategic PolicyExample
Example Corp does business in Russia; however, they want to block all Web Ads/Analytics sites that are based in theRussian
Federation; that is, based on location not RiskScore.
Business can proceed; but with enhanced security because nefarious data collecting applications are blocked.
Again, a transaction will only reach this policy if it has passed through the previous six shops.
Ready to visit the next custom policy shop?
n Proceed to "WSS Policy Custom Shop 08—WebIsolation" on page33

Policy Guide/Page 33
WSS Policy Custom Shop 08—WebIsolation
This topic is the eighth in a series of topics that describe how to approach defining WSS policy engines in the Symantec-
recommended order.
This is a value-add shop.
What is WebIsolation?
Web Isolation is a client-less solution that enables employees to safely browse the internet on any device using any browser.
All requests are allowed, but WebIsolation executes web sessions away from endpoints. Web pages are
rendered
and isolated
as graphics for display on the end user’s browser. This prevents malware from reaching your network and devices. A common
use case is to protect employees who browse uncategorized and potentially malicious sites.
Technical Requirements
n WSS Admin credentials.
n WSS root certificate installed on all clients.
n Web Isolation requires one of the add-on licenses.
n Selective Isolation—Allows for about 5% of web traffic per subscribed seat for isolation.
n Full Web Isolation—You can extend this license to some or all subscribed seats. Grants 100% isolation per
subscribed seat.
n (Optional) Advanced Web Security with Risk Controls and Web Applications add-on license—Enables Web Isolation
based on Risk Score.
Portal Location
Policy >Web Isolation
About the Editor
The Web Isolation policy editor is very similar to the other policy editors. You can add Sources and Conditions.

Symantec Web Security Service/Page 34
Instead of an Allow or Block verdict, select Isolation or Do Not Isolate.
n Isolate— WSS executes the web request in a secure, isolated environment and performs Web Isolation malware
scanning.
n No Isolation— WSS bypasses Web Isolation and serves the response as the full web content.
Again, building on the previous custom shop, use WebIsolation in conjunction with Risk Score logic to isolate traffic across any
category that has a higher then normal risk score. For example, isolate web traffic that has a threat risk score of 7
and
was not
blocked by previous policy logic.
Customization Complete!
n Proceed to "WSS Policy Custom Shop—Roll Out" on page35

Policy Guide/Page 35
WSS Policy Custom Shop—Roll Out
This policy tutorial used the analogy of visiting various custom engine shops to describe how all of the various WSS policy
decisions work together.
You now have the knowledge to create policies and build a fully-revved up vehicle that provides the highest security, protects
the enterprise network, and ensures employee use compliance.
Policy In Review
This tutorial walked you through the policy considerations in the order that Symantec recommends considering.
n As you define new rules, be mindful of how they might impact existing rules.
n A change to an existing rule or simply moving a rule higher or lower in a list of rules is a very important best practice to be
a successful policy administrator.
n Do not forget to click Activate after each policy change.
Full Help Topics
Help buttons on each policy page in the portal open that WSS Help System to relevant topics, as listed in the following link
library.
Bypass
n "Prevent IP/Subnet From Routing to the Web Security Service" on page88
n "Prevent a Domain From Routing to WSS" on page86
SSL
n "About Scanning Encrypted Traffic" on page40
n "Distribute WSS Root Certificate to Endpoints" on page44
n "Create SSL Policy" on page52
Authentication Exemptions and Locations
n Exempt FromAuthentication
n Authentication Location Policy
Content Filtering
n "About Content Filtering" on page70
n "About the Content Filtering Rule Editor" on page74
n "Create Custom Content Filtering Rules" on page78
Symantec Web Security Service/Page 36
Threat Protection
n "About Malware Scanning" on page121
n "Threat Protection Policy Editor" on page128
n "Exempt a Destination From Malware Scan" on page138
n "Exempt a Source From Malware Scan" on page134
Risk Score
n "Malware Policy From Risk Score" on page130
Geolocation
n "About Geolocation Policies" on page156
n "Create Custom Content Filtering Rules" on page78
Web Isolation
n "About Web Isolation" on page142
n "Enable Web Isolation" on page146
All Policy Order
This tutorial focused on the various editors that you can configure. There are there policy components that WSS evaluates,
depending of the portal entitlements. For example, you might have CASB or DLP licenses as well. See an overview of how WSS
evaluates all possible components.
n "About Web Security Service Policy" on page37

Policy Guide/Page 37
About Web Security Service Policy
For the Web Security Service solution,
policy
refers to configuration controls that restrict or allow network and web elements
such as IP addresses and content filtering categories. Only WSS users in the Admin Role can define the policies that comprise
a Secure Web Gateway solution.
Policy controls are flexible and allow you to apply global settings or granular rules for web content categories, web applications,
threat protection, and web isolation. For example, you can determine what happens to requests based on the role of requester.
In the above example, WSS policy is defined to achieve the following:
n A—Allow a network subnet, which requires the highest performance level possible, to bypass WSS malware scanning,
but explicitly block another specific destination. For example, you do not want Group B allowed access to sensitive
locations that have company IP.
n B—Allow the Sports website category, but deny Gambling sites.
n C—Allow access the Facebook social networking web application but within Facebook block games; allow webmail
applications.
About the Traffic Evaluation Order
The following summarizes how WSS and CloudSOC prioritizes and evaluates traffic according to behavior. When possible, all
behaviors are applied; the order addresses conflicts.

Symantec Web Security Service/Page 38
n Denial and blocking based on policy rules configured in the WSS portal or from Universal Policy Enforcement
(UPE)uploaded policy rules.
For security and compliance reasons, explicit denials (for Content Filtering or Threat Protection) must be applied.
n SSL Intercept exemptions configured in the WSS portal.
Explicit SSL exemptions (for example, traffic to Healthcare categories) are assumed to be defined by an organization's
legal compliance.
n CASB Gatelet processing of flows (with implicitly enabled SSL Interception).
To properly function, CASB Gatelets automatically implement SSL Interception for specific destinations.
n WSS-applied AV and DLP scanning.
DLPscanning occurs before the malware scanning.
n Web Isolation forwarding.
Policy Guide/Page 39
SSL Policy
Enable SSLinterception and define policy.
n "About Scanning Encrypted Traffic" on page40
n "Distribute WSS Root Certificate to Endpoints" on page44
n "Install SSL Root Certificate for Chrome Browsers" on page46
n "Install SSL Root Certificate for Mozilla Firefox Browsers" on page48
n "Install SSL Root Certificate for Microsoft Internet Explorer Browsers" on page50
n "Install SSL Root Certificate for Safari Browsers" on page51
n "Create SSL Policy" on page52
n "Troubleshoot Dropped SSL Connections" on page68

Symantec Web Security Service/Page 40
About Scanning Encrypted Traffic
By default the Web Security Service does not intercept inbound HTTPS traffic from destination web locations and applications.
With the default configuration, WSS applies content filtering policy to the furthest extent possible; however, it cannot apply
policies to transactions that require deeper inspection, such as web application controls or malware scanning. Enabling
SSLinterception allows WSS to decrypt HTTPSconnections, examine the contents, and perform policy checks.
To retain the security of personal private information, exclude some content filtering categories from termination and inspection.
By default, WSS does not intercept HTTPS traffic categorized as Brokerage/Trading, FinancialServices, and Health,
because this content usually involves private, sensitive personal account information. Additionally, for mobile devices, WSS
does not intercept traffic from a list of specific applications as these applications are known to break when intercepted on mobile
devices.
To view which applications WSS bypasses, see: https://knowledge.broadcom.com/external/article?legacyId=TECH252764
Tip:If your policy allows uploading and downloading attachments in Gmail, you
must
enable
SSLInterception. See "Define a User-Based Web ApplicationsPolicy" on page116.
Tip:All Intermediate CAs used for certificate emulate are signed with SHA-2 (SHA256).

Policy Guide/Page 41
Content Filtering Use Case
Some users configure their Facebook accounts for secure connections
(https://www.facebook.com/...). With SSLinterception enabled, WSS intercepts the inbound SSL
connections and applies a policy check, such as Block Games.
Without SSLinterception enabled, your acceptable web-use policies might not be fully enforced.

Symantec Web Security Service/Page 42
Malware Prevention Use Case
Another benefit of SSL interception is the detection of malware embedded in secure connection. No
further configuration is required as WSS provides malware scanning by default.
Without SSL intercept enabled, your network might still be at risk if WSS cannot intercept and inspect
inbound SSL connections.

Policy Guide/Page 43
Granular SSLPolicy
WSS allows you to selectively intercept HTTPS requests from specific network elements, such a
single users, user groups, locations, and access method. Consider the following use cases.
n You know that not all browsers in specific locations or user groups have the root certificate
installed and you want to exempt those elements until configuration completes.
n A single user is having SSL connection problems and you want to exempt that user while you
investigate.
In the following diagram, SSLinterception is enabled in WSS.
A—An employee located at the corporate Location performs an HTTPS request to Facebook.
B—An employee connecting through the Proxy Forwarding connectivity method performs an HTTPS
request to Facebook.

Symantec Web Security Service/Page 44
C—There is no SSLInterception policy based on location or the ProxyForward connectivity method , so
the interception occurs; WSS examines the returned HTTPS connection from Facebook.
D—A remote user with the WSSAgent installed on his client performs an HTTPSrequest to Facebook.
E—WSS is configured to exempt all HTTPS traffic from WSSAgent from SSLinterception.
Next Step
n If you do not want to enable SSL, Symantec still strongly recommends that you download and install the root certificate to
client systems. For more information, proceed to "Distribute WSS Root Certificate to Endpoints" below.
n Define granular SSL Policy. "Create SSL Policy" on page52
n Want to manage your own certificates? See "Deploy a Self Managed Certificate for SSLInterception" on page58.
Distribute WSS Root Certificate to Endpoints
While root certificates are
required
when SSLInterception is enabled, the best practice is to install the Web Security Service
root certificates on all client endpoints independent of the SSL setting. One reason is that a majority of social networking sites
use SSL, which means WSS must perform some SSL interception for policy checks and enforcement. Without the certificates,
clients receive UntrustedIssuer warnings, which generates support/IT inquiries and loss of productivity.
Tip:All Intermediate CAs used for certificate emulate are signed with SHA-2 (SHA256).
BestPractice—Replacing a Certificate
If you are replacing an existing root certificate with a new one, the best practice is to add the new certificate to the browser-
trusted list before removing the existing one. This prevents service disruptions.
Procedure—Obtain Certificate and Propagate
Step 1—Download the WSS root certificate.
If you previously completed this, proceed to Step 2.
If you enable SSL Interception, users receive a security warning dialog each time they attempt to browse an encrypted (HTTPS)
website. because their browser does not recognize the certificate returned by WSS. To prevent this security prompt, download
the certificate and propagate it to all client browsers.
Ensure that the WSS root certificate is installed on all clients. For clients with WSSAgent on the endpoints, the certificate is
automatically installed and applied to Internet Explorer, Edge and Google Chrome. If your organization uses Firefox or another
browser that has its own certificate store, this certificate must to be installed directly into that web browsing application.
1. Navigate to Policy >TLS/SSLInterception.
2. Expand the TLS/SSLInterception Certificate area.

Policy Guide/Page 45
3. Click Download.
4. Move the downloaded certificate to an internally accessible location, such as a server that hosts applications provided
by IT.
Step 2—Distribute or install the certificate on supported browsers.
Use an endpoint management application to propagate the cert to all supported client browsers.
The alternative method is to send out the link to the certificate location and instruct users how to install it. Select the following
links for browser-specific installation instructions.
n Apple Safari
n Google Chrome
n Microsoft Internet Explorer
n Mozilla Firefox
Related Topics
n "About Scanning Encrypted Traffic" on page40
n "Create SSL Policy" on page52
n Connectivity: Symantec Appliance Proxy Forwarding (Install/update the root cert on the proxy.)
n "Deploy a Self Managed Certificate for SSLInterception" on page58

Symantec Web Security Service/Page 46
Install SSL Root Certificate for Chrome Browsers
Perform the following steps for Google Chrome browsers. The procedures assume that you have downloaded the root certificate
from your WSS portal account to a network location.
1. In the Chrome browser, navigate to the Under the Hood settings page:Wrench icon >Options >Under the Hood (or
enter chrome://settings/advanced).
2. Access the import certificate wizard.
a. In the HTTPS/SSL area, click Manage Certificates.
b. Select the Trusted Root Certification Authorities tab.
c. Click Import.
3. Import the certificate.
a. On the first wizard screen, click Next.
b. Click Browse and navigate to the certificate location; select it and click Next.
c. Select the Place all certificates in the following store option.

Symantec Web Security Service/Page 48
Install SSL Root Certificate for Mozilla Firefox Browsers
Perform the following steps for Mozilla Firefox browsers. The procedures assume that you have downloaded the root certificate
from your WSS portal account to a network location.
1. Access the Import certificate screen.
a. Select Advanced.
b. Select the Encryption tab.
c. Click View Certificates. The browser displays the Certificate Manager dialog.
d. Navigate to where you stored the certificate and click Open.
e. ClickImport. The browser displays the Downloading Certificate dialog.
2. On the Downloading Certificate dialog, select Trust this CAto identify websites and click OK.
Symantec Web Security Service/Page 50
Install SSL Root Certificate for Microsoft Internet Explorer Browsers
Perform the following steps for Microsoft Internet Explorer browsers. The procedures assume that you have downloaded the root
certificate from your WSS portal account to a network location.
1. In the browser:
a. Navigate to where you downloaded the file.
b. Right-click the file, and select Install Certificate.
c. You might be prompted for admin credentials and/or a confirmation prompt.
2. On the first wizard screen, clickNext.
3. On the Certificate Store screen:
a. Select the Place all certificates in the following store option.
b. Click Browse.
c. Select the Trusted Root Certification Authorities option.
d. ClickOK.
4. Click Next.
5. Click Finish.
6. If another security warning dialog displays, click Yes.
Next Step
n Return to "Create SSL Policy" on page52.
Policy Guide/Page 51
Install SSL Root Certificate for Safari Browsers
Perform the following steps for Apple Safari browsers. The procedures assume that you have downloaded the root certificate
from your WSS portal account to a network location.
For Safari Browsers on OS X
1. From the browser, open the directory in which you downloaded the root cert file.
2. Double-click the certificate.
3. You are prompted to store the certificate in the login keychain or the system keychain. To make the certificate
available to all users of this system, select system keychain.
4. In Keychain Access, select the System keychain; then select Cloud Services Root CA certificate.
5. Select File > Get Info and expand the Trust section.
6. Change Secure Sockets Layer (SSL) value to Always Trust.
7. Close the dialogs and enter your password.
For Safari Browsers on a Windows System
1. In the browser:
a. Navigate to where you downloaded the file.
b. Right-click the file and select Install Certificate.
c. You might be prompted for admin credentials and/or a confirmation prompt.
2. On the first wizard screen, clickNext.
3. On the Certificate Store screen:
a. Select the Place all certificates in the following store option.
b. Click Browse.
c. Select the Trusted Root Certification Authorities option.
d. ClickOK.
4. Click Next.
5. Click Finish.
6. If another security warning dialog displays, click Yes.
Next Step
n Return to "Create SSL Policy" on page52.

Symantec Web Security Service/Page 52
Create SSL Policy
Create and enable SSL policy to ensure WSS correctly intercepts and exempts SSLtraffic. Intercepting SSL traffic allows WSS
to decrypt HTTPSconnections, examine the contents, and perform policy checks. Exempting SSL traffic allows traffic to remain
encrypted.
By default, WSS does not intercept:
n HTTPS traffic that is categorized as Brokerage/Trading, FinancialServices, and Health, because this content usually
involves private, sensitive personal account information.
n Applications that are listed in the SSLBypass List or Mobile App Bypass list because their traffic is known to break due
to certificate pinning issues.
Note: If traffic is from a mobile device or bypassed (not intercepted), then WSS does not apply
CASB Gatelets or Web Isolation to the traffic. These features are currently not available for
mobile traffic, and bypassed traffic cannot be isolated.
For more information on decrypting SSLtraffic, see "About Scanning Encrypted Traffic" on page40.
Technical Requirement
n Download and distribute the WSS root certificate. See "Distribute WSS Root Certificate to Endpoints" on page44.
About the SSL Bypass List
Symantec maintains an initial list of applications in the SSL Bypass List that are known to break when their traffic is intercepted
due to certificate pinning. The list is continually being updated; however, traffic for additional applications and domains that are
not included in the list might break. For these applications and domain, use the policy editor to exempt them from SSL
interception. For the list of applications in the SSL Bypass List, see:
https://knowledge.broadcom.com/external/article?legacyId=TECH252764
Note: The sites and applications in the SSL Bypass List are also exempted for mobile devices.
About Mobile SSL Policy
You can apply SSL interception policy for mobile devices using the policy editor. Symantec maintains an initial list of
applications in the Mobile SSL Bypass list that are known to break when their traffic is intercepted due to certificate pinning.
The list is continually being updated; however, traffic for additional applications and domains that are not included in the list
might break. For these applications and domains, use the policy editor to exempt them from SSL interception. For the list of
applications in the Mobile SSL Bypass list, see: https://knowledge.broadcom.com/external/article?legacyId=TECH252764

Policy Guide/Page 53
Note: In the default policy, the sites and applications in the Mobile App Bypass list are only
exempted for mobile devices (unless the site or application is also listed in the SSL Bypass
List).
About SSL Sources and Destinations
You can write policy to intercept and exempt traffic for:
n Sources: Define policy that instructs WSS to not intercept SSLtraffic from these sources. The portal enables you to
select from previously defined lists or other elements as defined in your network.
n Destinations: Define policy that instructs WSS to not intercept SSLtraffic to these destinations. The portal enables
you to select from previously defined lists or other elements as defined in your network.
For more information on the policy editor, see "About the Content Filtering Rule Editor" on page74.
Element
Type
Available Options
Sources
n Detected authentication elements (User, User Group)—As provided by the authentication method (Auth
Connector/SAML).
Tip:Be advised that user/group data is not always available before
SSLInterception occurs.
n IP/Subnet—Select from previously entered IP addresses/subnets that were defined on the Policy >
Object Library page.
n Locations—Exempt entire locations defined that are defined on the Connectivity > Locations page.
n Deployment Type—Exempt all SSL traffic from a specific connectivity method. For example, do not
intercept SSL traffic from any client connecting with Roaming Captive Portal or from mobile devices.
n Lists (User, User Group, Location, IP/Subnet)—These are previously defined object lists. To create a
list to use specifically for this SSLpolicy, navigate toPolicy > Object Library >User Defined Objects.
Destination
n Category—Exempt web traffic that belongs to specific categories.
n URL andIP/Subnet—Exempt specific URLs or IP addresses. Select from previously entered domains
that were defined on the Policy > Object Library >User Defined Objects page.
n Lists (Category List, URL List, IP/Subnet List)—These are previously defined object lists. To create a
list to use specifically for this SSLpolicy, navigate to Policy > Object Library >User Defined Objects.
Note: Before you enable policy, ensure you have downloaded and distributed the root
certificate. See "Distribute WSS Root Certificate to Endpoints" on page44.

Symantec Web Security Service/Page 54
About OCSP Validation
The OCSP Validation toggle provides you with the ability to enable or disable OCSP validation checks, so that you can:
n Decide whether sites that fail validation are at risk for being untrustworthy.
n Resolve any errors that are produced when OCSP validation is enabled.
Procedures
To create policy to exempt or intercept SSLtraffic:
1. Navigate to Policy > TLS/SSL Interception.
2. Expand the TLS/SSL Interception Policy area and click Add Rule.
3. (Optional) Add sources:
a. Click Add Sources.
b. From the Available Sources drop-down lists, expand an element to filter the view.
c. Select one or more sources to create policy for and click the right-pointing arrow to move sources to the Source
Conditions list.
d. (Optional) For most categories, you have the option to create a new source. The New drop-down list allows you to
create a new object and add it to the policy from this dialog. This might be helpful if you are immediately
troubleshooting from a source that is not currently part of a custom list.

Policy Guide/Page 55
e. Click Save.
4. (Optional) Add destinations:
a. Click Add Destinations.
b. From the Available Destinations drop-down lists, expand an element to filter the view.
c. Select one or more destinations to create policy for and click the right-pointing arrow to move destinations to the
Destination Conditions list.
d. (Optional) ) For most categories, you have the option to create a new source. The New drop-down list allows you
to create a new object and add it to the policy from this dialog. This might be helpful if you are immediately
troubleshooting for a destination that whose traffic is blocked by SSL policy.

Symantec Web Security Service/Page 56
e. (Optional) You can create policy that uses Symantec's list of mobile applications that are known to break when
decrypted. To add the list to policy, from the Available Destinations screen, click Mobile App Bypass.
f. Click Save.
5. Assign a verdict:
n To intercept traffic for your defined sources and/or destinations, click Intercept.
n To exempt traffic for your defined sources and/or destinations, click Do Not Intercept.
6. Click Add Rule.

Policy Guide/Page 57
7. After defining interception and exemption policies, enable SSL policy:
a. Toggle the switch to Enabled.
b. Click Activate Policy. WSS now intercepts SSL traffic per the defined policy.
Warning: Enabling SSL on WSS might introduced unintended results for some
websites. If your clients experience dropped connections, consult the information in
"Troubleshoot Dropped SSL Connections" on page68.
8. (Optional) Configure the service to pass-through specific encrypted destination URLs, IP addresses/subnets, or
Categories.
Tip:See also Apply Limited Policy to Non-Intercepted SSL Traffic.

Symantec Web Security Service/Page 58
Deploy a Self Managed Certificate for SSLInterception
To ensure that all traffic is properly analyzed, you can configure the Web Security Service to intercept and decrypt SSL traffic.
By default, the WSS portal supports only a certificate chain managed by Symantec. If your organization prefers to use your own
certificate infrastructure, you can license the Self Managed Certificate service to integrate your WSS portal with a Hardware
Security Module (HSM) hosted on Amazon Web Service (AWS).
This solution describes how to integrate an Amazon Cloud HSMservice with a WSS account.
Note: For each domain in your WSS configuration, you must configure a unique HSMhost.
About Integrating HSM
Self Managed Certificate support provides you with the ability to install your own certificate into the WSS portal. With this in
place, you can accomplish the following:
n Simplify user on-boarding
When SSL/TLStraffic is intercepted and decrypted by WSS, the private key stored on the integrated HSM is used. At no
point does the private key leave the HSM. As users' browsers already trust your root certificate, adding users to WSS
requires less setup time.
n Control your own certificates
With this configuration, you retain control of your certificate chain and how it is used.
Frequently Asked Questions
A Virtual Private Cloud (VPC) Peering connection is required to establish the connectivity between both VPCs. How is the VPC
Peering connection created between the Symantec and customer VPCs?
n To interact with the HSM instance in an AWS CloudHSM cluster, the AWS CloudHSM client software is required. The
software is installed inside the Symantec VPC. The CloudHSM client supports only the IP address of the HSM instance.
The CloudHSM Cluster is created in a private subnet of the customer VPC.
n The SMC init script creates a cross-account role for the auto-acceptance of the VPC Peering connection request. This
role is used when a new VPC is provisioned in Symantec's account and when creating a VPC Peering connection with
the customer VPC. You can revoke this role after successfully completing all steps.
What are the best practices to setup the CloudHSM Cluster?
n Refer to the following AWS link.
https://docs.aws.amazon.com/cloudhsm/latest/userguide/best-practices.html
How do I setup a CloudHSM cluster in multiple regions?

Policy Guide/Page 59
n As having CloudHSM in a single region potentially adds latency, setting up CloudHSM Clusters in multiple regions is a
best practice. To have the same key available in multiple regions, copy a backup from one region to another. Perform
the steps provided in the following link.
https://docs.aws.amazon.com/cloudhsm/latest/userguide/copy-backup-to-region.html
How are signing requests for generating emulated certificates routed to multi-region CloudHSM Clusters?
n There can be only one customer-specific DNS, which is mapped to all CloudHSM setups deployed in different AWS
regions. The DNS is configured with a latency-based routing policy. Thus, WSS sends signing requests for generating
certificates to the nearest region.
Technical Requirements
Ensure that you have the following.
n An Amazon Web Service (AWS) account hosting a CloudHSM cluster.
n An EC2 instance in the AWS Account where the AWS CLI has been configured with AWS administrator credentials.
n Python 2.7 (pre-installed in Amazon Linux)
To check the Python version, run the following command in your EC2 instance:python --version.
n APython Installable Package (PIP) module version 6.x and above compatible with Python 2.7.
To check your PIP version, run the following command in your EC2 instance: pip --version.
If PIP is not installed, execute this command: sudo yum install python2-pip.
n AWSSoftware Development Kit, Boto3, version 1.7 or later above.
To check what version of Boto3 is installed in your EC2 instance, run this command:pip freeze | grep boto3.
If Boto3 is not installed, run this command in your EC2 instance:sudo pip install boto3.
n WSS SUBSCRIPTION ID
This ID is included in your WSS order confirmation email.
If you are new to WSS, wait to receive the confirmation mail before proceeding with steps outlined in this document.
n CloudHSM Cluster ID
See the step labeled To Create a Cluster in the following CloudHSM documentation.
https://docs.aws.amazon.com/cloudhsm/latest/userguide/create-cluster.html.
n CloudHSM CA Certificate, saved as customerCA.crt
This file is used in the Initialize the Cluster step in the following CloudHSM documentation.
https://docs.aws.amazon.com/cloudhsm/latest/userguide/initialize-cluster.html.
n CloudHSM Crypto Username and Password

Symantec Web Security Service/Page 60
These credentials are created during the Create Users step in the following CloudHSM documentation.
https://docs.aws.amazon.com/cloudhsm/latest/userguide/manage-hsm-users.html.
Step 1—Prepare Your CloudHSMAccount For WSS Integration
After you have satisfied the prerequisites, log in to your AWSEC2 instance and complete the following tasks:
1. Copy the file SelfManagedCertificate.zip to any directory on your EC2 instance.
This file is included in your Symantec Provisioning Form.
2. Unzip the file with the following command:
unzip ./SelfManagedCertificate.zip
This command extracts the files into a new directory called SelfManagedCertificate.
3. Copy the CloudHSM CA Certificate file customerCA.crt —identified in the Technical Requirements section above—to the
SelfManagedCertificate directory created in Step 1.2.
4. Create an account role to allow the automatic acceptance of the Virtual Private Cloud (VPC) Peering connection from
Symantec's AWSaccount, and extract your CloudHSMCluster information with the following script. To define these
values manually, see appendix A at the end of this procedure.
./smc_init -r <AWS_REGION> -i <CLOUDHSM_CLUSTER_ID> -u <CRYPTO_USERNAME> -p <CRYPTO_USER_PASSWORD>
-s <WSS_SUBSCRIPTION_ID> -a <SYMC_AWS_ACCOUNT_ID>
If the script fails, a log file is automatically created under SelfManagedCertificate/logs.
5. Create an S3 bucket with the following path:
https://s3.console.aws.amazon.com/s3/buckets/wss-smc-tenant-<WSS_SUBSCRIPTION_
ID>/provisioning/<AWS_REGION>.
Upload the file to this new bucket, and provide access to the Symantec AWSaccount.
The preceding script performs the following tasks:
n Creates a CloudFormation stack called wss-smc-vpc-peer-role.
n Extracts the CloudHSM Cluster information required for peering with the Symantec HSMclient.
n Uploads your CloudHSMconfiguration details to an AWSS3 bucket and provides access to Symantec's AWSaccount.
Script Variables
The variables in the above command script are as follows:
n <AWS_REGION> = AWS—The region of your CloudHSM installation, based on Amazon's definitions here:
https://docs.aws.amazon.com/general/latest/gr/rande.html#cloudhsm_region
n <CLOUDHSM_CLUSTER_ID>—The Cluster IDfor your CloudHSMaccount.

Policy Guide/Page 61
n <CRYPTO_USERNAME>—The username for the account you created during the prerequisites stage.
n <CRYPTO_PASSWORD>—The password for the account you created during the prerequisites stage.
n <WSS_SUBSCRIPTION_ID>—The Subscription ID provided to in your WSS order confirmation email. If your Subscription
ID includes an underscore (_), replace it with a dash (-).
n <SYMC_AWS_ACCOUNT_ID>—239531557249 is the Symantec AWS Account ID.
Caution:If you receive an Access Denied error message when executing the script, verify that
AWS credentials configured on EC2 instance have adequate privileges to execute these
commands. Review the log_{current_ date}.log file under ./logs sub-directory for
additional information.
Procedure—Verify Peering Association was Created Successfully.
1. Log into the AWSWeb Management console and verify that the CloudFormation stack labeled wss-smc-vpc-peer-
role was created.
a. Navigate to the AWSServices page and search for CloudFormation.
b. Confirm the following:
n wss-smc-vpc-peer-role is listed among your Stacks, with a status of CREATE_COMPLETE.
n The RoleARN key is listed in your Outputs configuration.

Symantec Web Security Service/Page 62
2. Send an email to WSS-SMC-Provisioning.pdl@broadcom.com with the subject SMC Initialization: WSS Subscription
<WSS_SUBSCRIPTION_ID> to inform Cloud Operations that the configuration is complete.
Note: This email address is to be used for provisioning only. For support concerns, please
reach follow the appropriate support contact steps as directed on
https://support.broadcom.com/security.
WSS Operations provisions your WSS cloud account and sends you an email with an S3 URL.Use the URL in the next section
to complete the association.
Step 2- Register your CloudHSM/WSSAssociation
1. In the AWSManagement page, open the CloudFormation Console and click Create Stack.
2. When prompted to select a template, select Specify an Amazon S3 template URL.
Paste the URLprovided by WSS Operations and click Next.
3. Enter a name for your Stack and click Next.
4. Click Next on the options page; no optional configuration items need to be changed. Click Next.
5. Review the details in the review page, and click Create.
CloudFormation updates the required AWS resources to complete the VPC peering.
6. Browse to the CloudFormation console.

Policy Guide/Page 63
The stack status shows CREATE_COMPLETE. This confirms that the appropriate entries have been created in the
Security Group and Route Table.
Step 3-Activate CloudHSM in the WSSPortal
Verify that the service is active and configured.
Navigate to Account Configuration > Product &Licensing. Confirm successful integration by looking for the green check
mark with Paired next to AWSCloudHSM.
Step 4-Enable Your Intermediate Certificate for SSLInterception
1. In the WSS portal, navigate to Policy > TLS/SSLInterception.
2. Click Add Self Managed Certificate.

Symantec Web Security Service/Page 64
Select your Intermediate CAcertificate from the Private Key Handle list and paste in the public key that goes with it.
3. Select the option corresponding to the new self managed certificate.
Click Use for SSLInterception.
4. Click Activate at the top of the portal to commit these changes to your portal account.
5. Toggle the option from Disabled to Enable to intercept, decrypt, and re-sign SSLconnections.
Tip:You can click the download button next to your certificate in the list to download the public
key to your local system.
Known Issues
n Certificate Expiration Behavior— 60 days prior to a Self Managed Certificate expiring, the SSL configuration portal page
displays a warning. If the certificate used for interception expires, the service requires intervention. You must perform one
of the following:
o
Install a certificate with a valid expiration date.
o
Use the Symantec Certificate (see Step 3 above)for interception.
o
Disable SSLinterception.
n AWSCertificate Key Labeling
Policy Guide/Page 65
The Amazon Web Service does not enforce any rules to ensure that the keys hosted in your AWSHSM clusters are
labeled with unique names. The Amazon-provided CloudHSM APIs to retrieve key information is based on labels;
querying for a list of keys results in an array of entries identified by labels. The APIprunes duplicate labels from this list.
As WSS relies on this information, use unique labels for each private key.
n Maximum Certificate Chain Depth
The Self-Managed Certificate currently only supports a maximum certificate chain depth of three: Root CA >
Intermediate Issuer CA > Emulated Server Certificate. If your security infrastructure requires support for additional
intermediate CA certificates, push the intermediate CA certificates to client browsers. This ensures that the appropriate
trust relationship is maintained and full verification of the certificate chain is successful.
n DLP Scanning Behavior During Failure
In the event of a CloudHSM failure or error, DLP will not actively block leaks. When CloudHSM is operational DLP
functions as intended.
Manual Cluster Information
To manually gather cluster information, collect the following and upload to the S3 bucket (as in Step 4).
Step 1—CloudHSM Cluster information
Create file with the name smc_config. Add the following the contents:
n
awsAccountId=
n
vpcId=
n
cidrRange=
n
routeTableId=
n
securityGroupId=
n
crossAccountRoleArn=
n
partitionName=
n
cryptoUser=
n
cryptoUserPwd=
n
eniIP=

Symantec Web Security Service/Page 66
Example smc_config File
awsAccountId=12345678901
vpcId=vpc-389bd941
cidrRange=10.0.0.0/16
routeTableId=rtb-f50c758d
securityGroupId=sg-0b1dd275
crossAccountRoleArn=arn:aws:iam:: 12345678901:role/wss-smc-vpc-peer-role-peerRole-1BSWQUNBM7XBI
partitionName=PARTITION_1
cryptoUser=username
cryptoUserPwd=password
eniIP=10.0.2.29
Step 2—Upload the file.
As described in Prerequisites, upload the customerCA.crt file to the following S3 Bucket URL.
https://s3.console.aws.amazon.com/s3/buckets/wss-smc-tenant-WSS_SUBSCRIPTION_ID/provisioning/AWS_REGION
n WSS_SUBSCRIPTION_ID—The Subscription ID provided to you by Symantec in your WSSorder confirmation email. In the
event your subscription ID includes an underscore, (_) replace it with a dash (-).
n AWS_REGION—AWS region of your CloudHSM. For CloudHSM AWS Regions refer the following AWS documentation:
https://docs.aws.amazon.com/general/latest/gr/rande.html#cloudhsm_region
Example
Sydney region is ap-southeast-2.
Provide read and write access for this S3 bucket to Symantec's AWSaccount:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::239531557249:root"
},
"Action": [
"s3:GetBucketAcl",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::wss-smc-tenant-WSS_SUBSCRIPTION_ID"
]
},
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::239531557249:root"
},
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:::wss-smc-tenant-WSS_SUBSCRIPTION_ID/*"
]
}
Policy Guide/Page 67
]
}
WSS_SUBSCRIPTION_ID—The Subscription ID provided in your WSS order confirmation email. If your Subscription ID contains
an underscore (_), replace it with a dash (-).
Symantec Web Security Service/Page 68
Troubleshoot Dropped SSL Connections
With SSL enabled, the Web Security Service intercepts the SSL request to perform its security functions. This means that there
must be a trust established between the requesting workstation and the service. The workstation allows the service to access
the secure site (on the client's behalf) and establish an intermediary trust.
Dropped SSLConnections
Access issues might be caused by either one of the following scenarios.
n In some instances the requested HTTPS site (SSL) might detect that the request has been intercepted and disallow the
connection. One way the site determines this is by certificate pinning, which is the process of recognizing the host or
service’s certificate when an attempted connection occurs. Because a cert already identifies or associates both parties,
any attempt to come in between the client and the OCS is immediately recognized and the connection is refused. The
workaround is to find out what domains are getting looked at for the certificates and then exclude them from SSL
interception.
n Another method sites might use to prevent and protect against attacks is to allow access only from predefined IP
addresses. These predefined IP addresses are part of the
web sites allowed
addresses or ACL (access control list).
When an attempted connection occurs from a site that is not allowed by the ACL, the request goes unacknowledged. For
the user, the browser seems to not reach the site and times out.
In this scenario and similar, take these sites' IP addresses and set an exception on your firewall that excludes these addresses
from going through the IPSec tunnel; for other access methods, add these IP addresses to the SSL Pass Through IPs/Subnets
list.
Policy Guide/Page 69
Filter Content
Configure the WSS to apply content filtering policy to web requests and responses.
n "About Content Filtering" on page70
n "Control User Access to Web Content" on page72
n "About the Content Filtering Rule Editor" on page74
n "Create Custom Content Filtering Rules" on page78
n "Modify the Default Response Page" on page190
n "Customize the Response Pages" on page194

Symantec Web Security Service/Page 70
About Content Filtering
The Web Security Service leverages the Global Intelligence Network(GIN), which is driven by a community of tens of millions of
users. As these users browse web content, GIN scans the content and assigns a category rating. WSS policy checks against
this database.
WSS enables you to define a Content Filtering policy that meets your business requirements. Policy consists of a combination
of blocked and allowedweb content categories and trusted and blocked sources and destinations. You have the option to create
global rules (basic policy) that apply to all users or create more granular rules (advanced policy).
In the above example, there are two types of users:Executive Staff and standard Employees. The WSS policy achieves the
following:
n A—The Exec initiates two web destinations:a Gambling site and a Newsgroups/Forums site.
n B—Employees request Shopping, Sports, and Newsgroup/Forums sites.
n C—The WSS Policy and Content Filtering engines determine what happens based on who is allowed access to which
categories.
n The Exec is denied the gambling site, as Gambling is a globally blocked category. However, she is allowed
access to the news forum because the Exec group is given permission to the Newsgroup/Forums category.

Policy Guide/Page 71
n Employees are allowed to the shopping sites (although they might receive a coaching message). They are
blocked from accessing Sports sites, except for espn.com, which is configured as allowed. Another option here
is to allow access only during specific days and times.
n Unlike the Exec group, employees are also denied access to sites rated as Newsgroup/Forums.
Note: All trademarks used herein are the property of their respective owners.
Symantec Web Security Service/Page 72
Control User Access to Web Content
By default, the Web Security Service blocks the most common web categories that are deemed inappropriate in the work
environment or are known sources of malicious content. Furthermore, if High Risk Coverage was selected as the default policy
during the Initial Configuration, the WSS blocks additional web content. WSS enables you to alter the default Content Filtering
policy to meet the needs for your business environment.
About the Default Policies
When you or someone in your organization performed the WSS on-boarding, the DefaultPolicy selection was presented. Based
on that initial selection, the WSS blocks categories.
The following policy controls provide a baseline policy against all other transactions:
n Monitor—Provides only malware scanning. Users are allowed to browse anywhere.
n Child pornography
n Malicious Outbound Data/Botnets
n Malicious Sources
n Phishing
n Proxy Avoidance
n Spam
n Standard—In addition to the Monitor categories, provides malware scanning plus blocks access to the most common
questionable content, such as mature.
n Adult/Mature Content
n ControlledSubstances
n Gambling
n Hacking
n Nudity
n Peer-to-Peer (P2P)
n Piracy/Copyright Concerns
n Placeholders
n Pornography
n Potentially UnwantedSoftware
n Remote Access Tools
Policy Guide/Page 73
n Scam/Questionable/Illegal
n Suspicious
n High—In addition to the Monitor and Standard categories, provides malware scanning plus blocks access to the most
common questionable content and common categories that are not work-related, such as social networking sites.
n Dynamic DNSHost
n Extreme
n IntimateApparel/Swimsuit
n MixedContent/Potentially Adult
n SexEducation
n Sexual Expression
n Software Downloads
n Violence/Hate/Racism
n Weapons
Regardless of this selection, you can further modify policy from the WSS portal after completing the registration process.
Step 1—Review the current Content Filtering policies and adjust if necessary.
n "About the Content Filtering Rule Editor" on page74—Describes the Policy Editor rows and elements.
n "Create Custom Content Filtering Rules" on page78—Demonstrates how to create policy constructs and rules.
n "About Geolocation Policies" on page156—Learn about how to execute policies based on countries (requests to and
requests from).
Step 2—After WSS begins processing data, monitor employee web use
activity.
n For a high-level summary, view the Content Filter Dashboard (Dashboards>Content Filtering).
n Generate a pre-defined report. Select Reports > Report Center. Click any link to generate a report.
Step 3—(Optional) Configure an exception page that users see when they
browse to a blocked web destination.
n "Modify the Default Response Page" on page190.
n "Customize the Response Pages" on page194.

Policy Guide/Page 74
About the Content Filtering Rule Editor
The Web Security Service Content Filtering Rules policy editor allows you to accomplish the following:
n Create custom rules that, based on who requested it, allow or block access to web content.
n Quickly define global policy, or rules that apply to every employee that is not explicitly allowed or blocked by a custom
rule.
Navigate to Policy >Content Filtering. The Policy Rules matrix comprises five columns—an Order column and four policy
constructs—and a series of rows. The following sections describe how to interpret the editor and create new rules.
Content Filter Policy Construct
Policy Rules columns provide options for four constructs that shape the purpose of the rule.
By Column name—
n Sources—Applies to content requests. Users, Unauthenticated Users, Groups, IPaddresses/Subnets, fixed Locations,
WSSAgents, Mobile Users, and Geolocations (if your account has the license). The default is Any.
n Destinations—Applies to requested content Categories, Web Applications, IP addresses/Subnets, Domains/URLs,
and Geolocations. The default is Any.
Tip:See "About Geolocation Policies" on page156 for more details.
n Content and Limits—Applies to content parameters. For example, set the policy to only apply to selected file types,
browsers, or actions within web applications.
o
Actions, such as media uploads and downloads, joining meetings, games.
o
Specific browser vendors.
o
File Types
o
Schedule—Define when the policy rules apply, such as during core business hours.
The default is the rule applies to all contents at any time.

Symantec Web Security Service/Page 75
Note: Some Actions are valid only in Group A; others in Group B. For example, File
Types are notated with a B. These items correspond to the rows that WSS will place them.
The Contents and Limits section below discusses this.
n Verdict—
o
Allow or block the request or content if any policy matches occur in the rule.
o
Advise (coach) employees that their internet activity is recorded
o
Redirect the user to another web location (such as an intranet site that lists appropriate web use guidelines).
o
Require a password to access content.
AND/OR Constructs
The Policy Editor enables you to create And/Or constructs. For example, you have a rule where the Sources are either of two
users (an Or construct) if the request from a specific location (anAnd construct). TheAdd a Policy Rule section below
demonstrates an example.
Group and Global Rows
The rules editor contains two distinct areas:Group A and Group B. As you add and modify rules, the Content Filtering Rules
policy editor automatically places the rules in the correct group and correct order.Rules might contain conditions for a mix of
inbound and outbound traffic; the actions and whether the elements in the request or the response triggers the policy dictates the
appropriate rule grouping. Furthermore, the editor displays messages whenever a rule addition or change requires a rule to be
moved. This section describes why rules are placed where they are.
Rules are evaluated in order. If a rule matches, no other subsequent rules are checked.
Group ARules
As the service executes the rules in this group first, the only conditions available are those that test the request and the only
actions are those that can be enforced on the request. The rules in GroupA cannot
depend
on the content returned from the web
destination. This is because for this group of rules the WSS must check the policy
before
the request reaches the content
server.
If traffic matches a GroupA rule, the
request
never reaches the
server
. Keep this in mind as you develop policy. For example,
you might prefer to put rules in GroupA when possible for security reasons.

Policy Guide/Page 76
Group B Rules
If no rule in Group A triggers a policy action, WSS checks rules in Group B. As such, while Group A cannot depend on
returned content, Group B
might
. Rules in Group B can execute on traffic before it reaches the web destination, such as a
blocked IP address or content filter category. However, if any rules contain actions that must execute on returned content, they
are placed in Group B. This includes actions such as policy based on file type, an Allow verdict with web use coaching, and
Block verdicts with password override.
Global Rules
There are hard-coded rule rows that cannot be deleted. They are designated as G1, G2, G3, and G4. Primarily, these rules are
in place to enforce pre-defined, default policies. Where applicable for the rule, the columns contain links. Click the link to
display an editor dialog from which you can specify or select policy objects that apply to everyone (unless they are allowed or
blocked by other custom policy).
n G1—Designated row for permanently blocked categories, such as ChildPornography.
n G2—An Allow rule that applies to source IP addresses/subnets. The policy check occurs on the request.
Symantec Web Security Service/Page 77
n G3—An Allow rule that applies to specific trusted, or safe, destination URLs, IP addresses/subnets, and web
applications. For actions, such as uploading and downloading content, the policy occurs on the response.
n G4—A Block rule that applies to specifically blocked destination categories and webapplications, URLs, and IP
addresses/subnets.
In the editor, mouse-over the text bubble icons and the G-numbers in the left column to view these descriptions in text pop-ups.
Create a new rule?
n "Create Custom Content Filtering Rules" on page78

Policy Guide/Page 78
Create Custom Content Filtering Rules
You will more than likely need to create policy rules that accomplish your corporate web use guidelines while ensuring the web
resources required for your business remain available. For example, you might have applied a global block to a specific content
category or web application, but now need to allow specific users or groups access.
Tip:To save time, create policy objects (Policy > Object Library page) that you know you will
use multiple times. For example, a set of allowed domains or a group of categories.
Navigate to Policy >Content Filtering.
To launch the rule wizard, click Add Rule.
n The Conditions area is where you define the constructs of the policy rule. From who or where did the request originate?
To where is it going? And does it apply to specific content or based on a time frame?
n The Verdict area is where you define the action to take if the rule is triggered.
Construct and Editor Tutorials
The Editor and a Sources Construct
This example demonstrates what you can add to the Sources construct of the rule, including how to use the editor. Click Add
Sources.

Symantec Web Security Service/Page 79
The policy editor is flexible, allowing you to select objects and existing lists as well as create new lists from objects within. Refer
to the screenshot.
a. Select from objects that WSS currently detects, such as usernames and group names provided by the authentication
methods (Auth Connector or SAMLIdP), IP addresses, and fixed locations. You can also select a Geolocation, which
means the request originated from a specific country.
Tip:Geolocation policy requires an add-on license. See "About Geolocation Policies" on
page156 for more details.
b. If you have previously created custom lists in the Object Library (Policy > Object Library) or previously in the policy
editor, select a List item.
c. The policy editor provides static objects that apply to all connections from those sources.
n UnauthenticatedUsers—A username that is not part of your corporate username database.
n Mobile Devices—Users who log in through a smartphone or tablet.
n WSSAgents—Users who log in from remote client systems that have the WSSAgent installed. These are
connections from beyond the corporate network.
Select any construct to display its options.
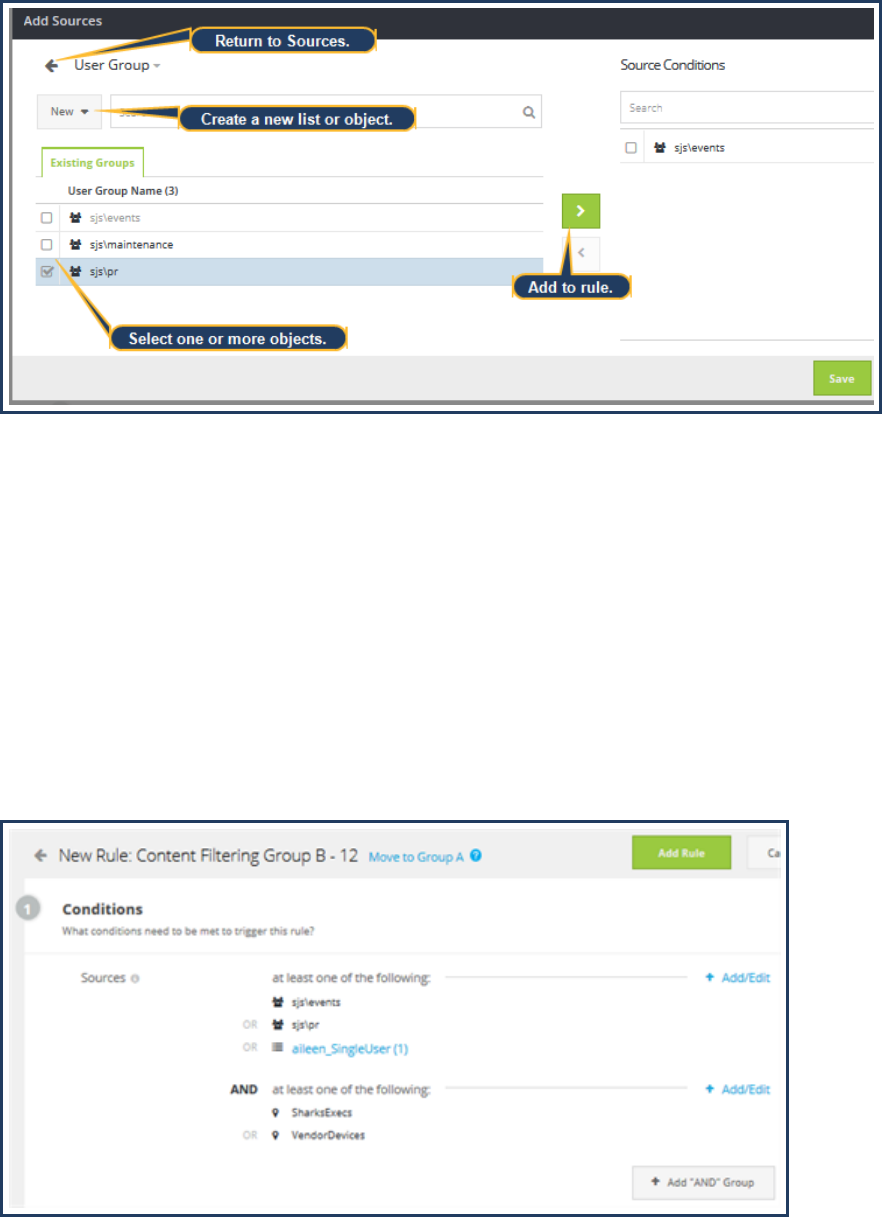
Policy Guide/Page 80
n The editor displays all of the objects that are available for this rule. Select one or more and click the right-arrow to assign
them to the rule.
n You can also click New and select to create a new list or in applicable constructs a new object.
After completing your selections, perform one of the following.
n If this rule is intended for these sources only, click Save.
n To add different source constructs, click the back-arrow (upper-left); repeat to add sources and clickSave.
This creates an OR construct; the rule triggers if the content request originates from a source associated with any of the
objects.
You can also continue to add sources that create an AND construct. Consider the following example.
The Admin clicked Add "AND"Group and added two fixed Locations as Sources. Now the rule is triggered by any user
belonging to the events or pr groups ANDfrom the specified Locations, one through a firewall device and one through explicit
proxy.

Symantec Web Security Service/Page 81
The Destinations Construct and Creating Lists
This example demonstrates what you can add to the Destinations construct of the rule, plus how to create lists within.
Click Add Destinations. Select internet elements to which this rule applies. As with the Sources construct, you can create
AND/OR policies.
n IP/Subnets and URLs/Domains—You might have a need to trigger policy when the destination is a specific server, such
as a testing server, or a specific URL path.
n Category—Policy applies when the request is for websites that belongs to a specific content category. The Symantec
Global Intelligence Network (GIN) continuously rates and classifies websites as they come online.
n WebApplication—Policy applies when the request is for one or more of the thousands of web applications WSS detects.
This is also known as a Cloud Access Security Broker (CASB) discovery and policy solution.
Create a List
On many policy editor screens, there is an option to create a list from objects you select.
After you name, create, and save the list, it becomes available for future selection in other rules.
The Contents andLimits Constructs
The final trigger Construct bases the rule on the following elements.
n Schedule—If you set a schedule, the rule applies only on the specified days and during the specified hours. For example,
you might want certain content restriction rules to apply only during core business hours.
n Browser—Your company might elect to employees to use the most recent versions or even one specific browser vendor.
n File Type—Trigger the rule if the request is for specific types of files, such as Databases or Audio and Music.

Policy Guide/Page 82
Tip:See "Reference: File Types Detected by Advanced Policy" on page224.
n Actions—When paired with WebApplication Destinations, you can provide a robust, granular policy. For example, you
might allow access to various social networking sites, but want to prevent the uploading or downloading of photos and
videos for specific applications.
This page provides an additional Filter field from which you can select a specific application and view what actions
WSS detects.
Conflicts with Actions and File Types
n Notice that some Actions are amended with an A.Rules that contain specific actions, such as File Upload, must be
enforced during request before the actual upload request reaches the server. Such objects require the rule to be created
in Group A.
n Notice that all File Types are amended with a B. For rules that contain specific actions, such as Executable, WSS
must see the contents of the
response
so that it can detect whether it is actually an executable. Such require the rule to
be created in Group B.
If you attempt to create a construct that contains incompatible elements, WSS displays a red exclamation mark to indicate an
error. You can roll over the letters to read an explanation. You must create separate rules to achieve your policy goal.
The Verdict Construct
Now that you have created the conditions that trigger the policy rule, the final configuration is to instruct WSS what action to
take. This is called the Verdict.

Symantec Web Security Service/Page 83
Allow
n Allow:Completely—Users are allowed access to the content.
n Allow:Coaching—Before allowed content access, users must click a message that acknowledges their request for such
content and that they understand their web activities are monitored. You can also change the interval between coaching
message re-displays.
Block
n Block—Users are denied access to the content.
n Block:Password Override—You can specify a password that you can distribute to users who request access to a
blocked content. You can also change when the coaching message re-displays.

Policy Guide/Page 84
n Redirect—In addition to blocking access to the content, you can enter a URL that redirects users to a specific web
resource. For example, when a user attempts to browse inappropriate content, redirect them to an internal web page that
describes your corporate web use guidelines.
Activate Policy
Now the that rule is complete, click Add Rule.
Based on the constructs, WSS automatically inserts the rule to the bottom of Group A or B accordingly on the Content
Filtering Rules page. However, you might elect to rearrange the rule. For example, you have a rule that takes an action based
on a group membership but want to take some other action for a specific user.
To move that rule above the group rule, select the rule number to display a menu.

Symantec Web Security Service/Page 85
The orange triangles indicate that the policy is not yet activated. The WSS also displays policy discrepancies, which you must
first resolve.
Click Activate to implement the policy.
Exempt URLs from Permanently Blocked Categories
The Group AG1 rule provides a construct for Permanently Blocked Categories. By default, Child Pornography is
permanently blocked (others might be added in the future). It cannot be changed.
But you might have a requirement for specific users or groups to be able to access URLs that belong to a Permanently Blocked
Category.
1. In the editor menu bar, clickSettings.
2. In the dialog, select Allow exemptions to Permanently Blocked Categories in Content Filtering.
The editor adds a new row designated as P1.
3. Click the Permanently Block Source Exemptions and/or the Permanently Block URLExemptions links and add
exemptions as required.
Tip:This topic provides a high-level description of the rules editor. See "Policy: How Do I?" on
page185 for use case examples.

Policy Guide/Page 86
Prevent a Domain From Routing to WSS
IMPORTANT—This topic only applies to locations that use the ExplicitProxy and WSSAgent WSS connectivity methods. All
other access methods ignore any bypass domain configurations.
Some destinations, such as intranets, do not require WSS processing. Configure the service to ignore these connections.
Another use case is you have use policy enabled, such as blocking several leisure categories, but you want to relax restraints
for remote users and allow their requests to bypass WSS en route to specific sites.
Notes
n WSS allows an unlimited number of bypassed domains.
n The bypass setting is a simple match; the hostname and top level domain are used for policy matching. For example, a
request for www.test.com matches bypass policy for test.com, but also for shop.test.com.
n The setting is global; that is, it applies to every location/client in your WSS account.
n Be advised that multi-homed domains might lead to over-bypassing a site.
n Each time that a WSSAgent reconnects to WSS (for example, a user who takes a laptop off campus and connects
through a non-corporate network), the client checks against any updates to the list.
Procedure—Manually Add Domain Entries
1. Navigate to the Policy >Bypassed Traffic >Bypassed Domains tab.
2. Click Add. The portal displays a dialog.

Symantec Web Security Service/Page 87
a. Enter a valid Domain.
b. (Optional)Enter a Comment.
c. (Optional)Click the +icon to add another row for another entry.
d. Click Add Domains.
The new entries display in the tab view. You can edit or delete any entry from here.
Import IPAddress Entries From a Saved List
This procedure assumes that you have already created an accessible list (text file) of domains to be bypassed. Each entry in the
file must be on its own line.
1. Navigate to the Policy >Bypassed Traffic >Bypassed Domains tab.
2. Click Add. The service displays the Add Bypass Domain dialog.
3. Click Import Domains.
a. Click Browse. The service displays the File Upload dialog. Navigate to the file location and Open it.
b. Click Import.
All of the new entries display in the tab view. You can edit or delete any entry from here.

Policy Guide/Page 88
Prevent IP/Subnet From Routing to the Web Security Service
IMPORTANT—This topic only applies to locations that use the ExplicitProxy and WSSAgent Web Security
Serviceconnectivity methods. All other access methods ignore any bypass domain configurations.
Some IP addresses or subnets do not require WSS processing. For example, you want to exclude test networks. Configure the
service to ignore these connections.
Notes
n WSS allows an unlimited number of bypassed IP addresses/subnets.
n Each time that a WSSAgent reconnects to WSS (for example, a user who takes a laptop off campus and connects
through a non-corporate network), the client checks against any updates to the list.
Procedure—Manually Add IPAddresses
1. Navigate to the Policy >Bypassed Traffic >Bypassed IPs/Subnets tab.
2. Click Add. The service displays a dialog.
a. Enter an IP/Subnet.
b. (Optional)Enter a Comment.
c. (Optional)Click the +icon to add another row for another entry.
d. Click Add IPs/Subnets.
The new entries display in the tab view. You can edit or delete any entry from here.

Symantec Web Security Service/Page 89
Import IPAddress Entries From a Saved List
This procedure assumes that you have already created an accessible list (text file) of IP addresses to be bypassed. Each entry
in the file must be on its own line.
1. Navigate to the Policy >Bypassed Traffic >Bypassed IPs/Subnets tab.
2. Click Add. The service displays the Add Bypass IP Address/Subnet dialog.
3. Click Import IPs/Subnets.
a. Click Browse. The service displays the File Upload dialog. Navigate to the file location and Open it.
b. Click Import.
All of the new entries display in the tab view. You can edit or delete any entry from here.

Policy Guide/Page 90
Modify the Default Response Page
By default, the Web Security Service displays response page to users when the transaction triggers an
exception
event, such
as a policy violation page when a user attempts to access a website or web application protocol that WSS policy is configured
to block. The content of the page includes the result message, such as Access Denied, along with other details, such as the
client IP address and the reason (for example, a blocked content filter category).
n WSS allows you to modify this page, including selecting a color scheme, adding contact information and changing the
displayed logo and company name. For example, add your ITgroup email address so that users can contact IT to
dispute a rating or ask a question about the policy.
n If your WSS account includes the Advanced Web Security with Risk Controls and Web Applications add-on license, the
exception includes the Client Location, or country of origin as determined by the service. For more details, see "About
Geolocation Policies" on page156.
n The Error ID indicates which policy rule triggered the exception. CF-XX is a content filter rule. TP-XX is a threat
protection rule. The exception displays N/A if it cannot determine the rule. Other operations, such a password override,
might cause an N/A.
Tip:You can also modify the template for this page. See "Customize the Response Pages" on
page194.

Symantec Web Security Service/Page 91
Additionally, English, French (European), German, Italian, Japanese, and Spanish (European) language web browsers displays
these pages in their respective languages.
Procedure
This task requires WSS portal Admin Role credentials.
1. Navigate to Policy >ResponsePages >Standard.
2. Customize contact information.
a. Select which additional text options to include on the page.In addition to letter and numbers, only spaces and plus
signs(+) are valid characters.
b. Select the page style and color.
c. Click Save.
3. Enter the Company Name field that replaces the current name on notification pages.
Policy Guide/Page 92
4. (Optional) Change the logo (.png file, 190 pixels x 35 pixels) that displays on exception pages. The default is the
Symantec company logo; however, if your company obtained WSS from a third-party service provider, their logo might
display instead. The logo you add here overrides that configuration.
a. In the Current Logo area, click Change. The service displays Upload Error Log dialogs.
b. Browse to the stored image; select it and click Open.
c. Click Save in the Error dialog.

Symantec Web Security Service/Page 93
To revert to the default file, click Change and select Reset.
5. Click Save.
Note: If WSS has other pending policy changes, a dialog displays to inform you of this.
You can accept to activate all pending policy or navigate to the various policy pages and
verify that you want those changes (then return here to save the notification changes).
6. Configure Content Filtering Policy.
Troubleshooting Assistance
You can force WSS to translate exception pages into English regardless of browser language version. The non-English browsers
do not display the site review URL. Temporarily forcing English can aid with troubleshooting, including talking to Support
Personnel who speak only English.
n Select Show English Translation Onlyand click Save.
n When assistance is complete, clear the option.
Policy Guide/Page 94
Customize the Response Pages
The Web Security Service displays response pages to users when a browsing action triggers an exception, such as a denied
content category. The page contains default information, including the exception reason. You can also select to display
information, such as contact information and a custom logo. These notification options should prove sufficient for most
enterprise requirements. This information comes from a template, which you can also customize.
Portal Location
Policy > Response Pages > Custom
Use Cases
n You do not want the notification page to contain specific elements, such as the logo or contact email.
n You want to change the background color or add additional text to an area on the page.
BestPractices
n Customizing the notification template is an advanced feature. As such, only admin-level WSS users are able to modify
the template contents.
n Have considerable knowledge of HTML and CSS before performing edits beyond simple string replacements.
n Perform only small, deliberate changes to the template rather than recreating a completely new template.
n To avoid display issues, keep the template code compatible with any browser vendor used by employees in your
enterprise.
n Certain sections of the template are critical for the page to function properly with other policy elements, such as the
Password Override feature. Avoid these clearly marked code sections in the template.
n Do not load content from servers that are outside of your control.
n JavaScript is running in the page under the context of the page that was blocked and might in some cases have
access to sensitive user cookies meant to be kept private. For this reason, avoid loading any third-party hosted
JavaScript.
n Requests to other resources (such as images) might have the Referrer HTTP header present from the page that
was blocked, revealing what page the user was visiting when the block page was served. For this reason, avoid
loading anything from a 3rd party server.
n When possible, directly include content in the template rather than hosting it on the Internet. This decreases load time
and guarantees that a resource is reachable.
n Base64 images can be encoded directly in the HTML.
n The template can contain CSS stylesheets.
n WSS displays the exception page for both HTTP and HTTPS connections. If an image (or some other resource) is
referenced in your template using the http:// protocol and the template is used for a page loaded over HTTPS, some
browsers might display a warning to inform the user that insecure content was loaded within a secure page. The same
might apply in the reverse situation where an https:// resource loads on a page over HTTP. For this reason, either

Symantec Web Security Service/Page 95
include the content inline as previously mentioned earlier or perform one of the following.
n Host your content both over http:// and https:// and
n Use a protocol-less URL to reference it; for example http://example.com/aResource becomes
//example.com/aResource.
The Editor
To view the Custom Notification editor, navigate to Policy >ResponsePages >Custom.
A—The Preview option allows you to view code changes before they are implemented.
B—Click Show Replacement Variables to display all of the code elements that the service uses to populate data.

Policy Guide/Page 96
The variables that begin with $(config.) are the ones that comprise the default Error Pages. These are ones that you can
elect to remove from the template.
C—If you run into problems with your edits or you want to start over and create a new template, click Reset to Default HTML,
which reverts the template to its default state.
D—When you click Enable custom error pages, the system might override any custom edits to Policy >Response Pages
>Standard. For example, if you add contact telephone number to the field on that page, but comment out the field in the
Custom template, the service does not display the entered phone number. If you clear the Enable option, the service returns to
the default page and any customizations that exist there.
Examples
The following examples illustrate how you can edit the template.
Add Text
Supplement the notification with custom text. The following example adds a new line to Tech support information drop-down
(accessed by clicking more).

Symantec Web Security Service/Page 97
ClickPreview to see how the service will display the page.
Remove an Element
Enter HTML code to comment out an element. For example, you do not want the notification to include detailed transaction
information/link. Locate the element in the template and add the comment out code: <!-- text -->.

Policy Guide/Page 98
IMPORTANT:Some span tags contain the localize attribute. Regardless of any customized text, this attribute instructs
WSS to overwrite with a localized version of the text (including English). To display custom text in a span, you must remove
the localize attribute. However, doing so prevents localization.
This line retains the default value because of the localize attribute.
<p id="httpCode"><span localize="[techSupport]">Tech support information</span>:$(exception.id)
This line provides the custom text:Tech support information.
<p id="httpCode"><span>Tech support information</span>:$(exception.id)
Customize theStyle
You can enter CSS code to change the appearance of the page. Locate the Symantec styling section.
You can also add JavaScript (above the style section) to add more complex HTML elements.
Symantec Web Security Service/Page 99
Web Application Policy
n "About Controlling Web Application Access" on page100
n "About the CloudSOC Integration" on page103
n "Integrate With CloudSOC" on page107
n "Set Default WebApplication Policy toAllow" on page112
n "Set Default WebApplication Policy toBlock" on page114
n "Define a User-Based Web ApplicationsPolicy" on page116

Policy Guide/Page 100
About Controlling Web Application Access
Web applications are vital to enterprise operations, yet also present challenges. You must balance the availability of various
applications required for business with security and your employee web acceptable Use policies. The Web Security Service
provides three methods to control web applications access. A combination of these methods allows you to create a robust, yet
targeted policy that both protects your employees while allowing them to perform their business tasks.
Always Block or Always Allow a Web Application
This policy option applies to
all
employees. WSS blocks all attempts to access specific webapplication destinations; or
conversely, the service always allows access to specified web application destination.
Allow a WebApplication But Block an Action
You can allow everyone access to specific Web Applications, yet prevent actions from within those applications. For example,
you allow Facebook access, but want to prevent video uploads to Facebook—an action that consumes valuable network
resources.
Symantec Web Security Service/Page 101
Define Who Can Access WebApplications
If your enterprise contains multiple users, groups, and roles, you will more than likely elect to define granular web application
policy. WSS allows you to specify who can access a webapplication, when they can access it, and what happens if they are not
allowed access. For example, you have different user groups with different requirements. The Marketing group requires access
to Facebook and Twitter; the HR group requires access to Facebook and Linkedin. Other groups are blocked access to those
applications.

Policy Guide/Page 102
Web Application Category Reference
For the current list of web applications that WSS recognizes, see the following article.
n https://knowledge.broadcom.com/external/article?legacyId=TECH242989
Want to configure Web Application policy?
n Proceed to Control Access to Web Applications.
n CASBAudit:"About the CloudSOC Integration" on page103.
Symantec Web Security Service/Page 103
About the CloudSOC Integration
The Web Security Service is an integrated platform for Content Filtering, Threat Protection, DLP, and CASB deep-controls on
cloud applications. The Symantec CASB platform, CloudSOC™, provides visibility to over 24,000 cloud applications and over 60
attributes
per
application. This enables scalable policy to control Shadow IT and cloud application access.
Symantec provides two WSS/CloudSOC integration solutions:
n CASB Gatelets—A full secure web gateway (WSS) solution plus integration with CloudSOC. After completing the one-
time WSS-to-CloudSOCintegration, you can apply a combined policy enforcement to both platforms based on their
respective configurations for all enabled application
Gatelets
. Configure gatelet policies in CloudSOC. An increased
number of web applications are available in WSS policy editors. The remainder of this conceptual topic discusses the
CASBGatelet solution.
n CASBGateway—ACASB-only solution. Configure WSS to identify and authenticate users and steer traffic to
CloudSOC. Use CloudSOC for all gatelet configuration, policy, and data analysis. Consult the CloudSOC documentation
for more information about this solution.
CASBGatelets Topography
This topography assumes that your CloudSOC is already operating.

Policy Guide/Page 104
1—A WSS admin links the WSS and CloudSOC accounts through a unique Integration ID. After launching CloudSOCfrom the
WSS portal, the Admin enables application Gatelets—for example, Yammer, Google Drive, Box. Within the Gatelets are
additional options, such as domains.
2—When Gatelet configurations are saved, WSS receives a list of applications subject to CASB deep control.
3—Regional employees (on campus or remote) perform requests for web application destinations.WSS processes the policy,
allows or denies the content, and adds entries to the access logs. WSS uses these access logs for report generation.
4—Over a secure connection, an API connects WSS to CloudSOC. WSS forwards the access logs to CloudSOC.
5—Admin or WSS accesses the WSS portal. From there, launches the CloudSOC portal, which opens in a separate browser
tab. In CloudSOC, users can generate reports.
Note: WSS remains in sync with the Symantec Global Intelligence Network (GIN). Updates to
the database occur each day.

Symantec Web Security Service/Page 105
About the Traffic Evaluation Order
The following summarizes how WSS and CloudSOC prioritizes and evaluates traffic according to behavior. When possible, all
behaviors are applied; the order addresses conflicts.
n The following graphic demonstrates the policy and service order when WSS receives a request.There are two
scenarios—A (no CASB Gatelet) and B (redirected CASBGatelet).
n Denial and blocking based on policy Allow/Deny rules is configured in the WSS portal or from Universal Policy
Enforcement (UPE)uploaded policy rules.
For security and compliance reasons, explicit denials (for Content Filtering or Threat Protection) must be applied.
n Authentication verifies the logged-in employee credentials.
SCENARIOA
No CASBGatelet:
n SSL Intercept except for exemptions configured in the WSS portal.
Explicit SSL exemptions (for example, traffic to Healthcare categories) are assumed to be defined by an organization's
legal compliance.
n Malware scanning and Sandboxing (with Advanced license).
n DLPscanning (with license).
n Web Isolation (if licensed) forwarding.
SCENARIOB
Policy Guide/Page 106
Applications routed to CloudSOC (CASBGateway) over ICAPservice:
n Authentication
Gatelets only work for WSS connectivity methods where the end user must authenticate. For example, if an endpoint
connects through explicit proxy with no authentication, the CASB Gatelet policy enforcement is ignored.
n
SSLInterception
When an enabled Gatelet matches, WSS forwards the traffic to CloudSOC, regardless of the SSL Interception setting.
n WSS-applied DLP and Malware scanning.
Because CASB Gatelets include Symantec content analysis and integration to Symantec DLP, material can be
exempted from WSS processing of those types.
The primary use cases for CASB Gatelets and Isolation are parallel. The Web Isolation service is focused on risky/unfamiliar
sites, while CASB Gatelets, are by definition, for sanctioned applications. The population of sanctioned applications is smaller,
thus they remain lower in the order because the account has enabled CASB.
Current Limitations
n O365 Gatelet—WSS global O365 SSL exemption is overridden for specific destinations.
n O365 Gatelet—File Sharing Block policy is ignored for the Desktop O365 Apps (OneDrive for Business, Word, Excel,
Powerpoint).
For example, if the file sharing block policy is in place and a user is attempts to share the files (already synced to
OneDrive) with another user/group, the files are allowed instead of blocked.
n Google Drive Gatelet—Similar to the Office 365 issue, data uploads from Google Drive are allowed despite blocking
policy in place.
n If you have modified O365 settings to disable the Modern-Authentication option, clients with WSSAgent installed are
not able to login to Outlook. The credential dialog repeats.

Symantec Web Security Service/Page 107
Integrate With CloudSOC
Symantec provides two CASB integration solutions with the Web Security Service:
n CASB Gatelets—Full WSS web security solution with enhanced web application from the CloudSOC service.
n CASBGateway—CASB-only solution where CloudSOCreceives user identity and traffic from WSS.
After you obtain the CASB license, you must perform the task to integrate WSS with the CloudSOC portal.
Technical Requirements
n When you purchase the CASB license, the admin on record receives an e-mail from Symantec that contains the
Integration ID. You must have this ID to register. The Integration ID is
not
the same number as your WSS Subscription
ID.
n This procedure describes how to integrate with an existing CloudSOC portal account. If you have not onboarded
CloudSOC, do so before continuing with this procedure.
Procedure
1. Navigate to Account Configuration >Products &Licensing.
2. In the Linked Products area, click CloudSOC CASB.
3. Define the integration information.
Policy Guide/Page 108
a. Enter your Company Domain.
b. Enter the Integration ID sent you by Symantec.
c. IMPORTANT—Select the appropriate Data Storage Location for your location. You cannot change this value
after setup.
d. Select how many Months of Data to Track. The current maximum is 3, which means you can view reports that
contain data from no more than the three previous months.
e. Click Save.
CASB Gatelets Solution Only
The following sub-sections apply only to the CASBGatelets solution only. If you have the CASB Gateway solution, continue
with the CloudSOCdocumentation topics.
WebApplication Policy
As web traffic flows through your network, you now have the ability to define granular block/allow and other actions on the tens
of thousands of detected web applications.
View CASB-RelatedReports
As WSS processes traffic, you can view specific reports that provide insight into web application traffic traversing your
network.
Navigate to Report Center. The following reports contain reports enhanced by the CASBAudit Service.
n Applications by User
n Applications by Client IP
n Blocked Web Applications
n Web Application Actions
Add Reporting Users
WSS Administrators can add other users and designate them as Reporting Users. These users can only view reports—they
cannot change configuration settings. When a Reporting User accesses the CloudSOC Service from the WSS portal, the audit
service uses the credentials to create a Reporting User role.
Add new users on the Account Configuration > Administrators page.
For more information, search for
roles
in the help.
Access the CASBAudit App
The top of the WSS portal has a drop-down arrow next to your Admin name. Select Cloud App Audit.

Symantec Web Security Service/Page 109
When you click Cloud App Audit link, the CloudSOC opens in a new browser tab.
The Dashboard displays high-level data. Click Store.

Policy Guide/Page 110
The store is where you enable web applications and define domains and policies that are then sent to the WSS portal and made
available in policies.
To learn more about implementing web application configurations and monitoring user activities, consult the CloudSOCHelp
system and other relevant Symantec documentation.
Delete the CloudSOC Integration
You can delete the WSS/CloudSOC integration. Be advised that this might cause adverse issues with other WSS
components. Symantec will provide best practices as they are developed.
Click CASBCloudSOC in theLinked Products area.

Symantec Web Security Service/Page 111
Click Delete Integration.

Policy Guide/Page 112
Set Default WebApplication Policy toAllow
The Web Security Service allows you to ensure that web applications vital to the effectiveness of your workforce are always
accessible (assuming that the application itself is functioning properly at the destination). For example, E*Trade applications
are required for your business operations.
Tip:As stated above, this is the default policy and WSS performs the check on the connection
inbound from the origin content server. You can create additional policy that blocks specific
users, groups, and locations access to the web applications that are otherwise allowed by
default.
Reference
For the current list of web applications that WSS recognizes, see the following article.
n Web Application Reference Article
Procedure
This procedure demonstrates how to select specific applications and specify them as always available to any employee (client)
that is routing web traffic to WSS (and is not otherwise blocked by more granular policy).
1. Navigate to Policy >Content Filtering.
2. In the Group A >G3 rule, click the Allowed Web Applications link in the Destinations column. The portal displays the
Edit Web Application List:Allowed Web Applications dialog.

Symantec Web Security Service/Page 113
a. The initial dialog is read-only. Click Edit.
b. Optional—Enter a Comment that describes the reason for the policy.
c. Select web applications from one or more high-level categories.
d. Click Save.
3. Click Activate Policy.

Policy Guide/Page 114
Set Default WebApplication Policy toBlock
The Web Security Service allows you to select specific web applications that you feel are detrimental to the effectiveness of
your workforce or the security of your network and set the
default
policy to block. For example, you think access to personal
webmail accounts, such as yahoo and gmail, provide a greater security threat. Or you need to block resource intensive or
time-wasting applications, such as streamed sports and social network destinations.
Tip:As stated above, this is the default policy and WSS performs the check on the connection
inbound from the origin content server. You can create additional policy that allows specific
users, groups, and locations access to the Web applications that are blocked for anyone else.
Reference
For the current list of web applications that WSS recognizes, see the following article.
n Web Application Reference Article
Tip:Obtaining the Symantec CASB license exposes thousands of applications.
Procedure
This procedure demonstrates how to select specific applications and specify them as unavailable to any employee (client) that
is routing web traffic to WSS.
1. Navigate to Policy >Content Filtering.
2. In the Group B >G4 rule, click the Blocked Web Applications link in the Destinations column. The portal displays
the Object Edit:Blocked Web Applications dialog.

Symantec Web Security Service/Page 115
a. The initial dialog is read-only. Click Edit.
b. Optional—Enter a Comment that describes the reason for the policy.
c. Select web applications from one or more high-level categories.
d. Click Save.
3. Click Activate Policy.

Policy Guide/Page 116
Define a User-Based Web ApplicationsPolicy
By combining several types of Web Security Service policy, you can create a robust web application policy that both protects
your network, ensures acceptable web use policies, and allows employees to complete their job duties based on their roles in
the organization. Consider the following use case and example policy.
Use Case
The default WSS settings for all applications is Allow. Previously, a WSS admin set the major webmail applications to Block
and set E*Trade to Allow. You now want to add a more granular policy based on user groups.
n The FIFAWorld Cup creates network bandwidth havoc every year; furthermore, reports indicate that Pinterest traffic is
trending upward and you want to block access.
n Both Facebook and Twitter can hinder productivity, yet are necessary marketing applications. You want to allow access
only to the Marketing group; however, you also want to block security risks (such as downloading files) and block
unnecessary features (such as games and chatting) for everyone in those groups.
Tip:How a user understands that an application action was blocked is application-
dependent. For some actions, nothing happens. This behavior might generate support/IT
tickets, so be sure such personnel understand this and can inform employees.
n Human Resources also uses Facebook plus Linkedin, but you do not want other employees job-networking while
working for you.
Example Policy
1. Navigate to Policy > Content Filtering.
2. Add FIFAWorld Cup, Facebook, Twitter, Linkedin, and Pinterest to BlockedWeb Applications to the global block
list.
a. In the Group B >G4 rule, click the Blocked Web Applications link in the ToWhere column. WSS displays the
Object Edit:Blocked Web Applications dialog.
b. The initial dialog is read-only. Click Edit.

Symantec Web Security Service/Page 117
c. Select the FIFA WorldCup application in the Sports/Recreation drop-down (you can search for the term).
d. Select the Facebook, Twitter, Linkedin, and Pinterest applications from the Social Networking drop-down.
e. ClickSave.
The Blocked Applications (#) number increments to include the four applications.
f. Blue asterisk icons indicate non-active policies. ClickActivatePolicy. At this point, anyone who attempts to
access any of those applications are blocked.
3. Allow Marketing access to Facebook and Twitter.
a. Click Add Rule. The service displays the CreateNew Rule dialog.
b. Click Add Sources.
c. Click User Group.
d. Select the group to be granted access—for this example, CorpMarketing.

Policy Guide/Page 118
e. Click Save.
f. Click Add Destinations
g. Click Web Application.
h. Search for Facebook and Twitter and add them; click Save.
i. For the Verdict construct, select Allow >Completely. Click Finish, which adds the rule in Group B above the
default global block rule. The order is important, as when a component of rule gets matched, subsequent rules
are ignored.
4. You now want to prevent Marketing employees from downloading attachments, playing games, and chatting from within
Facebook.
a. Repeat Step 3, creating a rule that applies to the same CorpMarketing group (Sources construct).
b. Select the same web applications on the Destinations construct.
c. Click Contents and Limits; click Actions.
d. Select the actions to block, such as Download Video and Games.

Symantec Web Security Service/Page 119
e. Click Save.
f. Set the Verdict construct to Block.
g. Click Add Rule; the service displays the new action blocking rule in Group B.
h. ClickActivate.
5. Create another rule for the CorpHR group to be allowed Facebook and Linkedin.
6. Click ActivatePolicy. You now have conditional rules that fully allow access, limit access, or block web applications.
How a user understands that an application action was blocked is application-dependent. For some actions, nothing happens.
This behavior might generate support/IT tickets, so be sure your support staff understand this and can inform employees.
Malware Policy
Configure the WSS to exempt specific sources, destinations, or web applications from malware scanning.
Malware Policies
n "About Malware Scanning" on page121
n "ProtectYour Network From Web Threats" on page126
n "Threat Protection Policy Editor" on page128
n "Malware Policy From Risk Score" on page130
n "Exempt a Source From Malware Scan" on page134
n "Exempt a Destination From Malware Scan" on page138
WebIsolation Solution
n "About Web Isolation" on page142
n "Enable Web Isolation" on page146
Policy Guide/Page 120

Symantec Web Security Service/Page 121
About Malware Scanning
The Web Security Service has three levels of malware protection. The first level, Basic, is a tenant of WSS. The second two
require additional licenses and provide deeper malware analysis. The following sections describe these levels for your malware
protection consideration.
Tip:For a client-less option, see "About Web Isolation" on page142.
BaseLevel
Without any additional configuration, WSS provides protection against malware and malicious web content designed to harm
networks or obtain private user information. The service leverages the Symantec WebPulse technology, which is driven by a
community of users that numbers into the tens of millions. As these users browse web content, scanned content receives a
category rating. The database is updated in real time. WSS policy checks against this database.
The default and unalterable Content Filtering policy prevents access to malicious content websites. These blocked categories
are located in these sub-groups:
n Security >Security Concerns: Spam
n Security >Security Threats:Malicious Outbound Data/Botnets, Malicious Sources/Malnets, Phishing, Proxy
Avoidance
n Legal Liability >Liability Concerns: Child Pornography
n No additional configuration is required. WSS does, however, enable you to designate trusted sources and
destinationsthat are never scanned for malware.

Policy Guide/Page 122
In the above example, there are two types of users: standard Employees and a Security Specialist. WSS policy achieves the
following:
n An employee makes a request to a site the service rates as a known Phishing site.
n The Security Specialist operates on a subnet (a Trusted Source), which is used to test anti-virus software, that
bypasses the default content filtering and malware inspection policy.
Basic Level Protection
n ProxySG/Secure Web Gateway
n Dual Anti-Virus Scanning
n Global Intelligence Network
n URL Filtering and Categorization
n Comprehensive Reporting

Symantec Web Security Service/Page 123
n SSL Interception/Policy-Based Decryption
n (Optional) CASB Audit Integration for web application analysis.
Malware Analysis Standard Service
The Malware Analysis Standard Service (MASS) prevents infection from unknown malware. It blocks malicious content in real-
time based on sandboxing resources (Malware Analysis + Content Analysis) that are hosted in Symantec datacenters. This
functionality requires an additional license added to your current WSS account. After this entitlement is added to your account,
relevant Threats report provides indications of which technology blocked the malware:the standard service ThreatProtection
(AV) or Malware Analysis (sandbox).
MASSLicense Protection
In addition to the Base Level, the MASS license provides the following malware analysis.
n Static Code Analysis
n YARA Rules Analysis
n Behavioral Analysis
n Emulation of Windows Processes
n Inline, Real-Time Blocking
n File and URL Reputation
Tip:For this initial standard service, the sandboxing results are from scans against exe and dll
content.
MalwareAnalysis Advanced Service
The Malware Analysis Advance Service (MAAS)license adds more malware analysis capability. While the MASS license
provides functionality that always returns results in real-time, the MAAS license adds detonation services that can extend past
the real-time sandboxing period.
If the MASS mechanisms (included in MAAS) do not detect malware, the sample is sent to a datacenter for detonation. If
malicious behavior is detected within the real-time sandboxing period, the service blocks the file and sends the user an error
page.
Because detonation can take longer than the sandboxing period, the service delivers the file to the user
after
this time
while
detonation continues in the background. Any post-download detection triggers an administrative alert (email) with the details of
the potential client infection (if Malware Analysis Notifications are enabled in the portal; see link below).
Supported Common Documents and File Types
n Windows Installers
n MS Word, Excel , PowerPoint , and Visio files/documents
n Adobe Portable Document Format

Policy Guide/Page 124
n Rich Text Format
n Java Archives
n Android Application Packages
n iOS Application Archives
n Debian/iOS
Note: Symantec continues to evaluate and might add more types.
There are no additional configuration options. After the Malware Analysis Standard Service (MASS license) or the Malware
Analysis Advanced Service (MAAS license) is added to your account, the relevant Threats report provides indications of
which technology blocked the malware:the standard service ThreatProtection (AV) or the MASS/MAAS (sandbox).

Symantec Web Security Service/Page 125
Tip:For this initial standard service, the sandboxing results are from scans against exe and dll
content.
Policy Guide/Page 126
ProtectYour Network From Web Threats
Without any additional configuration, the Web Security Service provides a level of protection against malware, or malicious
web content designed to harm networks or obtain private user information. The service leverages the Symantec WebPulse
technology, which is driven by a community of users that numbers into the tens of millions. As these users browse web
content, scanned content receives a category rating. The database is updated in real time. The WSS policy checks against this
database.
The WSS provides various levels of malware protection(add-on subscriptions are required for some features). For other details
about the service levels, including what is blocked per level, see "About Malware Scanning" on page121.
The Policy >Content &Malware Analysis page displays the current protection status and provides basic options.
Content Analysis
The WSS basic malware services block the types of websites that are the source of viruses and other malicious content. The
default and unalterable Content Filtering policy prevents access to malicious content websites. Default blocked categories are
located in the following sub-groups:
n Security >Security Concerns: Spam
n Security >Security Threats:Malicious Outbound Data/Botnets, Malicious Sources/Malnets, Phishing, Proxy
Avoidance
n Legal Liability >Liability Concerns: Child Pornography
n No additional configuration is required. WSS does, however, enable you to designate trusted sources and
destinationsthat are never scanned for malware.
Malware Analysis
For more in-depth malware scanning obtain one of the add-on Malware Analysis licenses.
n The Malware Analysis Standard Service (MASS) prevents first-client infection from unknown malware.
n The Malware Analysis Advance Service (MAAS)adds detonation services that can extend past the real-time
sandboxing period, plus email notifications for post-downloaded threats. To add one or more email addresses, navigate
to Policy >Content &Malware Analysis and expand the Malware Analysis area.

Symantec Web Security Service/Page 127
Enter emails (separated by commas) and click Save.
For full details, see "About Malware Scanning" on page121.
Malware Exemptions andPolicy
You might have a need to exempt some traffic from malware scanning or a specific level of scanning. For example, scanning
interferes with your testing on a specific network segment.
n "Exempt a Source From Malware Scan" on page134
n "Exempt a Destination From Malware Scan" on page138
Use the ThreatProtection Policy Editor to customize your protection strategy.
n "Threat Protection Policy Editor" on page128
With the Advanced Web Security with Risk Controls and Web Applications add-on license, you can allow or block access to
content that has been rated Cautionary Risky, Moderately Risky, or Risky levels. You can also define custom risk score-based
policy.
n "Malware Policy From Risk Score" on page130
Geolocation-Based Polices
If your WSS portal account is provisioned with the Advanced Web Security with Risk Controls and Web Applications add-on
license, you can base malware scanning policies from what country the request originates (AddSources >Geolocation
construct) or to what country the request is destined (Add Destinations >Geolocation construct). See "About Geolocation
Policies" on page156.
Web Isolation
Web Isolation is a client-less solution that enables employees to safely browse the internet on any device using any browser.
See "About Web Isolation" on page142.

Policy Guide/Page 128
Threat Protection Policy Editor
By default, the Web Security Service blocks access to known risky content categories (this varies depending on which Default
Policy level you or another admin selected during the initial configuration process).
Use the ThreatProtectionPolicy Editor to further customize your protection strategy. If you or another admin previously
created applicable lists (such as in the Policy > Object Library), the policies already include them. Each blue link in the editor
enables you to perform changes to that element. For example, you might—
n Elect to have a stronger file type protection strategy for mobile users.
n Allow specific users or groups access to permanently blocked categories.
n Allow access to uncategorized content.
n Define policies that depend on multiple conditions. For example, the rules triggers if for a specific group that accesses
from a specific location (ANDconstruct). You can also create OR constructs.
Tip:If your account has provisioned the Advanced Web Security with Risk Controls and Web
Applications add-on license, you can define policy based on Risk Scores. See "Malware Policy
From Risk Score" on page130.
1. Navigate to Policy >ThreatProtection.
The ThreatProtectionPolicy Editor contains policy rows grouped by A and B.
n A—These rules do not depend on content returned from the destination.
n B—These rules might depend on returned content.
2. Each row labeled with G# has a purpose in its order. Roll over each tool tip icon to understand how the rule interacts
with the overall policy.

Symantec Web Security Service/Page 129
Each blue link enables you to perform changes to that element. If you or another admin previously created applicable lists
(such as in the Policy >Object Library), the policies already include them. For example, the above screenshot has a list
added to the Risky File Type Source Exemptions in rule G4.
3. To create a rule, click Add Rule. The editor displays the constructs page (Conditions and Verdict).
n Click Add Sources, Add Destinations, and Content and Limits to add the elements to the rule. You can create
AND/OR constructs to make the rule conditional on multiple elements.
Tip:For a more detailed tutorial on how to use this editor. See "About the Content
Filtering Rule Editor" on page74.
n The Verdict is the action to take on triggered rules:Allow or Block (WSS displays an exception page on the client
system or device).
Note: If your account has the Web Isolation license, the Block verdict has a sub-
option to Block unless Isolated. Selecting this means traffic that triggers
WebIsolation policy is not blocked by this policy. See "Enable Web Isolation" on
page146.
4. ClickAddRule.WSS places the rule in the correct order.
5. Click Activate.

Policy Guide/Page 130
Malware Policy From Risk Score
The Symantec Global Intelligence Network (GIN) provides datafeeds that contain content category
risk ratings
to the Web
Security Service. The risk rating ranks from 1 to 10 and has the following labels.
Score Description
1-2 Content is Very Likely Safe. Sites have a proven history of proper behavior.
3-4 Content is Likely Safe.Sites are beginning to establish a history of proper behavior.
5-6 Content is Cautious. Possibilities exist that the sites might not be yet be proven to be safe.
7-8 Content is Suspicious. Evidence exists that the sites are possibly malicious.
9-10 Content is confirmed as Malicious.Solid evidence that the sites are malicious.
By default, WSS blocks categories such as Phishing, but other categories can contain malware sources. For heightened
security, many organizations opt to block anything with a risk rating 7 or above. With the Advanced Web Security with Risk
Controls and Web Applications add-on license provisioned to your account, you can use the ThreatProtection Policy Editor to
define more granular risk rating policy.
Consider the following use cases that demonstrate how risk score policy can be of benefit.
n The Marketing group might have a more lenient web access policy applied to it because they browse more for research;
therefore, you want to set its risk score block level to 6.
n You want any request sent to (or from) specific countries to block any risk score of 6 and above.
n Content policy previously blocked the Uncategorized category; however, too many false-positives occurred. Now you
can block all access to the Unrated and other categories that present similar behaviors (for example, Advertising) that
is risk level 5 and above.
n Block specific file types with a risk rating of 4 and above.
n Your security suite includes the Universal Policy Enforcement (UPE) solution. You have created risk rating policy on
your on-premises ProxySG appliance.WSS accepts that policy when delivered from Symantec Management Center.
Defining risk score policy is the same as described in "Threat Protection Policy Editor" on page128. After your account is
provisioned with the Advanced Web Security with Risk Controls and Web Applications add-on license, the editor displays
default rows that contain risk scores.

Symantec Web Security Service/Page 131
By default, WSS provides three Group A rows with Cautionary (6), Moderately Risky (7), and Risky Levels(8-10). By
default, these default risk level rules are set to a Block verdict. If your portal account has the Web Isolation add-on license, the
default for Cautionary (6) and Moderately Risky (7) is Block Unless Isolated.
You can add other constructs to these rows. The exception is FileTypes in Contents and Limits because they rely on
responses from content servers and thus need to be in Group B.
Note: If you or the Admin who performed the WSS account registration process selected High
Security as the Default Policy, the Risk Levels are different.
Each row labeled with G# has a purpose in its order. Roll over each tool tip icon to understand how the rule interacts with the
overall policy.
With the license, the Add Destinations construct now includes a Threat Risk Level element.
Policy Guide/Page 132
n The blue-linked default levels are modifiable (name and level values).
n You can create a new Risk Level object to apply to specific Sources.
Web Isolation Policy Based on Risk Score
If your WSS account has provisioned the Web Isolation add-on license, you can force content with a specific risk score to be
processed in isolation.
RiskScore Reporting
WSS provides several default reports based on risk scores.
On the Report Center page, the Security area provides several default reports.
n Trend of Risk Distribution
n Trend of Overall Risk
n Risky Sites Per Country
n Risky Clients Per Country
n Risk Distribution—Pie chart showing percentage of each rating level for a given time frame.
n Riskiest Users—List of users with highest numbers of requests scored over or equal to Risk Score 7. (PDF report not
available.)
n Risky Sites Not Blocked—Top sites not blocked with score over or equal to 7.
On the Dashboards >Threat Protection page, select risk score-based report applets from the AddReport >Security menu.

Symantec Web Security Service/Page 133
Policy Guide/Page 134
Exempt a Source From Malware Scan
The Web Security Service allows you to exempt web requests from specific sources from malware scanning. Furthermore, you
can select the level of scanning for those sources.
Exemptable Sources
You can exempt:
n Specific IP addresses and subnets—Use Case:You might have a list of client systems whose responsibilities exempt
their requests from WSS malware scanning. For example, you have a Security Specialist who requires unabated web
access. There are two methods:manually enter anIPaddress or subnet or define a list in a text file (one entry per line)
and import that list.
n Locations—If you do not require granular exemptions, you can exempt an entire location. For example, a micro-branch
office connects to WSS through the Explicit Proxy access method.
n A client IP address or subnet listed as a Trusted Source also causes WSS to disable Protocol Detection for requests
coming from this Trusted Source. Even if SSL Interception is enabled, the service does not intercept any HTTPS (SSL)
traffic requested by this source, which might cause unintended policy misses.
Exemption Levels
By default, WSS exempts the source from the following malware scanning processes.
n
Anti-virus engine scanning
n Malware Analysis (if the account has the MASS or MAASlicense)
If the account has the MASS or MAASlicense, you can elect to not apply Malware analysis or Malware analysis and Anti-
virus engine scanning.
Procedures
1. Navigate to Policy >Content &Malware Analysis.
2. Expand the Scanning Exemptions area.
3. The interface provides the following methods to add exempted sources.
n Click the Trusted Source IP/Subnets link—This is the default link/object.
n Click any other existing link created by you or another WSS Admin.
Either of these display the Object dialog from which you can add or import trusted (exempt) IPaddresses.
n Click Add to create a new object. From this dialog, you can also add new IP addresses and locations plus create
combined objects from existing objects. The remainder of this procedure demonstrates this method.
4. (Option 1) Create a combined object from existing objects. If you created custom objects in the Object Library (Policy >
Object Library), they are available for selection.

Symantec Web Security Service/Page 135
a. Click Add. The portal displays the AddExempted Sources dialog.
b. Select existing objects.
c. Click Add to move them to the to be added field.
d. Verify/select the malware scanning levels that are
not
performed against this source.
e. Click Add.
5. (Option 2)Create a new object.
a. Click Add. The portal displays the AddExempted Sources dialog.
b. In the dialog, clickNew and select what to add.

Policy Guide/Page 136
n Location or IP/Subnet List—Displays entries from your Object Library or create a new list from
selections; can also select entries detected by an already-run report.
n Location—Define a new location and Access Method. For example, you want to test and need to create
an Explicit Proxy location.
n IP/Subnet—Add or import IP addresses.
c. ClickSave.
d. Add more objects or click Add.
6. Click Activate.
Change Exemption Scanning Level
For any exempted source, you can change the Malware Scanning Level, which are described in "Exemption Levels" on
page134.
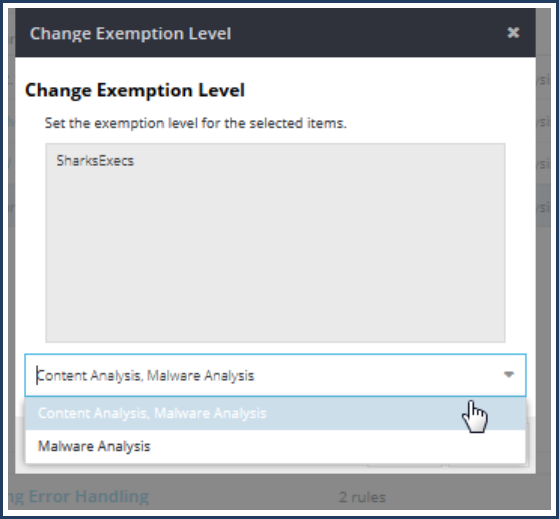
Symantec Web Security Service/Page 137
a. Select a source object.
b. Click Change Exemption Level.
c. The dialog contains a show selected... link, which displays all of the objects in the current rule. The screenshot above
reflects this selections.
d. Select a different level and click Save.
e. Click Activate.
Next Step
n "Exempt Files From Error Handling" on page141.
n Return to "ProtectYour Network From Web Threats" on page126.
Policy Guide/Page 138
Exempt a Destination From Malware Scan
The Web Security Service allows you to exempt web requests from specific sources from malware scanning. Furthermore, you
can select the level of scanning for those sources.
Exemptable Destinations
You can exempt:
n Specific IP addresses and subnets—Use Case:Your employees routinely access information stored on an external
server that is not otherwise connected to the Internet.
n Domains/URLs—Use Case:Your employees routinely access information from a secure partner site.
n Categories—Use Case:You have a collection of categories that you want scanned only for risky files.
n Web Applications—Use Case:You feel financial applications, such as E*Trade, do not require malware scanning.
Exemption Levels
By default, WSS exempts the destination from the following malware scanning processes.
n
Anti-virus engine scanning
n Malware Analysis (if the account has the MASS or MAASlicense)
If the account has the MASS or MAASlicense, you can elect to not apply Malware analysis or Malware analysis and Anti-
virus engine scanning.
Procedures
1. Navigate to Policy >Content &Malware Analysis.
2. Expand the Scanning Exemptions area.
3. Click the Destinations tab.
4. The interface provides the following methods to add exempted sources.
n Click the Trusted Destination IP/Subnets, Domains/URLs, or Web Applications link—These are default
links/objects.
n Click any other existing link created by you or another WSS Admin.
Either of these display the Object dialog from which you can add or import trusted (exempt) IP addresses.
n Click Add to create a new object. From this dialog, you can also add new IP addresses and locations plus create
combined objects from existing objects. The remainder of this procedure demonstrates this method.
5. (Option 1) Create a combined object from existing objects. If you created custom objects in the Object Library (Policy >
Object Library), they are available for selection.

Symantec Web Security Service/Page 139
a. Click Add. The portal displays the AddExempted Destinations dialog.
b. By default, the dialog displays all object types.To narrow the field, select a type from the All Types drop-down list.
c. If you know the name of the object, enter it (or any other keyword) in the search field.
d. Select existing objects.
e. Click Add to move them to the added field.
f. Verify/select the malware scanning levels that are
not
performed against this source.
g. Click Add.
6. (Option 2)Create a new object.
a. Click Add. The portal displays the AddExempted Destinations dialog.
b. In the dialog, clickNew and select what to add.

Policy Guide/Page 140
n Category/URL/IPSubnet/Web Application List—Displays entries from your Object Library or create a
new list from selections; can also select entries detected by an already-run report.
n URL or IP/Subnet—Add or import URLs or IP addresses.
c. ClickSave.
d. Add more objects or click Add.
7. Click Activate.
Next Step
n "Exempt Files From Error Handling" on page141.
n Return to "ProtectYour Network From Web Threats" on page126.

Symantec Web Security Service/Page 141
Exempt Files From Error Handling
Some files are rejected by ICAP error detection based on their type. For example, malware scanning routinely rejects password-
protected archives. The Web Security Service allows you to exempt specific file types from ICAPerror handling and allow them
to continue to the client.
Tip:Currently, PasswordProtectedArchives are the only supported type. Future service
updates will add more types.
1. Navigate to Policy >Content &Malware Analysis.
2. Expand the Scanning Error Handling area and click Add Scanning Error Exemption. The portal displays the
Exemption Rule dialog.
3. (Optional) Click Add Sources and define that construct.
4. (Optional) Click Add Destinations and define that construct.
5. ClickAdd Error Type. Currently, onlyAddPassword Protected Archives is available. Click it and click Save.
Example rule:
6. ClickAdd Rule.
7. Click Activate.
Policy Guide/Page 142
About Web Isolation
Web Isolation is a client-less solution that enables employees to safely browse the internet on any device using any browser.
The zero footprint negates the need for software installation on the clients. The Symantec Web Isolation feature requires a
license. If after reading this section you want to enable this Web Security Service feature, contact your Symantec sales
representative.
What is Web Isolation?
IT departments invest large amounts of resources to protect employees and assets from malicious activity. The most common
element of cyber-security solutions is detection. Anti-virus/malware, network sandboxes, next-generation firewalls, web
application firewalls—all depend on detection. In some cases, such as sandboxes, notification of malicious content arrives to
the admin after the user has received the content because of the time required to ascertain the verdict. Detection of threats
through IOCs and other signatures is necessary to protect against known threats, but in the arms race to apply new
attack/exploits, detection by itself is insufficient.
The Symantec Web Isolation solution addresses this security weakness. Instead of relying on malware detection, Web
Isolation protects organizations’ end users from cyber attacks by isolating malware and preventing it from reaching end user
browsers. A common use case is to protect employees who browse uncategorized and potentially malicious sites.
Web Isolation:
n Provides a safe visual stream of the original web site in the user's browser.
n End users browse the site as if the site was running directly in the browser.
n Preserves original browsing experience with full usability and control.
n Only safely rendered information arrives at the user’s browser.
n Web Isolation executes web sessions away from endpoints.
Protect Endpoints from Attack
As stated above, Web Isolation executes web sessions away from endpoints.
n Isolates and then renders websites, emails, and documents as graphics for display on the end user’s browser, thereby
preventing malware from reaching your network and devices.
n Prevents malware and fraud.
n Protects against drive-by infection, malvertising, and ransomware.
n Blocks malware Command & Control (C&C) and ex-filtration communications.

Symantec Web Security Service/Page 143
Topography
1—Client initiates a web request.
2—You define policy rules that contain Who, FromWhere, To Where, and Verdict criteria. Policy that you define on the proxy
asset in the WSS determines that this traffic—to uncategorized content for example—requires isolation.
3—On the WSS datacenter asset, the Threat Isolation Engine (TIE) in the data center asset runs the website within a secure
disposable container. Simultaneously, WSS returns safely rendered information to users' browsers. This occurs over a secure
web socket. The employee can still scroll, navigate, and enter keystrokes. However, no possibly malicious content, including
browser-based exploits, reaches the client browser.
4—TIE retrieves the requests from the content servers.
5—The client browser is allowed to continued (rendered) site access.
6—IfWeb Isolation detects malicious content:
n Malicious content is blocked by content scanning service.
n Malicious content is eliminated by Web Isolation because of true type validation or rendering failure.

Policy Guide/Page 144
Website Data
The website data remains in the WSS Web Isolation
containerized
environment, which is disposed of after the browser
session.However, you can view reports that track isolation activity.
About the Two Web Isolation License Types
As previously stated, the Web Isolation feature requires a Symantec add-on license. The license is available in two levels.
n Selective Isolation—Allows for about 5% of web traffic per subscribed seat for isolation. The Selective Isolation license
must apply to all seats in your WSS contract.
n Full Web Isolation—You can extend this license to some or all subscribed seats. Grants 100% isolation per subscribed
seat.
Both licenses provide Risk Level-based policy (Threat Level Risk object in the Destinations construct).
Contact your Symantec sales representative.
Tip:An expired Web Isolation license results in the Web Security Service ignoring the rules
defined in the policy editor.
Geolocation—The Advanced WebSecurity Add-On
If your WSS account has provisioned the Advanced Web Security with Risk Controls and Web Applications add-on license,
you gain isolation based on geolocation Sources. For example, you want the WSS to isolate all traffic when the request
originates from specific countries (applies to non-fixed Locations only). See "About Geolocation Policies" on page156.
About Web Isolation and UPE
If you are using Symantec Management Center to manage WSS policy (the Universal Policy Enforcement solution), you can
add policy that directs susceptible traffic to Web Isolation. See "About Web Isolation With UPE" on page151.
About Web IsolationOperations
Use Cases
n By default, Web Isolation policy applies to the To Where policy to the Uncategorized and/or Suspicious categories.
n Document isolation occurs on files that originated in browsing sessions.
Support
Minimum compatible browser versions:
n Chrome 56
n Edge 38
n Firefox 54
Symantec Web Security Service/Page 145
n Internet Explorer 11
n Safari 11
Supported Operating Systems:
n Windows 7+
n Mac OS Sierra+
Traffic
n Ensure that the WSS root certificate is installed on all clients. For clients with WSSAgent on the endpoints, this is
automatically installed and applied to Internet Explorer, Edge and Google Chrome. If your organization uses Firefox or
another browser that has its own certificate store, this certificate must to be installed directly into that web browsing
application.
n Enable SSLInterception in the WSS portal to enable isolation of SSLtraffic.
n The policy enforcement hierarchy is Block >Isolate >Allow.
If web security policy is to block a category, URLs associated with that category are not susceptible to isolation.
n Currently, DLP and CASB functionalities on isolated traffic might be incomplete.
n Currently, Web Isolation is not available for UniversalPolicy Enforcement (UPE) deployments or on mobile devices.
n Because isolation is serving the site representation over the web socket, policy is not applied to the
content
of the HTML
responses.
n Uploads/Downloads—Isolation traffic ignores the following operations.
o
Block file download from a specific URL / category.
o
Block file upload to a specific URL / category.
o
Threat prevention exemption based on destination address.
n If your organization uses Skype for Business (SfB) under the following conditions:
o
You have a private SfB server.
o
SSLInterception is enabled.
Then you must bypass the private URLs for SfB/Lync from SSL interception. If you do not, the app hangs.
Policy Guide/Page 146
Enable Web Isolation
Web Isolation protects organizations’ end users from cyber attacks by isolating malware and preventing it from reaching end
user browsers.
Prerequisite—Obtain License
Web Isolation requires one of the add-on licenses.
n Selective Isolation—Allows for about 5% of web traffic per subscribed seat for isolation.
n Full Web Isolation—You can extend this license to some or all subscribed seats. Grants 100% isolation per subscribed
seat.
Prerequisite—Install Root Certificate
n Ensure that the WSS root certificate is installed on all clients. For clients with WSSAgent on the endpoints, this is
automatically installed and applied to Internet Explorer, Edge and Google Chrome. If your organization uses Firefox or
another browser that has its own certificate store, this certificate must to be installed directly into that web browsing
application.
You can download the certificate from the SSLInterception page or the Policy >Web Isolation page.
Optional Prerequisite—Enable SSL
n To isolate HTTPS traffic, enable SSLInterception(Policy >TLS/SSLInterception).
Examine Encrypted (HTTPS) Traffic
Optional Prerequisite—Custom Lists
Use the Policy >Object Library to define list objects—such as user/group lists, categories, destinations—to be used in
ThreatIsolation policy.
Reference—EgressIP addresses
If you have firewall rule considerations, refer to the following articles.
The Americas:https://knowledge.broadcom.com/external/article?articleId=167190
EMEA:https://knowledge.broadcom.com/external/article?articleId=168147
APAC:https://knowledge.broadcom.com/external/article?articleId=168148
Procedure
Tip:The following procedure demonstrates defining policy that applies Web Isolation.
Performing the same steps, you can also define policy that exempts traffic from Threat
Isolation.

Symantec Web Security Service/Page 147
Step 1—Enable Web Isolation
1. Navigate to Policy >Web Isolation.
2. Toggle to Enabled.
Step 2—Define an Isolation Policy Rule
1. Click Add Rule. The editor displays the constructs page (Conditions and Verdict).
2. Click AddSources.
For example, you want Web Isolation applied to allUnauthenticated Users and specified Groups.
Tip:You can also create AND conditions, which means the rule triggers when both
conditions are met.
Click Save.
3. Click AddDestinations.

Policy Guide/Page 148
For example, you want to add Social Networking categories.
4. The final page, Verdict, defines the Web Isolation action.
n Isolate— WSS executes the web request in a secure, isolated environment and performs Web Isolation malware
scanning.
n No Isolation— WSS bypasses Web Isolation and serves the response as the full web content.
5. Click AddRule. WSS adds the Web Isolation policy rule.
6. ClickActivate to enable the rule.
Isolation Based on Risk Scores
If your WSS account has provisioned the Advanced Web Security with Risk Controls and Web Applications add-on license,
you can force content with a specific risk score to be processed in isolation.

Symantec Web Security Service/Page 149
Monitor Licensed Capacity
As the service begins to process web traffic and perform WebIsolation, your portal account tracks the activity. You can review
the amount of Web Isolation that has occurred against the capacity deemed by your license.
In the upper-right corner of the Web Isolation page, click the highlighted percentage element. The portal displays the Isolation
License Details dialog.
The above screenshot reflects a newly activated license. As more activity occurs, the Projected IsolationUsage area
expands with more data. Roll over graph elements for more data.
Web Isolation Reporting
As traffic begins to undergo Web Isolation, you can review numerous related reports.These reports are on the Report Center
page.
Policy Guide/Page 150
Skype for Business Issue
If your organization uses Skype for Business (SfB) with the following deployment:
n A private SfB server; and
n This SfB server is susceptible to traffic isolation;
Then you must exempt the private SfB/Lync URLs from Web Isolation policy to prevent the SfB from becoming unresponsive.
Add a Do Not Isolate rule as described in Step 2.
Symantec Web Security Service/Page 151
About Web Isolation With UPE
Web Isolation is a client-less solution that enables employees to safely browse the internet using any browser.
WSS supports integration with Symantec Management Center in a solution called Universal Policy Enforcement (UPE). This
allows you to author policy locally (with ProxySG appliance/Management Center) and determine which traffic goes to WSS
where the centralized, cloud-based policy implements Web Isolation.
Technical Requirements
Before implementing the policy provided in this topic, ensure the following technical requirements are met.
n You have an existing Universal Policy Enforcement (UPE) implementation; that is, the Visual Policy Manager (VPM) has
policy designated for WSS upload. This topic does not contain initial UPE configuration procedures.
n Your WSS has the Web Isolation license (Selective or Full).Without the license, the policy objects are suppressed.
Limitations
n The user and group names in UPE policy must match the user and group names authenticated in the WSS.
Supported Deployments
There are two deployment variations to achieve WebIsolation through UPE.
Deployment Use Case—Existing Web Isolation On-Premises/Service
In this deployment, there is an existing Web Isolation solution that is either an on-premises Symantec Web Isolation platform or
a Symantec Web Isolation service account. Policy on the Symantec Secure Web Gateway determines what traffic is
susceptible to isolation. You want to use Management Center to push that existing Web Isolation policy to the WSS.

Policy Guide/Page 152
A—Web Isolation on-premises deployment:a Symantec SecureWeb Gateway appliance (ProxySG or ASG) interacts with
either an on-premises, dedicated Symantec Web Isolation platform or a Web Isolation service.
B—The WSS interacts with a Symantec Web Isolation cloud service (dedicated or shared).
1—The Admin uses the Web Isolation Management UI to determine which traffic is susceptible to isolation based on criteria
such as risk score, category, destination. The Management UI generates a SecureWeb Gateway policy template. The Admin
uses Management Center to push that template to the WSS.
2—An on-site employee issues a web request that triggers WebIsolation.
3—The Threat Isolation Engine (TIE) in the data center asset runs the website within a secure disposable container.
4—The client browser is allowed to continued (rendered) site access while content scanners perform.
5—In the above example, remote clients connect to the WSS. The same traffic is sent to Isolation based on the defined criteria
(flow step 1). The Web Isolation service performs the same disposable container and rendered site tasks. You might have also
on-premises connections, such as from an IPsec or explicit proxy location.
Note: The WSS can forward to only the Web Isolation cloud service. Forwarding to an on-
premises environment is not supported.
Perform This Option?
As mentioned above, the Web Isolation platform has the policy (Content Policy Language—CPL). The Symantec Web Isolation
platform documentation has more details about how to retrieve this.

Symantec Web Security Service/Page 153
n https://techdocs.broadcom.com/content/broadcom/techdocs/us/en/symantec-security-software/web-and-network-
security/web-isolation/1-0.html
n The chapter is
Integration with a Downstream Proxy
.
Deployment—WSS Web Isolation Policy
In this deployment, you do not have any existing proxy forwarding to an isolation product. You want to solely leverage the WSS;
however, you are using UPEto manage WSS policy and want to include Web Isolation.
A—Web Isolation deployment:The WSS interacts with a Symantec Web Isolation cloud service (dedicated or shared).
B—Symantec Management Center determines which traffic goes to the WSS.
1—The Admin adds an isolation policy template to a CPLLayer and determines which traffic is susceptible to isolation based on
criteria such as risk score, category, destination. The Admin uses Management Center to push that template to the WSS.
2—An on-site employee issues a web request that triggers WebIsolation.
3—The Threat Isolation Engine (TIE) in the data center asset runs the website within a secure disposable container.
4—The client browser is allowed to continued (rendered) site access while content scanners perform.
5—In the above example, remote clients connect to the WSS. The same traffic is sent to Isolation based on the defined criteria
(flow step 1). The Web Isolation service performs the same disposable container and rendered site tasks. You might have also
on-premises connections, such as from an IPsec or explicit proxy location.
Perform This Option?
n Proceed to "Web Isolation PolicyTemplate" on page154.
Policy Guide/Page 154
Web Isolation PolicyTemplate
As described in "About Web Isolation With UPE" on page151, you can use Symantec Management Center add policy that
dictates the traffic that the Web Security Service sends to Web Isolation. This solution applies if do not otherwise have a
current on-premises Symantec Web Isolation platform.You must implement a policy template.
Technical Requirements
Before implementing the policy provided in this topic, ensure the following technical requirements are met.
n You have an existing Universal Policy Enforcement (UPE) implementation; that is, the Visual Policy Manager (VPM)
has policy designated for WSS upload. This topic does not contain initial UPE configuration procedures.
n Your WSS has the Web Isolation license (Selective or Full).Without the license, the policy objects are suppressed.
About the PolicyObjects
Two filter objects (conditions) comprise the policy that determines what traffic is susceptible to routing to the WSS for possible
Web Isolation. These conditions are called IsolationMatchCriteria.Both are required as part of the policy.
n <Proxy>layer—Isolation_CondWebIsolationMatchCriteriaWebAccess
n <Forward>layer—Isolation_CondWebIsolationMatchCriteriaForwarding
Each layer evaluates each condition to determine if traffic is to be isolated.
UPEand Web Isolation Policy Template
1. Use Management Center to access theVPM.
Create a new CPL layer and name it (for example, Web Isolation).
2. Copy the policy template below to a file.
3. Paste the policy into the layer (or in a notepad first to refine, then copy over).
4. Modify the policy to match your testing or solution goals.
5. Save the layer and Install the policy. Distribute to the appropriateSecure Gateway appliances.
Template
You must use the same criteria in each condition (WebAccess and Forwarding). Also, the Isolation_
CondWebIsolationMatchCriteriaWebAccess object must use url gestures and the Isolation_
CondWebIsolationMatchCriteriaForwarding object must use server_url gestures.
;; Begin Template
#if enforcement=wss
define condition Isolation_CondWebIsolationMatchCriteriaWebAccess
;url.threat_risk.level=7..10
;url.category=("Malicious Outbound Data/Botnets","Suspicious")
;url.domain="malicious.com"
;authenticated=yes
;client.address=192.168.10.0/24
;authenticated=yes url.category=("Malicious Outbound Data/Botnets")
end
Symantec Web Security Service/Page 155
define condition Isolation_CondWebIsolationMatchCriteriaForwarding
;server_url.threat_risk.level=7..10
;server_url.category=("Malicious Outbound Data/Botnets","Suspicious")
;server_url.domain="malicious.com"
;authenticated=yes
;client.address=192.168.10.0/24
;authenticated=yes url.category=("Malicious Outbound Data/Botnets")
end
; This should be conditioned but is required for Isolation
<SSL-Intercept> condition=Isolation_CondWebIsolationMatchCriteriaWebAccess
ssl.forward_proxy(https)
#endif
;; End Template
The #if enforcement=wss clause ensures this code block is only applicable to WSS deployment. The conditions are tests for
routing to the WSS Isolation facility.
Notice that all of the criteria gestures are commented out with a semi-colon ;. You must elect which ones to enable(delete the ;)
and edit the line to craft your policy. For example, the template sends the Malicious Outbound Data/Botnets and Suspicious
web categories to WebIsolation. You can replace those or add additional per the format.
About SSLInterception of Mobile Traffic (UPE)
WSS provides a policy wizard that enables to you to determine which traffic is susceptible to SSLInterception. You can define
SSLpolicy specifically for traffic generated from mobile devices. If you have enabled SSLInterception globally (without
exceptions),
The best practice is to disable interception of mobile device traffic to avoid known issues caused by app use of locked/pinned
certificates.
Create a pre-defined object:
define condition WSS_AccessViaMobile
#if enforcement=wss
client.location.access_type=mobile_device
#endif
End
Add an SSL layer condition:
<SSL>
Condition=WSS_AccessViaMobile ssl.forward_proxy(no)
About FailureModes
By default, the Web Isolation forwarding policy is Fail Closed. That is, if the forwarding process cannot connect to the Web
Isolation service, the request is refused and the client receives an exception notification.
You can elect to set to Fail Open. However, be advised that it will difficult to distinguish whether or not a browser is operating in
isolation.
<forward>
forward.fail_open(yes) ; UPE isolation will be fail open

Policy Guide/Page 156
About Geolocation Policies
If your Web Security Service portal account has the Advanced Web Security with Risk Controls and Web Applications add-on
license, the Source and Destinations constructs in the Content Filtering and ThreatProtection policy editors contain the
Geolocation construct. This allows you to create policy based on from what country or to what country a content request
occurs.
Tip:Geolocations are supported with the Universal Policy Enforcement (UPE) solution if the
on-premises ProxySG also is provisioned with the correct license.
Supported Methods
Because of how WSS determines the geolocation (country), this policy is best suited for the following connectivity methods.
n Explicit Proxy
n Mobile Devices (iOS, Android)
n WSSAgent and SEP clients
n Roaming Captive Portal authentication option
Be advised of the following details.
n Sources—If the connectivity method is Firewall/VPN or Proxy Forwarding, WSS receives the IP address of the client
system; therefore, the service cannot properly determine the geolocation. For these methods, define policy based on the
fixed locations (as defined on the Connectivity >Locations page).
n Destinations—WSS determines the geolocation based on a DNS resolution to an IP address. If the destination IP
address resolves to a different IP address for the same URL, a different policy result might occur.
Reporting
WSS provides pre-defined geolocation reports based on Sources only. You can create custom reports to see results based on
Destinations.
Exception Pages
When a client request triggers a policy rule, the WSS displays an exception page.

Symantec Web Security Service/Page 157
n The exception details includes the source (Client Geolocation).
Tip:To provide Server Geolocation, create a custom exception page. See "Customize the
Response Pages" on page194.
n The Error ID item informs you what policy rule triggered the exception.
o
In the above example, Content Filtering (CF) rule G1 is the trigger.
o
ATP-## indicates a Threat Protection a rule.
User Privacy
The add-on license allows you to suppress personal information based on geolocation. See Suppress Personal Information From
Access Logs.
Define Policies?
n "Create Custom Content Filtering Rules" on page78
n "Threat Protection Policy Editor" on page128
n "Enable Web Isolation" on page146
Symantec Web Security Service/Page 159
About the Cloud Firewall Service
The rapid move of infrastructure from on-premises to the cloud brings the need to secure all internet-bound traffic, including
traffic from non-standard ports. The Cloud Firewall Service (CFS), a multi-tiered licensed component of the Web Security
Service, provides next-generation firewall capabilities and extends network security beyond the standard web ports (80/443).
The CFS enables you to define firewall policies to control all TCPor UDP traffic based on IPaddresses, destination ports,
locations and users and groups. Accepted traffic continues to WSS security/policy processing functionality. Furthermore, you
can enable ApplicationMonitoring, which allows you to define policies to accept or deny based on specific web applications.
Licensing and Use Cases
The WSS CFS requires one of two available add-on licenses. Selecting the appropriate license depends on your solution goals.
The following sections describe the add-on licenses and what use cases they fulfill.
Policy Guide/Page 160
CFS Standard License
Abstract
n I want to enforce Protocol, Source IP, Destination IP/hostname, and Destination Port firewall
policies across the entire organization.
n I want to apply firewall policies to roaming endpoints (WSSAgent 6.1+ and mobile devices).
n I require the enforcement and user and group-based CFS policies.
Entitles
n Logs all traffic denied by CFS policy. Accepted traffic is
not
logged.
n User and group-based policies.
n User/Group logging controls integrated with user privacy controls.
Cloud Firewall Use Cases
Forward all traffic to the WSS.
n I want to configure my on-premises firewall to point to WSS as the default route for
all
traffic.
Prevent specific traffic types to be used across the organization.
n I want to prevent the use of TCP destination port 22 (SSH).
I have an on-premises security stack and want to reduce complexity by sending each location direct-
to-net with a centralized firewall policy enforcement across the organization.
n I want to remove my branch offices' MPLS nodes and direct the network traffic to WSS and
CFS policies.
Endpoints and Reporting.
n I want to enforce an acceptable network use policy on roaming endpoints.
n I want to have reports for all web (HTTP/HTTPS) traffic and blocked non-web traffic.
Prevent specific users and groups from using specific traffic types within the organization.
n I want to prevent any unauthorized users or groups from using SSH; to enforce data and access
protections.
n I want to limit the use of FTP/SFTP on standard ports to specific users and groups that require
downloading and uploading files.
I have operations already migrated to the cloud. The challenge now is going direct-to-net but allowing
only the required network traffic type based on user and group roles.
n I want to ensure that group-based firewall policies are enforced across the organization
independently of location or endpoint type.
Symantec Web Security Service/Page 161
Endpoints and Reporting.
n I want to enforce an acceptable network user and group-based firewall policies for roaming
users.
n I want to have reports for all users and groups with blocked non-web (HTTP/HTTPS) traffic.

Policy Guide/Page 162
CFS Advanced License
Abstract
n I require monitoring and control for applications such as Windows File Sharing; non-web file
streaming; Proxy Avoidance; applications running over dynamic non-standard ports.
Note—Standard applications running on well-known ports might not require this type of
advanced application monitoring and control.
Entitles
n CFS Standard features.
n Application and application category-based policies.
n All traffic and applications from non-standard web ports are logged for information and reporting.
Note: Traffic through standard web ports are logged in the WSS web
access logs;
not
the CFS.
Application Monitoring Use Cases
Prevent specific applications or application types to be used by certain users and groups at the
organization.
n I want to prevent any unauthorized users and groups from using SSH even if they are not using
standard TCP port 22.
n I want to permit the use of FTP/SFTP for specific users and groups that require downloading
and uploading files even if some of the FTP/SFTP servers are not using standard ports.
I have operations already migrated to the cloud. The challenge now is going direct-to-net but allowing
only the applications the organization has licensed or purchased.
n I want to ensure sure that the organization’s endpoints are using only the Outlook desktop
application for Office 365 and have no communications with other unauthorized mail services.
Extend the on-premises firewall policies to roaming users; enforce differentiated firewall polices per
user types and groups and also per application.
n I want to enforce user and group-based firewall policies to the organization’s roaming users but
also prevent them from using unauthorized applications, such as BitTorrent.
Correlate the impact of specific applications used by certain users and groups.
n I want detailed reports on users and groups that have permissions for testing new applications.

Symantec Web Security Service/Page 163
Supported Connectivity Matrix
Supported
Connectivity
Methods
n VPN/IPsec
n WSSAgent
6.1+
n Cloud
Connect
Defense
(CCD)
n Mobile
Devices
(unknown
locations)
n SDCloud
Connector
LimitedSupport n Explicit
Proxy over
IPsec
Destination IP or port-based firewall policies are not supported because the CFS sees
connection to the proxy in the datacenter; not to the destination.
Not Applicable
Connectivity
Methods
n SEP Traffic
n Explicit
Proxy
n Proxy
Forwarding
When CFS is enabled, the CFS ignores traffic from these sources. Policies defined in
the other WSS editors apply.
CFS Traffic Overviews
The following diagrams and descriptions provide high-level details of how the CFS is positioned in the WSS traffic flow.

Policy Guide/Page 164
CFS—No ApplicationMonitoring
A—A client sends a request from a location routed through a firewall device.
n An IPsec tunnel is established.
n The CFS receives the initial packets.
n Authentication identifies the user and group affiliation from the associated client IP address.
B—A client sends a request from a client system with WSSAgent, from a mobile device, or from the Cloud Connect Defense
(CCD) app on a Windows 10 system.
n An IPsec tunnel is established.
n The CFS receives the initial packets.
n Authentication identifies group affiliation from the logged in employee.
C—The CFS applies its policy to check against the requested network services, protocols, and ports.
n If a Deny verdict occurs, the CFS terminates the request and no packets traverse beyond the CFS to the WSS proxy.
n If an Accept verdict occurs , the CFS passes the request to the WSS proxy, which determines the next decision based
on SSL, CASB, Web Isolation, and web use policies). Exception:DNStraffic passes through the WSS proxy asset.

Symantec Web Security Service/Page 165
CFS—With ApplicationMonitoring Policy
Requires the CFS Advanced License
An Application Monitoring policy is enabled.
A—A client sends a request from a location routed through a firewall device.
n An IPsec tunnel is established.
n The CFS receives the initial packets.
n Authentication identifies the user and group affiliation from the associated client IP address.
B—A client sends a request from a client system with WSSAgent, from a mobile device, or from the Cloud Connect Defense
(CCD) app on a Windows 10 system.
n An IPsec tunnel is established.
n The CFS receives the initial packets.
n Authentication identifies group affiliation from the logged in employee.
C—The CFS Application Monitoring module examines packets to identify the requested firewall application. During this
transaction, traffic might be transferred until the application is determined.
n If a Deny verdict occurs, the CFS terminates the request and no packets traverse beyond the CFS to the WSS proxy.
Policy Guide/Page 166
n If an Accept verdict occurs , the CFS passes the request to the WSS proxy, which determines the next decision based
on SSL, CASB, Web Isolation, and web use policies). Exception:UDP and non-DNS traffic passes through the WSS
proxy asset.

Symantec Web Security Service/Page 167
About the CFS Policy Editor
The Web Security Service Cloud Firewall Service (CFS) replicates firewall capabilities and extends network security beyond the
standard web ports (80/443). Through, you can determine what non-web (HTTP/HTTPS) traffic is permitted in your organization.
This policy can be ubiquitous across the whole organization or determined by users, groups, and firewall-detected applications.
n This topic describes the components of the policy editor. After you understand this topic, you can review policy use
cases and examples in the next section.
Technical Requirements
n WSS Admin Access.
n An access control plan to allow or deny internet outbound traffic based non-web ports, network services, sources,
destinations, and locations.
Users, groups, and applications if properly licensed for these elements.
n Authentication—Standard and Advanced license enable user and group-based policies.
o
WSSAgent, CCD, and SEP-Mobile provide identities per connection.
o
Fixed-site IPsec connections require the Auth Connector for domain log in detection.
o
Challenge-based SAML or CaptivePortal authentication requires the IP surrogate option.
n An authentication method is implemented if you are applying policies to specific users or groups.
Limitations
n To properly support domain bypasses, the WSSAgent does not send DNS requests to WSS when CFS is enabled. DNS
requests are sent direct.
n The maximum length of a username string is 50 characters. For example, Domain\UserName.
About theCFS Policy Editor
The WSS CFS policy editor allows you to create custom rules that define what traffic from non-standard ports is allowed to
proceed to WSS for further acceptable use and threat protection.
Note: The policy editor components vary based on the CFS license tier applied to your account.
To view the policy editor, navigate to Policy >Cloud Firewall. The Policy Rules matrix comprises five or six columns depending
on the license tier—an Order column and four or five policy constructs—and a series of rows. The following sections describe
how to interpret the editor and create new rules.
CFS Policy Construct
Policy Rules columns provide options for four constructs that shape the purpose of the rule.

Policy Guide/Page 168
By Column name—
n Sources—
o
Default—Apply to IPaddresses/subnets, fixed IPsec Locations, WSSAgents, and Mobile Users.
o
Standard/Advanced Licenses—Add support for to users and groups.
The default is Any.
n Destinations—Apply to IP addresses/Subnets and Domains. The default is Any.
n TCP/UDP/Network Services—
o
Apply the rule to all TCP, UDP, or both traffic.
o
Apply the rule to well-known network service protocols and ports, such as SSHon port 22.
o
Define a custom service. For example, you want to apply against a custom service running through TCP/UDP on
unique set of ports.
The default is Any.
n Verdict—
o
Accept—The traffic is allowed to proceed through to WSS.
o
Deny—The CFS drops denied packets.
n Application Overrides—
o
Requires the CFS Advanced License; this column is not visible without this license.
o
The CFS examines packets to identify the firewall-detected applications and applies the rule Verdict. However,
you can override a Deny verdict. For example, theMarketing group is denied all applications except for
Facebook. For that group, Facebook traffic is allowed, but still susceptible to use policies as defined in the
Content Filter policy editor.
Global Rules
There are hard-coded rule rows that cannot be deleted. They are designated as G1, G2, , G3, and G4. Primarily, these rules
are in place to enforce pre-defined, default policies. Where applicable for the rule, the columns contain links. Click the link to
display an editor dialog from which you can specify or select policy objects that apply to everyone (unless they are allowed or
blocked by other custom policy).

Symantec Web Security Service/Page 169
n G1—A Deny that blocks all unsupported IP protocols. This rule cannot be modified.
n G2—An Accept rule that exempts specified IP addresses and domains from CFS policies.
n G3—An Accept rule that allows all HTTP/HTTPS traffic that does not match any preceding rules. This ensures the traffic
reaches the WSS proxy and policy assets. This rule cannot be modified
n G4—An Accept rule that allows all traffic that does not match any of the preceding rules. For this rule, you can click the
edit icon and set to Deny, which provides the most heightened security.
In the editor, mouse-over the text bubble icons and the G-numbers in the left column to view these descriptions in text pop-ups.
Create Custom CFS Rules
You will more than likely need to create policy rules that accomplish your CFS goals.
On the Policy >Cloud FirewallService page, verify that the CFS is Enabled.
Tip:This setting globally controls the CFS policy enforcement and allows the quick toggling of
CFS functions during network troubleshooting.
To launch the rule wizard, on the Cloud Firewall Service page click Add Rule.
The Policy Editor enables you to create And/Or constructs. For example, you have a rule where the Sources are either of two
users (an Or construct) if the request from a specific location (anAnd construct).
The Sources Construct
This example demonstrates what you can add to the Sources construct of the rule.
The policy editor is flexible, allowing you to select objects as well as add new objects within.
n Add Users/Groups—This policy applies to specified logged in users and affiliated groups.
n Add SourceIPs—This policy applies to the client IP addresses seen by WSS.

Policy Guide/Page 170
n Add Locations—
n This policy applies fixed IPsec locations as previously defined on the Connectivity >Locations tab.
n Also an option is this policy applies to roaming clients, which can be WSSAgents or mobile devices (from SEP-
Mobile or the Android app).
Select any construct to display its options.
n The editor displays all of the objects that are available for this rule. Select one or more and click the right-arrow to assign
them to the rule.
n You can also click New and select to create a new list or in applicable constructs a new object.
After completing your selections, click Save.
You can also continue to add sources that create an AND construct. Consider the following example.
The Admin added three Source IP addresses, a fixed Location, and two User Groups. To trigger the rule, one match from
each
source must occur.

Symantec Web Security Service/Page 171
The Destinations Construct
As with the Sources construct, you can create AND/OR policies.
Click Add Destinations. Select to what internet elements this rule applies.
n IP/Subnets and Domains—You might have a need to trigger policy when the destination is a specific server, such as a
testing server, or a specific domain (URLs are
not
supported).
n
The Services Construct
The Services construct is where you select network traffic protocols and ports.

Policy Guide/Page 172
All TCP/UDP
You want the rule to apply to TCP, UDP, or both types of traffic from the sources and to the destinations you defined.
Well-Known Network Services
TheCFS editor presents a list of well-known services and associated ports. For example, FTP and SSH.
Click Network Service, then the Well-Known and RegisteredPorts tab.
Custom Services and Port Ranges
If you have a custom service or a service running on non-standard ports, you can define them in the Network Service editor.

Symantec Web Security Service/Page 173
1. Click New.
2. Define the Port/Port Range and select the network Protocol.
3. Click Add and Save.
The Verdict Construct (CFS Default Behavior and Standard License)
Now that you have created the conditions that trigger the policy rule, the final configuration is to instruct the CFS whether to
Accept the traffic into the WSS or Deny the traffic. This is called the Verdict.
The Client Experience
When CFS policy triggers a Deny verdict, what the end user sees on the client varies.

Policy Guide/Page 174
n If it is a simple Deny, the packets are dropped and the client returns a timed out message.
n If an application control is enabled for the rule, the connection might continue until a block is determined.
o
The user might receive an exception page if the connection is HTTP. Otherwise, it cannot be predicted whether
will occur or note; it depends on multiple webpage communication factors.
The Verdict Construct with Application Monitoring (CFS Advanced
License)
If your account is provisioned with the CFS Advanced license, you have the option to enable Application Monitoring, which
examines packets to identify the firewall-detected applications. When enabled, traffic might transfer until the application is
determined and a verdict rendered. With reporting, you can monitor application traffic.
Combine monitoring with deny verdict to create a robust, secure policies. Achieve this by adding Application Overrides. For
example, your organization uses Microsoft Exchange and you do not want any other email category applications to reach
WSS.
1. Click Add App Overrides.
2. Click Cloud Firewall Application.
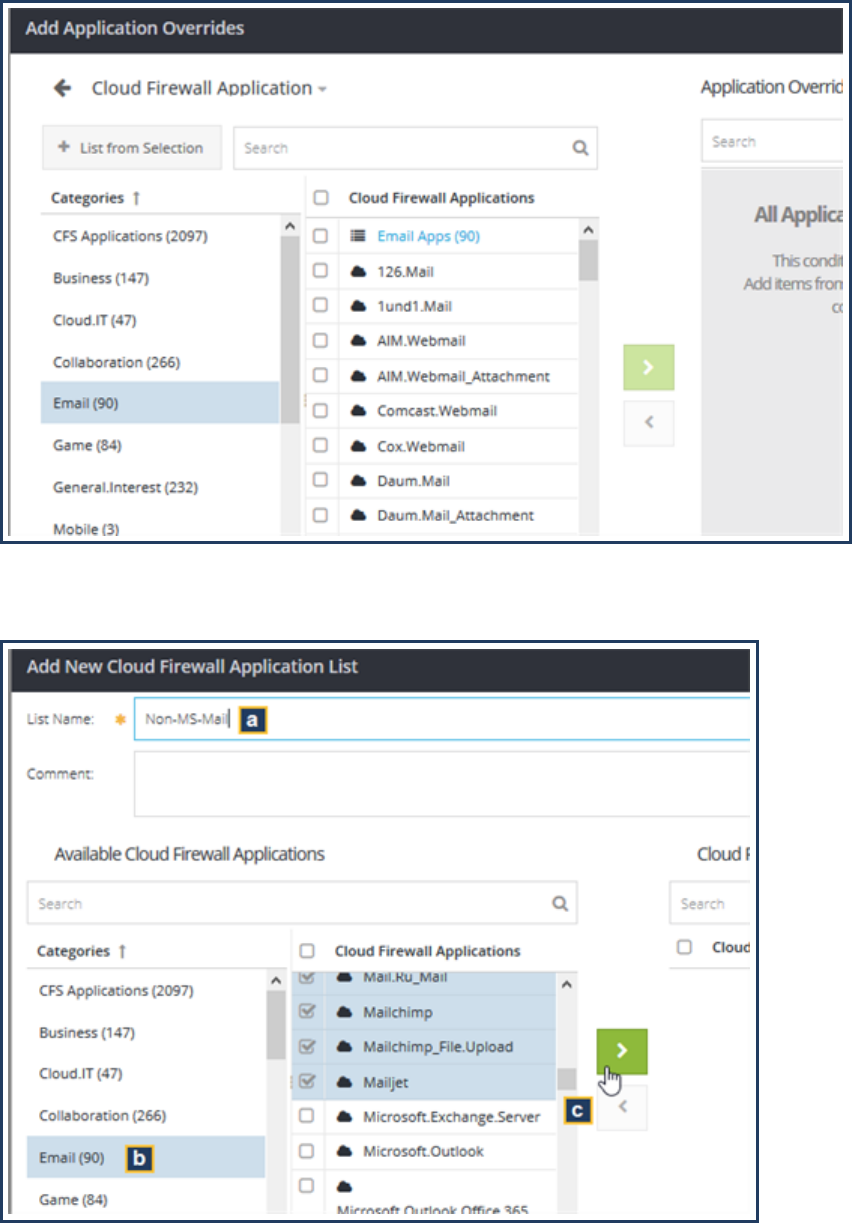
Symantec Web Security Service/Page 175
3. Browse categories and applications. In this example, it is easier create a new List from Selection.

Policy Guide/Page 176
a. Name the list.
b. Select Categories; in this example, Email.
c. Use Control +left-click to select or de-select multiple applications; add to the include column.
d. Save the new list; Save the override list.
Save and Activate the Policy
1. When you are satisfied with the rule, clickSave, which adds it to the CFS rule matrix.
2. Click Activate.
The matrix displays all custom rules between the G2 and G3 global rules.
About Reference Rule Limits
As with other WSS policies editors, you can create and add objects, such as custom User Groups IP address lists. You can
create unlimited objects; however, the portal enforces limits when attempting to add them to CFS rules. The limits are
expressed as a percentage of maximum CFS limit, which by default is 100.
n Destinations (includes both IP addresses and domains): 80
n Users: 50
n Groups: 50
n Services: 10
n Application overrides: 10
If you attempt to add objects beyond the limit threshold, the portal displays an exception dialog.

Symantec Web Security Service/Page 177
CFS Policy Best Practices
n After you update exiting CFS firewall policies, the new policy is applied to
future
traffic flows. All existing
established
firewall sessions are enforced by already matched firewall policies. For example, a user belongs to a group that by policy
is allowed access to Spotify. That user is moved to group that cannot request Spotify; however, the user is still allowed
because the TCP connection is persistent.
n If you define a rule that uses hostname (for example, deny a website domain), be advised that the CFS actually resolves
that hostname into an IP address, which it then uses for run-time traffic enforcement. If you are accustomed to other
WSS policy editors, such as Content Filtering, you might be inclined to add the domain only. For example, you want to
block a site called Example, you typically enter example.com. For CFS policy, the best practice is to define two
destinations: example.com and www.example.com. These two domains open the same page, but might resolve to two
different IP addresses.
o
Also be advised that the hostname condition might not be compatible with large sites such as facebook.com.
Because of geolocation or other processes, DNS might return different sets of IPs to the client and to WSS. Only
use the hostname condition for sites that you are sure will not return conflicting DNS information for a particular
hostname.This might require some testing.
n When designing application-based firewall policies, the accepted application might need to access other applications for
dependent services. For example, you want to deny all applications but accept a single application. Using Facebook as
an example, Facebook Messenger might depend on services provided by Facebook
or
Facebook Apps. The dependent
application must also be accepted for the original application to be accessed.
n When configuring CFS policies, you can specify destinations as DNS domains or IP/subnets. If the DNS domain uses
round-robin DNS or if the DNS domain can be resolved as multiple IP addresses, then the client device and the WSS
asset might resolve the DNS domain as different IP addresses. Consequentially, the firewall policy might not be able to
block access to the destination using DNS domains.
In this scenario, use the more effective CFS application monitoring method to block connections. (This functionality
requires the CFS Advanced License.)

Policy Guide/Page 178
n If you have WSSAgents deployed, you must select the Forward all traffic from all ports to WSS option on the
Connectivity >WSSAgent portal page.
CFS Reporting
CFS reports are driven by CFS log data (separate from the content access logs).
The Dashboards > Cloud Firewall page displays high-level CFS
flow
data. A flow is traffic from any port or protocol received
by the CFS; this includes traffic that might not reach WSS content processing because of a Deny verdict in the CFS policy.
The Reports Center page provides many pre-defined reports designed to present CFS-related data. Given that the CFS
feature potentially allows traffic from all ports, port-based reports provide insight. Traffic by Ports, Blocked Traffic by Ports, and
Unrecognized Traffic by Ports might be a good place to begin analyzing traffic.

Symantec Web Security Service/Page 179
Like other WSS reports, you can drill down, view more details, and apply filters. In a report, the Options dialog (gear icon in
upper-right corner) is you can summarize and filter data.
Policy Guide/Page 180
You can download the CFS access logs to store for compliance or use with other tools.
Privacy
You can configure WSS to suppress some or all user identification information from the CFS Log on the devices in the
Symantec datacenters.
Next Selection
n Proceed to "CFS Policy Planning and Examples" on page181.

Symantec Web Security Service/Page 181
CFS Policy Planning and Examples
The Web Security Service Cloud Firewall Service allows the forwarding of all traffic (web and non-web) to the WSS, which
enables user protection through granular firewall rules enforcement. Before proceeding with this topic, understand the contents
of the following.
n "About the Cloud Firewall Service" on page159 describes the solution.
n "About the CFS Policy Editor" on page167 describes how the editor functions.
Before you begin to define CFS policy, plan out your organization's protection requirements. Within the organization, different
teams or groups likely require access to different ports and protocols. This topic provides planning strategies and use case
policy examples.
Note: The following planning and example information relates mostly to the functionality
afforded by the CFS Standard and Advanced licenses. With the default behavior, you can define
simple, global protocol and port policies.
Plan CFS Policy Enforcement
As network security administrator, you must design firewall policies to meet the needs of different teams. The first step is to
decide who and/or what to protect. Consider defining
security profiles
.
n Do specific users in the organization (from your Active Directory or SAML IdP) require access to specific ports, protocols,
or web applications? For example, a QA engineer requires full access for testing.
n Do groups contains users who share the same security profiles and needs? For example, QA and Dev groups require
access to specific ports, but the non-development groups are to be denied.
n Is policy based on requests from specific network subnets required? For example, network subnet 192.168.0.0/16 is
dedicated to testing web applications.
n Do fixed Locations require policies? For example, a branch location is a test lab that connects to WSS from a location
defined in the portal.
n Determine if the security profiles require Accept or Deny firewall traffic verdicts.
n As with any granular policy, you can have exceptions with each security profile. Refine each by considering differing
needs. For example, a super administrator in a group requires even less restrictive policy.
Example Planning Use Case
Example Corp has two locations.

Policy Guide/Page 182
LOCATION ONE—Headquarters, which has multiple network segments to consider.
n GREEN SEGMENT—The corporate network (192.168.0.0/16), which is the employee path to the internet. CFS policy
requirements—
o
All users allowed to perform any internet requests except for applications that use peer-to-peer file transfers.
o
Users in the TechMarketing group are allowed to use peer-to-peer applications.
n LIGHTBLUESEGMENT—A developer network (10.1.0.0/16) used by some developers. CFS policy requirements—
o
Users are denied all internet sites except a public customer support HTTPS website (1.2.3.4) that hosts a
customer discussions forum.
o
Users in the DevSupport group can access the customer log download site (1.2.3.5) through SFTP.
n BLUESEGMENT—A lab network (10.2.0.0/16) used by developers and quality engineers who perform product
testing. In addition, this lab has an all traffic testbed (10.3.1.0/24) that requires all protocols allowed to the internet.
CFS policy requirements—
o
Users in the Blue Lab network can go to any internet sites through HTTP/HTTPS.
o
For users who have access to the test bed sub-segment there are no protocol restrictions.
n RED SEGMENT—A restricted lab network (10.3.0.0/16) used by developers and quality engineers who perform
product testing. CFS policy requirements—
o
Users in the Red Lab network can go to any internet sites.
LOCATION TWO—A remote Data Center that connects through an IPsec Location named in the WSS portal as RDC.
n This location hosts Example Corp's data analytics engine and connects to a internet cloud service (1.2.3.6) for
periodic data download. The specific protocol used is HTTPS.
n There cannot be any other outbound internet traffic from this remote location.

Symantec Web Security Service/Page 183
Example Policies
After you catalog your network segment planning, you can use the CFS Policy Editor (Policy >Cloud Firewall Service) to
implement the policies. The following policy examples match the use cases in the previous section.
GREENSEGMENT
n IF Source = 192.168.0.0/16
AND
Group = TechMarketing
AND
Destination= ANY and Service= ANY
THEN
Accept
n IF Source= 192.168.0.0/16
AND
Destination = Any
AND
Service = ANY
THEN
Accept
Enable Application Monitoring; override to Deny P2P application category.
LIGHTBLUESEGMENT
n IF Source= 10.1.0.0/16
AND
Destination= 1.2.3.4
AND
Service= TCP/443
THEN
Accept
n IF Source= 10.1.0.0/16
AND
Group= DevSupport
AND
Destination= 1.2.3.5 AND service = SFTP
THEN
Accept
n IF Source= 10.1.0.0/16
AND
Destination= Any
AND
Service= ANY
THEN
Deny
BLUESEGMENT
n IF Source= 10.3.1.0/24
AND
Destination= Any
AND
Service= ANY
THEN
Accept
n IF Source= 10.3.0.0/16
AND
Destination= Any
AND
Service= TCP/[80,443]
THEN
Accept
n IF Source= 10.3.0.0/16
AND
Destination= Any
AND
Service= Any
THEN
Deny

Policy Guide/Page 184
REDSEGMENT
n IF Source= 10.2.0.0/16
AND
Destination= Any
AND
Service= ANY
THEN
Accept
RDC LOCATION
n IF Location = RDC
AND
Destination= 1.2.3.6
AND
Service= TCP/443
THEN
Accept
n IF Location = RDC
AND
Destination= Any
AND
Service= Any
THEN
Deny
Default Deny Policy?
Consider the need to have a default Deny policy for all web traffic not otherwise affected by Accept rules.
Be advised that this rule is quite restrictive (as indicated by the icon/tooltip). But it provides the highest security level as only
traffic that satisfy Accept rules is allowed through to WSS.

Policy: How Do I?
The Web Security Service provides policy options that, mostly, determine how specific web traffic is processed by the service.
This page allows you to navigate to common, specific tasks.
Service
n I want to set captive portal surrogate type and refresh times.
n I want to set authentication policy based on location.
n I want to create custom lists of objects and network elements to use in multiple polices.
n I want to notify users when an exception occurs.
n I want to customize the error page template.
Content
n I want to block specific web application actions.
n I want redirect acceptable web use policy abusers to the company's Employee Handbook.
n I want to enforce safe search engine policy.
User-Related
n I want to assign Reporting Users based on organizational role.
n I want to coach users when they browse to potentially non-productive web content.
n I want to create a policy to block unauthenticated users.
n I want to allow certain people to over rule the blocked content verdict.
n I want to generate instant policy directly from a user or client value in a report.
n I want to create a policy based on usernames that I see in reports.
n I want to restrict when a specific user has access to content.
n I want to define a policy that applies only to my mobile users.
n I want to block specific application actions.
n I want to enforce search engine Safe Search functionality.
Policy Guide/Page 185
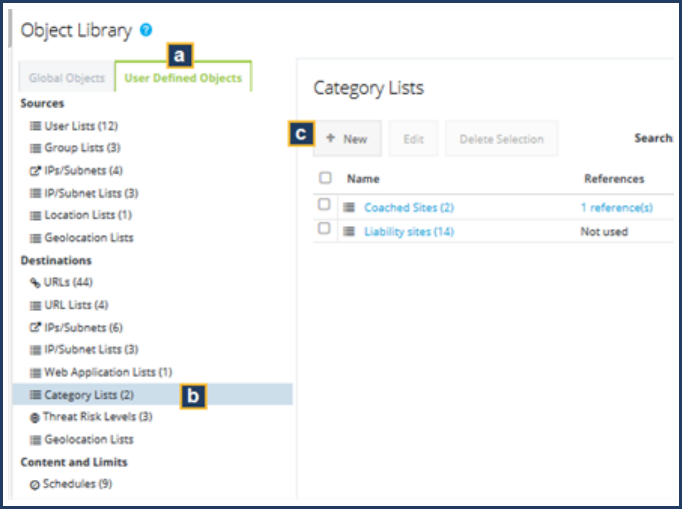
Symantec Web Security Service/Page 186
Define Object Lists to Use in Custom Policy
The Web Security Service policy editors enable you to create or select network objects such as usernames, IP addresses,
URLs, and categories.Amore efficient method is to create objects that contain lists of related values and then select that object
when creating policy.The further advantage is that objects are reusable in multiple policy rules.
WSS provides an Object Library that displays all of the reusable lists—both global and user-defined. It is from here that you also
manage the object lists (create and edit existing).
Use Case Procedure
You want to create a list that combines several time-wasting categories into one content filtering list object for use in a coaching
policy.
1. Navigate to Policy >Object Library.
2. Access the Category Lists dialog.
a. Select User Defined Objects.
b. Select any object. For example, add a new Category List.
c. Click the Add New.The service displays the new AddNew Object dialog.
3. Select the categories to include.

Policy Guide/Page 187
a. Name the object; make the name obvious so that other WSS users understand what it is.
b. (Optional)Enter a Comment that describes the purpose of the object.
c. Select the object elements. This example selects the Non-Productive > Social Interaction category groups.
d. Click Add to move them to the In ThisList area.
e. Click Save.
f. An orange triangle next to the object indicates new objects are in Pending state and remain so until you click
Activate.
4. Navigate to Policy >Content Filtering.
5. Click Add Rule and create a rule that coaches access to these categories.
a. Click Destinations.
b. Click the Category Lists item.

Symantec Web Security Service/Page 188
c. Select the object that you created in Step 3 and click the right-arrow icon.
d. ClickSave.
e. In the Verdict area, Select Allow and with Coach.
f. Click AddRule.
6. Objects rest in pending state until they are added to policy rules.
After you define rules (that contain these objects) in the Content Filtering policy editor, the object library displays the object and
indicates which rule(s) contain the object.

Policy Guide/Page 189
GeolocationObjects
If your portal account has the Advanced Web Security with Risk Controls and Web Applications add-on license, you can use
Geolocation objects (lists of countries). This allows you to create policy based on from what country or to what country a
content request occurs. See "About Geolocation Policies" on page156.

Symantec Web Security Service/Page 190
Modify the Default Response Page
By default, the Web Security Service displays response page to users when the transaction triggers an
exception
event, such as
a policy violation page when a user attempts to access a website or web application protocol that WSS policy is configured to
block. The content of the page includes the result message, such as Access Denied, along with other details, such as the client
IP address and the reason (for example, a blocked content filter category).
n WSS allows you to modify this page, including selecting a color scheme, adding contact information and changing the
displayed logo and company name. For example, add your ITgroup email address so that users can contact IT to dispute
a rating or ask a question about the policy.
n If your WSS account includes the Advanced Web Security with Risk Controls and Web Applications add-on license, the
exception includes the Client Location, or country of origin as determined by the service. For more details, see "About
Geolocation Policies" on page156.
n The Error ID indicates which policy rule triggered the exception. CF-XX is a content filter rule. TP-XX is a threat
protection rule. The exception displays N/A if it cannot determine the rule. Other operations, such a password override,
might cause an N/A.
Tip:You can also modify the template for this page. See "Customize the Response Pages" on
page194.

Policy Guide/Page 191
Additionally, English, French (European), German, Italian, Japanese, and Spanish (European) language web browsers displays
these pages in their respective languages.
Procedure
This task requires WSS portal Admin Role credentials.
1. Navigate to Policy >ResponsePages >Standard.
2. Customize contact information.
a. Select which additional text options to include on the page.In addition to letter and numbers, only spaces and
plus signs(+) are valid characters.
b. Select the page style and color.
c. Click Save.
3. Enter the Company Name field that replaces the current name on notification pages.

Symantec Web Security Service/Page 192
4. (Optional) Change the logo (.png file, 190 pixels x 35 pixels) that displays on exception pages. The default is the
Symantec company logo; however, if your company obtained WSS from a third-party service provider, their logo might
display instead. The logo you add here overrides that configuration.
a. In the Current Logo area, click Change. The service displays Upload Error Log dialogs.
b. Browse to the stored image; select it and click Open.
c. Click Save in the Error dialog.

Policy Guide/Page 193
To revert to the default file, click Change and select Reset.
5. Click Save.
Note: If WSS has other pending policy changes, a dialog displays to inform you of this.
You can accept to activate all pending policy or navigate to the various policy pages and
verify that you want those changes (then return here to save the notification changes).
6. Configure Content Filtering Policy.
Troubleshooting Assistance
You can force WSS to translate exception pages into English regardless of browser language version. The non-English
browsers do not display the site review URL. Temporarily forcing English can aid with troubleshooting, including talking to
Support Personnel who speak only English.
n Select Show English Translation Onlyand click Save.
n When assistance is complete, clear the option.
Symantec Web Security Service/Page 194
Customize the Response Pages
The Web Security Service displays response pages to users when a browsing action triggers an exception, such as a denied
content category. The page contains default information, including the exception reason. You can also select to display
information, such as contact information and a custom logo. These notification options should prove sufficient for most
enterprise requirements. This information comes from a template, which you can also customize.
Portal Location
Policy > Response Pages > Custom
Use Cases
n You do not want the notification page to contain specific elements, such as the logo or contact email.
n You want to change the background color or add additional text to an area on the page.
BestPractices
n Customizing the notification template is an advanced feature. As such, only admin-level WSS users are able to modify
the template contents.
n Have considerable knowledge of HTML and CSS before performing edits beyond simple string replacements.
n Perform only small, deliberate changes to the template rather than recreating a completely new template.
n To avoid display issues, keep the template code compatible with any browser vendor used by employees in your
enterprise.
n Certain sections of the template are critical for the page to function properly with other policy elements, such as the
Password Override feature. Avoid these clearly marked code sections in the template.
n Do not load content from servers that are outside of your control.
n JavaScript is running in the page under the context of the page that was blocked and might in some cases have
access to sensitive user cookies meant to be kept private. For this reason, avoid loading any third-party hosted
JavaScript.
n Requests to other resources (such as images) might have the Referrer HTTP header present from the page that
was blocked, revealing what page the user was visiting when the block page was served. For this reason, avoid
loading anything from a 3rd party server.
n When possible, directly include content in the template rather than hosting it on the Internet. This decreases load time and
guarantees that a resource is reachable.
n Base64 images can be encoded directly in the HTML.
n The template can contain CSS stylesheets.
n WSS displays the exception page for both HTTP and HTTPS connections. If an image (or some other resource) is
referenced in your template using the http:// protocol and the template is used for a page loaded over HTTPS, some
browsers might display a warning to inform the user that insecure content was loaded within a secure page. The same
might apply in the reverse situation where an https:// resource loads on a page over HTTP. For this reason, either

Policy Guide/Page 195
include the content inline as previously mentioned earlier or perform one of the following.
n Host your content both over http:// and https:// and
n Use a protocol-less URL to reference it; for example http://example.com/aResource becomes
//example.com/aResource.
The Editor
To view the Custom Notification editor, navigate to Policy >ResponsePages >Custom.
A—The Preview option allows you to view code changes before they are implemented.
B—Click Show Replacement Variables to display all of the code elements that the service uses to populate data.

Symantec Web Security Service/Page 196
The variables that begin with $(config.) are the ones that comprise the default Error Pages. These are ones that you can
elect to remove from the template.
C—If you run into problems with your edits or you want to start over and create a new template, click Reset to Default HTML,
which reverts the template to its default state.
D—When you click Enable custom error pages, the system might override any custom edits to Policy >Response Pages
>Standard. For example, if you add contact telephone number to the field on that page, but comment out the field in the
Custom template, the service does not display the entered phone number. If you clear the Enable option, the service returns to
the default page and any customizations that exist there.
Examples
The following examples illustrate how you can edit the template.
Add Text
Supplement the notification with custom text. The following example adds a new line to Tech support information drop-down
(accessed by clicking more).

Policy Guide/Page 197
ClickPreview to see how the service will display the page.
Remove an Element
Enter HTML code to comment out an element. For example, you do not want the notification to include detailed transaction
information/link. Locate the element in the template and add the comment out code: <!-- text -->.

Symantec Web Security Service/Page 198
IMPORTANT:Some span tags contain the localize attribute. Regardless of any customized text, this attribute instructs WSS
to overwrite with a localized version of the text (including English). To display custom text in a span, you must remove the
localize attribute. However, doing so prevents localization.
This line retains the default value because of the localize attribute.
<p id="httpCode"><span localize="[techSupport]">Tech support information</span>:$(exception.id)
This line provides the custom text:Tech support information.
<p id="httpCode"><span>Tech support information</span>:$(exception.id)
Customize theStyle
You can enter CSS code to change the appearance of the page. Locate the Symantec styling section.
You can also add JavaScript (above the style section) to add more complex HTML elements.

Policy Guide/Page 199
Provide Browsing Coaching to Users
The Coaching option enables you to display a message to employees when they attempt to browse web content that is not
blocked by Content Filtering policy, yet might not represent the best use of employee time. You elect to not block employee
access to some leisure sites, such as Facebook, but do want to given an indication that spending too much time on these
might draw attention to oneself.
This message informs the employee that their request will be logged and they must acknowledge this before proceeding to the
website. Furthermore, the message suggests that the employee contact IT should they want to dispute the verdict. Currently,
this message applies to all coach-able requests and is not customizable.
Note: For coaching to properly function, browser settings must allow cookies.
1. Navigate to Policy > Content Filtering.
2. Add a rule or Edit an existing rule (click the symbol in the Verdict column). If adding a new rule, click Next until you
reach the Verdict page.
a. Select Allow and select with Coach. The service displays the Coaching Message text. This text is what
employees see.
Symantec Web Security Service/Page 200
b. (Optional) By default, the Coaching Message displays upon first content request and then not again for 60
minutes. Click the Change link to set a different duration: Midnight or End of Session (browser close/reopen).
Click Save (
3. To complete this non-conditional rule, click Finish. You can edit its elements, such as select categories to which
coaching applies.

Policy Guide/Page 201
Policy Example—Prevent Unauthenticated User Access to Content
The Who element enables you to trigger the policy when a content request comes from a specific user, user type, or group,
based on authentication. This example blocks all unauthenticated users (users on the network who did not log in with internal
domain credentials—requires the Auth Connector) from accessing a company-sensitive information on a specific destination
subnet.
1. Navigate to Policy > Content Filtering.
a. Click Add Rule. The service displays the CreateNew Rule wizard.
b. ClickAddSources.
2. Click Add Unauthenticated Users.
3. Click Save.
4. This example prevents access to a specific subnet.
a. Click Add Destinations.
b. Click IP/Subnets.
c. ClickNewIPs/Subnets. Thewizard displays the Add IPs/Subnets page.

Symantec Web Security Service/Page 202
d. Enter the destination location and clickAdd IPs/Subnets.
e. Click Save.
5. For the Verdict construct, click Block.
6. Click Add Rule.
7. The Content Filtering page displays the new rule, automatically ordering it correctly—after other existing Block rules.
8. Click Activate Policy.

Policy Guide/Page 203
Allow Individuals Access to Blocked Content
You might find a need to allow certain individuals access to content that is blocked by policy. For example, you have a subnet
that contains servers with company proprietary information and that destination is a blocked except for a specific group;
however, a contractor not in the group requires access to complete report.
The Verdict construct in the Web Security Service ContentFiltering policy editor allows you to set an override password that
allows users who receive this password to bypass the blocked verdict.
Note: For coaching to properly function, browser settings must allow cookies.
1. Navigate to Policy > Content Filtering.
2. Add a rule or Edit an existing rule (click the symbol in the Verdict column). If adding a new rule, look for the Verdict
construct.
a. Select Block and select Password Override.
b. Click Change. The service displays the Edit Global Password Override Settings dialog.
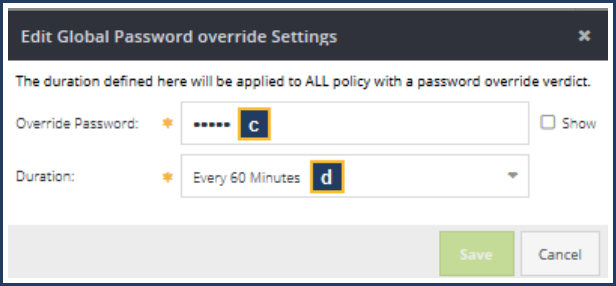
Symantec Web Security Service/Page 204
c. Define the OverridePassword.
d. (Optional) By default, the password prompt displays upon first content request and then not again for 60 minutes.
From the Duration drop-down list, select a different duration: Midnight (00:00) or End of Session (browser
close/reopen).
e. Click Save.
3. To complete this non-conditional rule, click Add Rule. Either delete it or edit its elements, such as select blocked
categories that allow for password override.

Policy Guide/Page 205
Create Policy From a Reported User
As you generate and view Web Security Service reports, you might observe suspicious activity from a client or user and want
to instantly create a policy directly from the report.
This feature is only supported in reports that represent singular users, clients, and so on. Reports that display trends, for
example, do not have this feature. Consider the following two use cases.
Use Case—Infected Client
You are reviewing the Potential Malware InfectedClients report and notice a large amount of suspicious activity from a
specific client. You can instantly apply policy to block that client until you investigate and resolve.
1. Navigate to Report Center and generate the Potential Malware Infected Clients report(from the Security area).
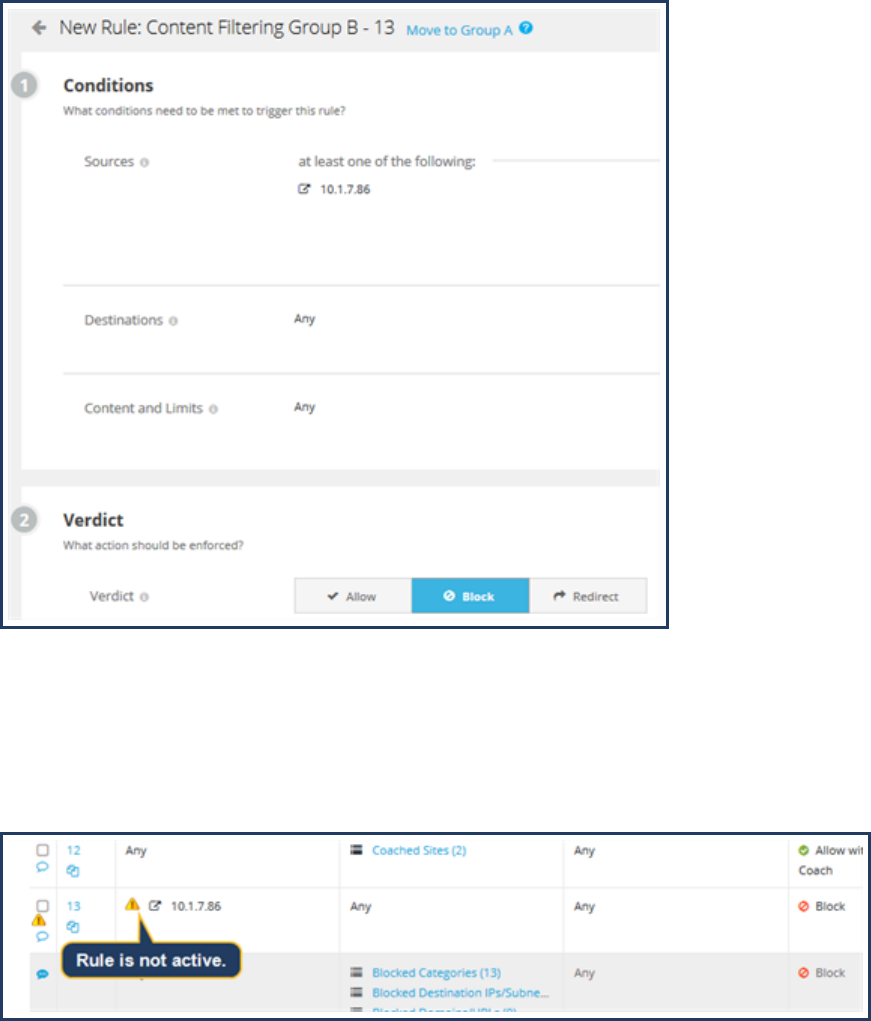
Symantec Web Security Service/Page 206
a. Select graphic element or table row. This is the user or client that requires a policy change.
b. In the table header, select Actions >New Policy Rule. The service displays the New PolicyRule dialog.
2. Define the policy.
The policy editor automatically adds the suspect IP address to the Sources construct. Set the Verdict to Block and click
Add Rule.
3. The policy creation switches the view to the Content Filtering page. Your new rule is viewable in the order added. If
necessary, move it to another spot in the list (click the number link). For example, you want a rule for an individual to be
evaluated before a group rule.
You must click Activate to enable the policy.
4. When you resolve this issue and want to restore the client back into production, return to this page, select the rule, and
click Delete (or you can click Disable to temporarily halt the enforcement of a rule).

Policy Guide/Page 207
Use Case—User Misconduct
When browsing a user report, you notice that a particular user is abusing Web privileges and you want to create a policy that
coaches this person.
1. In Solutions Mode, select Content Filtering >Reports and generate the Web Browsing per User andCategory
report.
a. Scroll and scan the report to identify which users require coaching.
b. Select a row that requires coaching.
c. In the table header, select Actions >New Policy Rule. The service displays the New PolicyRule dialog.
2. Define the policy.

Symantec Web Security Service/Page 208
a. For this example, set the Verdict as Allow With Coach.
b. Click Add Rule.
3. The policy creation switches the view to the Content Filtering page. Your new policy is viewable in its proper place in the
order of policy.
You must click Apply to enforce the policy. Also, to see the current coaching message that is sent to users who trigger
the policy, click the Edit icon in the Verdict column.

Policy Guide/Page 209
Create Policy Based on Reporting Usernames
The Web Security Service Content Filtering policy editor allows you to create policy based on usernames that currently exist
in the reporting database. Rather than using the Auth Connector to synchronize the full user/group list from the enterprise
Active Directory(AD), this subset of username information comes from user credentials, such as the Windows login
credentials. The following use cases illustrate the usefulness of this ability.
Use Case—Small Business/WSSAgent Only
Your WSS account serves a small business, all your clients use the WSSAgent, and you do not need an Active Directory
deployment. You can create global policies for all of these users and create specific policies for a few of the users.
Use Case—ProxySG Appliance WithRADIUSAuthentication
You want to use the ProxyForwarding connectivity method to send some users/groups to WSS, but do not have an
LDAPenvironment. With Reporting Username Policy, you can write policy based on the forwarded usernames because they
are part of the reporting database.
Create A Reporting Username Policy
1. Navigate to Policy > Content Filtering.
a. Click Add Rule. The service displays the CreateNew Rule page.
b. Click Add Sources.
c. Click User.
2. On the first wizard page, Who, click Users FromReporting.
Symantec Web Security Service/Page 210
a. Click From Reporting.
b. Select the Usernames for this policy.
3. Click Save and continue defining the rule as required.

Policy Guide/Page 211
Advanced Policy Example—Set Web Access Times
The When element triggers the policy when it matches a specified time frame. For this example, Chat/Instant Messaging is a
globally blocked category. You decide to have a trial for one week that allows users to use instant messaging, but only Monday
through Friday during the lunch time: 12:00 to 1:30 PM.
1. Navigate to Policy > Content Filtering.
2. Click Add Rule. The service displays the CreateNew Rule page.
a. Click Add Destinations.
b. Click Web Application.
3. Select the Chat(IM/SMS) category (you can also enter chat in the search field).
a. Select the apps to add or the top-of-column option to add all.
b. Click the arrow-icon to add the apps to the construct.
c. Click Save.
4. Create a schedule construct.
a. Click Contents and Limits.
b. Click Schedule.
c. Select New >Schedule.
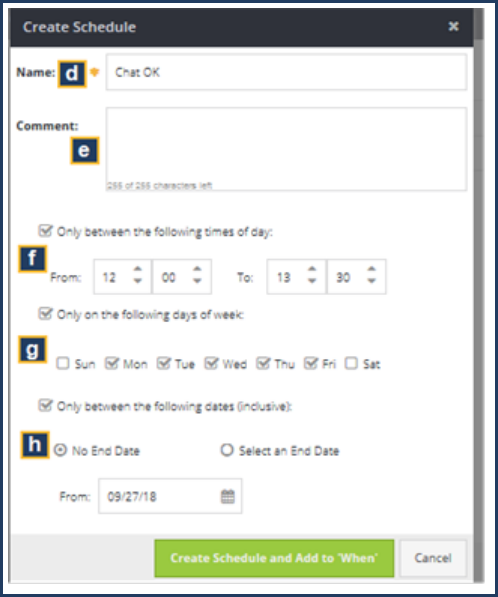
Symantec Web Security Service/Page 212
d. Name the element. (Created elements display in lists and are selectable in other policy rules).
e. (Optional)Provide a descriptive Comment.
f. Only between the following times of day—Select Enable and specify the times. The interface uses a 24-hour
clock; this example sets the From time to 1200 (12:00 PM) and the To time to 1330 (1:30 PM).
g. Only on the following days of the week—This example specifies to allow only on week days. Select Enable and
select Mon, Tue, Wed, Thu, and Fri.
h. Only between the following dates (inclusive)—You can specify No End Date to keep the policy indefinitely. Or
set a data range; for example, you want to test the policy on a trial basis and elicit feedback.
i. Click Create Schedule and Add to 'When'.
j. Click Next.
5. Click Save.
6. Click Add Rule.
7. The ContentFiltering Rules page displays the new rule, automatically ordering it correctly—before the Block rules. A user
attempting to instant message at anytime other than 12:00 to 1:30 matches the global block rule(Group B).
8. Click Activate Policy.

Policy Guide/Page 213
Policy Example—Define Policy For Mobile Users
If you have employees connecting to the Web Security Service from supported mobile devices, you can define a policy that
applies specifically to that access method. For example, you have stringent policy that applies to corporate-owned desktops
and laptops, but want to allow some leniency on allowable Content Filtering categories when the users access from a mobile
device outside of business hours.
1. Navigate to Policy >Content Filtering.
a. Click Add Rule. The service displays the CreateNew Rule wizard.
b. ClickAddSources.
2. Click Add Mobile Devices.
3. ClickNext and continue to define the policy for mobile devices.

Symantec Web Security Service/Page 214
Policy Example—Block Application Actions
You have a set of users for which you want to block specific actions, such as uploading or downloading bandwidth-consuming
content. For example, you do not want your guest WiFi users clogging the wireless resources.
1. Navigate to Policy > Content Filtering.
2. Click Add Rule. The service displays the CreateNew Rule page.
a. Click Add Sources.
b. This example applies to a previously created Location:HQGuestWiFi.
c. Click Save.
3. Click Contents and Limits.
4. Click Actions; the service displays all of the currently supported content actions. Select network-expensive actions,
such as Upload Pictures and Upload Video and click Add.
The default view is all actions for all web applications.To filter the view to display only valid actions for a specific
application, select that application from the Show Actions For drop-down list (or enter text in the field).

Policy Guide/Page 215
5. ClickSave.
6. Click Add Rule.
7. Click Activate Policy.

Symantec Web Security Service/Page 216
Force Safe Searches
Safe Search refers to individual browser settings that allow or disallow displaying links to mature/inappropriate site and image
results when using the browser's search function. The Web Security Service provides the following browser search engine
policy controls.
n Allow all search engines.
n Fully enforce Google's Safe Search mode regardless of the client browser's configuration. Google is the only search
engine that WSS currently fully enforces. If you enable this option, select the policy action the service takes against
requests to other engines.
Tip:When Safe Search is enabled, WSS performs minimal SSLinterception, which is required
for policy enforcement. This is regardless of the current SSLInterception enabled/disabled state
(Policy >TLS/SSLInterception). If your employee base reports certificate warnings, deploy
the WSS trusted certificate. See "Distribute WSS Root Certificate to Endpoints" on page44 and
Examine Encrypted (HTTPS) Traffic.
1. Navigate to Policy > Content Filtering.
2. Click Search Restriction.
3. Select Enabled.
4. Select the action for other search engine requests (as described above).
5. Click Save.
6. Click Activate Policy.

Symantec Web Security Service/Page 218
Reference:Updated Content Filtering Categories
This section lists and describes the Symantec Web Security Service Content Filtering categories. The October 2013 Web
Security Service release (v6.2) contained a category name refresh and added these categories.
n Computer/Information Security
n Internet Connected Devices
n Marijuana
n Piracy/Copyright Concerns
Deprecated in October, 2013:
n LGBT—Sites have been moved to the appropriate content categories (such as Political/Social Advocacy, Personal
Sites, Sexual Expression).
n Pay-to-Surf—Decreased popularity negates the need for a standalone category. Depending on legitimacy, sites go into
Scam/Questionable/Illegal or other business categories.
The definitions below are the most current and might differ from previous descriptions even in cases where the category name
remained unchanged.
https://docs.broadcom.com/docs/webfilter-en.
Name
Previous Name
(if applicable) Definition
Alcohol Same Sites that discuss, encourage, promote, offer, sell, supply, or otherwise
advocate the use or creation of alcoholic beverages—including but not
limited to beer, wine, and hard liquors. It does not include sites that
sell alcohol as a subset of other products such as restaurants or
grocery stores.
Chat (IM)/SMS Chat/Instant Messaging Sites that provide chat, text messaging (SMS), or instant messaging
capabilities or client downloads.
Computer/Information
Security
(New) Sites that provide information or tools for securing or safeguarding
computers, networks, and other data systems. While these sites
provide helpful and legitimate security information to IT professionals,
they also pose a degree of risk because information they provide
might be used to help gain unauthorized access to systems.
Controlled Substances Illegal Drugs Sites that discuss, encourage, promote, offer, sell, supply or otherwise
advocate the use, cultivation, manufacture, or distribution of non-
pharmaceutical drugs, intoxicating plants, solvents or chemicals, and
their related paraphernalia. Typically, these substances have no
accepted medical use and a high potential for abuse. This category
does
not
include alcohol, tobacco, or marijuana sites as these have
dedicated categories.

Policy Guide/Page 219
Name
Previous Name
(if applicable) Definition
E-Card/Invitations Greeting Cards Sites that facilitate the sending of electronic greeting cards, invitations,
or similar electronic messages typically used to mark an event or
special occasion.
Entertainment Same Sites that provide information about or promote popular culture
including but not limited to film, film critiques and discussions, film
trailers, box office, television, home entertainment, music, comics,
graphic novels, literary news, and reviews. This category also includes
entertainment-oriented periodicals, interviews, fan clubs, celebrity
gossip, and podcasts; and music and film charts.
File Storage/Sharing Online Storage Sites and services that provide online file or note storage, file sharing,
synchronization of files between devices and/or network-based data
backup and restoration. These services might provide the means to
upload, download, paste, organize, post and share documents, files,
computer code, text, non-copyright-restricted videos, music and other
electronically formatted information in virtual data storage. Does not
include Web Applications or Media Sharing.
Financial Services Same Sites that provide or advertise banking services, lending services,
insurance services, financial information, or advice on a variety of
fiscal topics including loans. Does not include sites that offer market
information, brokerage or trading services, which are categorized in
the Brokerage/Trading category.
Hacking Same Sites that distribute, promote or provide tools or other information
intended to help gain unauthorized or illegal access to computers,
computer networks, or computerized communication and control
systems. Includes “white-hat” tools used to test the security of existing
systems, e.g., penetration testing tools. Also includes sites with
instructions for creating or distributing malware or information on
performing cyber attacks.
Health Health Sites that provide advice and information on general health such as
fitness and well-being, personal health, medical services, over-the-
counter and prescription medications, health effects of both legal and
illegal drug use, alternative and complementary therapies, medical
information about ailments, dentistry, optometry, and general
psychiatry. Also includes self-help and support organizations
dedicated to a disease or health condition.
Internet Connected
Devices
(New) Sites that allow management and monitoring of or network access to
physical devices connected to the Internet. Such devices include but
are not limited to network infrastructure such as routers and switches,
network-enabled industrial equipment, security cameras, home
automation equipment, and other Web-enabled devices. Also includes
security camera feeds, which are dually categorized as TV/Video
Streams.

Symantec Web Security Service/Page 220
Name
Previous Name
(if applicable) Definition
Malicious
Sources/Malnets
Malicious Sources Sites that host or distribute malware or whose purpose for existence is
as part of a malicious network (malnet) or the malware ecosystem.
Malware is defined as software that takes control of a computer,
modifies computer settings, or collects or reports personal information
without the permission of the end user. It also includes software that
misrepresents itself by tricking users to download or install it or to
enter personal information. This includes sites or software that perform
drive-by downloads; browser hijackers; dialers; any program that
modifies your browser homepage, bookmarks, or security settings;
and keyloggers. It also includes any software that bundles malware
(as defined above) as part of its offering. Information collected or
reported is "personal" if it contains uniquely identifying data, such as
email addresses, name, social security number, IP address, etc. A site
is not classified as malware if the user is reasonably notified that the
software will perform these actions (for example, it alerts that it will
send personal information, be installed, or that it will log keystrokes).
Marijuana (New) Sites that discuss, encourage, promote, offer, sell, supply or otherwise
advocate the use, cultivation, manufacture or distribution of marijuana
and its myriad aliases, whether for recreational or medicinal purposes.
Includes sites with content regarding marijuana-related paraphernalia.
Mixed Content/Potentially
Adult
Open/Mixed Content Sites with generally non-offensive content but that also have
potentially objectionable content such as adult or pornographic
material that is not organized so that it can be classified separately.
Sites that explicitly exclude offensive, adult, and pornographic content
are not included in this category.
Non-Viewable/
Infrastructure
Non-Viewable Servers that provide Internet infrastructure services and information
used by applications but not necessarily viewable by web browsers.
Includes security services such as security patch downloads, anti-virus
database updates, content filtering systems, shared authentication
services, and certificate management services such as OCSP and
CRL services. Traffic and content in this category is neither malicious
nor objectionable in nature and may be required for applications or
network traffic to function properly.
Office/Business
Applications
Web Applications Sites with interactive, Web-based office, productivity, collaboration,
and business applications including business enablement services.
Excludes email, chat/IM, or other sites that have a specific content
category.
Personal Sites Blogs/Personal Pages Sites consisting primarily of user-generated content that serves as a
vehicle for self-promotion on which a variety of personal experiences
or interests are shared. These sites do not represent businesses,
institutions or governmental entities although they might mention or be
sponsored by such bodies. Content on these sites tends to be
dynamic in nature. Content topic and tone may vary from benign to
extreme or vacillate between the two as determined by the author.
Reader comments might also contain mixed content.

Policy Guide/Page 221
Name
Previous Name
(if applicable) Definition
Piracy/Copyright
Concerns
(New) Sites that provide information or technology for cracking or pirating
software or other protected intellectual property, and sites that
distribute such media.
Political/Social Advocacy Political/Activist Groups Sites sponsored by groups or individuals that provide information on
political parties, special interest groups, organizations, factions or
individuals that promote change or reform in public policy, public
opinion, social practice, social justice, or related economic activities.
Includes sites that advance political or social agendas, lobby for
political or social change, facilitate civic engagement, and advocate
personal or collective action in its multiple forms including but not
limited to petitioning, boycotts, and demonstrations.
Scam/Questionable/Illegal Same Sites that advocate or give advice on performing acts that are illegal or
of questionable legality such as service theft, evading law
enforcement, fraud, burglary techniques, and plagiarism. Also
includes sites that promote scams such as work-from-home, pay-to-
surf, and Ponzi schemes and sites that provide or sell legally
questionable educational materials such as term papers.
Sexual Expression Alternative
Sexuality/Lifestyles
Sites that provide information about, promote, or cater to sexual
expression and sexual identity in all its forms including the full range
of sexual practices, interests, orientations, and fetishes. Does not
include sex education which is categorized in the Sex Education
category or content that is sexually gratuitous in nature, which is
categorized in the Pornography or Extreme categories.
Software Downloads Same Sites wholly dedicated to the download of software for any type of
computer or computing device whether for payment or at no charge.
Does not include sites or pages that offer a software download as a
subset of their overall content.
Technology/Internet Computers/Internet Sites that sponsor or provide information, news, reviews, opinions and
coverage of computing, computing devices and technology, consumer
electronics, and general technology. Also includes sites of technology-
related organizations and companies.
Tobacco Same Sites that discuss, encourage, promote, offer, sell, supply, or otherwise
advocate the use or creation of tobacco or tobacco-related products
including but not limited to traditional or electronic cigarettes, pipes,
cigars, chewing tobacco, hookahs, or nicotine delivery systems. Does
not include sites that sell tobacco as a subset of other products such
as grocery stores.
Uncategorized Unrated
Web Ads/Analytics Web Ads Sites that provide online advertisements, banners, or the means to
identify and market to existing or potential customers based on their
browsing or online purchasing habits including but not limited to Web
analytics sites such as visitor tracking and ranking sites. Includes
social plugins and analytics that allow site visitors to share, vote for, or
signal their appreciation of a site or its content (e.g., Facebook “Like”
or Google “+1” plugins).

Symantec Web Security Service/Page 222
Name
Previous Name
(if applicable) Definition
Web Hosting Same Sites of organizations that provide top-level domain pages, as well as
web communities, blog hosting sites, and other hosting services.
Policy Guide/Page 223
Reference:Role-BasedAccess Fields
n Client IP—The IP address of the system that initiated the web request.
n Status—Status code returned from server.
n Protocol—The content protocol type; for example, HTTP, FTP.
n Site—The name of the requested website.
n User—The user name(if the access method supported authentication).
n Content Type—Type of content returned; for example:text/html, text/plain, application/xml, application/x-
javascript.
n User Agent—The client application that performed the request; for example, the browser type and version.
n Verdict—Policy block or allow.
n Malware—The name of the detected malware/virus.
n Category—The content filtering category.
n Port—The port number used to broadcast the request.
n Search Term—Text strings entered into browser search engines.
n Web Application—The name of the application used to generate the request; for example, Sales Force, Facebook.
n Web Application Action—
n Location—Location name of the originating traffic as configured in the WSS.
n Risk Group—This content might belong a risk group.
n Subnet—The subnet to which the requesting IP address belongs.
Symantec Web Security Service/Page 224
Reference: File Types Detected by Advanced Policy
The WSS Content Filtering policy wizard allows you to select File Type categories to block or allow. The following lists provide
the recognized file extensions for each category.
Active Content
n Applet—Java applets
n Embed—plugins
n object—ActiveXcontrols
n script—JavaScripts, VPScript, and more
Archives and Compressed Files
n Q?—files compressed by the SQ program.
n 7z—7-Zip compressed file.
n ace—ACE compressed file
n ALZ—Alzip compressed file
n AT3—Sony's UMD Data compression
n bke—BackupEarth.com Data compression
n ARC
n ARJ—ARJ compressed file
n BA—Scifer Archive (.ba), Scifer External Archive Type
n big—Special file compression format used by Electronic Arts for compressing the data for many of EA's games
n BIK, bi—Bink Video file. A video compression system developed by RAD Game Tools
n BKF, bkf—Microsoft backup created by NTBACKUP.EXE
n bzip2, bz2"
n bmp—Paint
n c4—JEDMICS image files, a DOD system
n cab—Microsoft Cabinet
n cals—JEDMICS image files, a DOD system
n cpt, sea—Compact Pro (Macintosh)
n DAA—Closed-format, Windows-only compressed disk image
Policy Guide/Page 225
n deb—Debian Linux install package
n DMG—An Apple compressed/encrypted format
n EEA—An encrypted CAB, ostensibly for protecting e-mail attachments
n egg—Alzip Egg Edition compressed file
n EGT—(.egt) EGT Universal Document also used to create compressed cabinet files replaces .ecab
n ECAB—(.ECAB, .ezip) EGT Compressed Folder used in advanced systems to compress entire system folders,
replaced by EGT Universal Document
n ESS—(.ess) EGT SmartSense File, detects files compressed using the EGT compression system.
n GHO—(.gho, .ghs); Norton Ghost
n gzip—(.gz); Compressed file
n IPG—(.ipg) Format in which Apple Inc. packages their iPod games. can be extracted through Winrar
n jar—ZIP file with manifest for use with Java applications.
n LBR—Library file
n LQR—LBR Library file compressed by the SQ program.
n LHA—Lempel, Ziv, Huffman
n Lza—Lempel, Ziv, Huffman
n lzo
n lzma
n lzx
n MPQ—Used by Blizzard games
n bin—MacBinary
n PAK—Enhanced type of .ARC archive
n par—par archives
n par2—par archives
n pk3—Quake 3 archive (.pk3) (See note on Doom³)
n pk4—Doom³ archive (.pk4) (Opens similarly to a zip archive.)
n RAR—Rar Archive (.rar), for multiple file archive (rar to .r01-.r99 to s01 and so on)
n SEN—Scifer Archive (.sen), Scifer Internal Archive Type
n sit—StuffIt (Macintosh)
n sitx—StuffIt (Macintosh)
n tgz—gzipped tar file
Symantec Web Security Service/Page 226
n tar
n tar.gz—gzipped tar file
n gz—gzipped tar file
n TB—Tabbery Virtual Desktop Tab file
n TIB—Acronis True Image backup
n uha—Ultra High Archive Compression
n VIV—Archive format used to compress data for several video games, including Need For Speed: High Stakes.
n VOL—Unknown archive
n VSA—Altiris Virtual Software Archive
n Z—Unix compress file
n zoo
n zip
Audio and Music Files
Lossless Audio
n AIFF—Audio Interchange File Format
n AU
n CDDA
n IFF-8SVX
n IFF-16SV
n RAW—Raw samples without any header or sync)
n WAV—Microsoft Wave
n FLAC—Free lossless codec of the Ogg project
n LA—Lossless Audio (.la)
n PAC—LPAC (.pac)
n M4A—Apple Lossless (M4A)
n APE—Monkey's Audio (APE)
n RKA—RKAU (.rka)
n SHN—Shorten (SHN)
n TTA—Free lossless audio codec (True Audio)
Policy Guide/Page 227
n WV—WavPack (.wv)
n WMA—Windows Media Audio 9 Lossless (WMA)
Lossy Audio
n AMR—For GSM and UMTS based mobile phones
n MP2—MPEG Layer 2
n MP3—MPEG Layer 3
n Speex—Ogg project, specialized for voice, low bitrates
n GSM—GSM Full Rate, originally developed for use in mobile phones)
n WMA—Windows Media Audio (.WMA)
n AAC—(.m4a, .mp4, .m4p, .aac); Advanced Audio Coding (usually in an MPEG-4 container)
n MPC—Musepack
n VQF—Yamaha TwinVQ
n RA—Real Audio
n RM—Real Audio
n OTS—Audio File (similar to MP3, with more data stored in the file and slightly better compression; designed for use with
OtsLabs' OtsAV)
n SWA—Macromedia Shockwave Audio (Same compression as MP3 with additional header information specific to
Macromedia Director)
n VOX—Dialogic ADPCM Low Sample Rate Digitized Voice (VOX)
n VOC—Creative Labs Soundblaster Creative Voice 8-bit & 16-bit (VOC)
n DWD—DiamondWare Digitized (DWD)
n SMP—Turtlebeach SampleVision (SMP)
Other Music Formats
n AUP—Audacity project file
n BAND—GarageBand music
n CUST—DeliPlayer custom sound file format
n MID"—Standard MIDI file; most often just notes and controls but occasionally also sample dumps
n MUS—Finale Notation file, see also Finale (software)
n SIB—Sibelius Notation file, see also Sibelius (computer program)
n LY—LilyPond Notation file, see also GNU LilyPond
n GYM—Sega Genesis YM2612 log
n VGM—Stands for Video Game Music, log for several different chips
Symantec Web Security Service/Page 228
n PSF—Portable Sound Format
n NSF—NES Sound Format, bytecode program to play NES music
n MOD—Soundtracker and Protracker sample and melody modules
n PTB—Power Tab Editor tab
n S3M—Scream Tracker 3 module, with a few more effects and a dedicated volume column
n XM—Fast Tracker module, adding instrument envelopes
n IT—Impulse Tracker module, adding compressed samples, note-release actions, and more effects including a resonant
filter
n MT2—MadTracker 2 module. It could be resumed as being XM and IT combined with more features like track effects and
automation.)
n MNG—BGM for the Creatures game series, starting from Creatures 2; a free editor and player is available
n PSF—PlayStation Sound Format.
n RMJ—RealJukebox Media used for RealPlayer.
n SPC—Super Nintendo Entertainment System sound file format.
n NIFF—Notation Interchange File Format
n MusicXML
n TXM—Track ax media.
n YM—Atari ST/Amstrad CPC YM2149 sound chip format
n JAM—Jam music format
n ASF—Advanced Systems Format
n MP1—For use with UltraPlayer
Playlist Formats
n ASX—Advanced Stream Redirector (.asx)
n M3U
n PLS
n RAM—Real Audio Metafile For Real Audio files only.
n XSPF—XML Shareable Playlist Format
n ZPL—Zune Playlist format
Audio Editing and Music Production Formats
n AUP—Audacity project file
n BAND—GarageBand project file
n CEL—Adobe Audition loop file (Cool Edit Loop)
Policy Guide/Page 229
n CPR—Steinberg Cubase project file
n NPR—Steinberg Nuendo project file
n CWP—Cakewalk Sonar project file
n DRM—Steinberg Cubase drum file
n OMF—Cross-application format Open Media Framework application-exchange bundled format
n SES—Adobe Audition multitrack session file
n SNG—MIDI sequence file (MidiSoft, Korg, etc.) or n-Track Studio project file
n STF—StudioFactory project file. It contains all necessary patches, samples, tracks and settings to play the file.
n SYN—SynFactory project file. It contains all necessary patches, samples, tracks and settings to play the file.
n SND—Akai MPC sound file
Computer-Aided Design (CAD)
n 3dmlw—3DMLW (3D Markup Language for Web) files
n 3dxml—Dassault Systemes graphic representation
n ACP—VA Software VA" ; Virtual Architecture CAD file
n AR—Ashlar-Vellum Argon" ; 3D Modeling
n ART—ArtCAM model
n ASC—BRL-CAD Geometry File (old ascii format)
n ASM—Solidedge Assembly, Pro/ENGINEER Assembly
n BIN, BIM—Data Design System DDS-CAD
n CCC—CopyCAD Curves
n CCM—CopyCAD Model
n CCS—CopyCAD Session
n CAD—CadStd
n CATDrawing—CATIA V5 Drawing document
n CATPart—CATIA V5 Part document
n CATProduct—CATIA V5 Assembly document
n CATProcess—CATIA V5 Manufacturing document
n cgr—CATIA V5 graphic representation file
n CO—Ashlar-Vellum Cobalt; parametric drafting and 3D modeling
n DRW—Caddie Early version of Caddie drawing; Prior to Caddie changing to DWG
Symantec Web Security Service/Page 230
n DWG—AutoCAD and Open Design Alliance applications
n DFT—Solidedge Draft
n DGN—MicroStation design file
n DGK—Delcam Geometry
n DMT—Delcam Machining Triangles
n DXF—ASCII Drawing Interchange file format; AutoCAD
n DWB—VariCAD drawing file
n DWF—AutoDesk's Web Design Format; AutoCAD & Revit can publish to this format; similar in concept to PDF files;
AutoDesk Design Review is the reader
n EMB—Wilcom; Wilcom ES Designer Embroidery CAD file
n ESW—Agtek format
n EXCELLON, or Excellon file
n FM—FeatureCAM Part File
n FMZ—FormZ Project file
n G—BRL-CAD Geometry File
n GERBER or Gerber file
n GRB—T-FLEX CAD File
n GTC—GRAITEC Advance file format
n IAM—Autodesk Inventor Assembly file
n ICD—IronCAD 2D CAD file
n IDW—Autodesk Inventor Drawing file
n IFC—BuildingSMART for sharing AEC and FM data
n IGES—Initial Graphics Exchange Specification
n Intergraph's Intergraph Standard File Formats
n IPN—Autodesk Inventor Presentation file
n IPT—Autodesk Inventor Part file
n model—CATIA V4 part document
n PAR—Solidedge Part
n PRT—NX (recently known as Unigraphics), Pro/ENGINEER Part, CADKEY Part
n PLN—ArchiCad project
n PSM—Solidedge Sheet
Policy Guide/Page 231
n PSMODEL—PowerSHAPE Model
n PWI—PowerINSPECT File
n PYT—Pythagoras File
n SKP—SketchUp Model
n RLF—ArtCAM Relief
n RVT—AutoDesk Revit project files
n RFA—AutoDesk Revit family files
n SLDASM—SolidWorks Assembly drawing
n SLDDRW—SolidWorks 2D drawing
n SLDPRT—SolidWorks 3D part model
n STEP—Standard for the Exchange of Product model data
n STL—Stereo Lithographic data format (see STL (file format)) used by various CAD systems and stereo lithographic
printing machines.
n TCT—TurboCAD drawing template
n TCW—TurboCAD for Windows 2D and 3D drawing
n VC6—Ashlar-Vellum Graphite; 2D and 3D drafting
n VLM—Ashlar-Vellum Vellum, Vellum 2D, Vellum Draft, Vellum 3D, DrawingBoard
n VS—Ashlar-Vellum Vellum Solids
n WRL—Similar to STL, but includes color. Used by various CAD systems and 3D printing rapid prototyping machines.
Also used for VRML models on the Web.
n XE—Ashlar-Vellum Xenon; for Associative 3D Modeling
n brd—EAGLE Layout Editor Board File; Eagle is Commercial EDA software for designing PCBs (printed circuit boards).
n OASIS—Open Artwork System Interchange Standard
n VHD—A VHDL source file
n MS10—NI Multisim file
Databases
n ACCDB—Microsoft Database (Microsoft Office Access 2007)
n ADT—Sybase Advantage Database Server (ADS)
n APR—Lotus Approach data entry & reports
n BOX—Lotus Notes Post Office mail routing database
Symantec Web Security Service/Page 232
n CHML—Krasbit Technologies Encrypted database file for 1 click integration between contact management software and
the Chameleon(tm) line of imaging workflow solutions
n DAF—Digital Anchor data file
n DAT—DOS Basic
n DB—Paradox
n DBF—db/dbase II,III,IV and V, Clipper, Harbour/xHarbour, Fox/FoxPro, Oracle
n EGT—EGT Universal Document, used to compress sql databases to smaller files, might contain original EGT database
style.
n ESS—EGT SmartSense is a database of files and its compression style. Specific to EGT SmartSense
n EAP—Enterprise Architect Project
n FDB—Firebird Databases
n FDB—Navision database file
n FP, FP3, FP5, FP7"—FileMaker Pro
n FRM—MySQL table definition
n GDB—Borland InterBase Databases
n KEXI—Kexi database file (SQLite-based)
n KEXIC—Shortcut to a database connection for a Kexi databases on a server
n LDB—Temporary database file, only existing when database is open
n MDB, mdb, ldb—Microsoft Database (Access)
n ADP—Microsoft Access project (used for accessing databases on a server)
n MDE—Compiled Microsoft Database (Access)
n MDF—Microsoft SQL Server Database
n MYD—MySQL MyISAM table data
n MYI—MySQL MyISAM table index
n NCF—Lotus Notes configuration file
n NSF—Lotus Notes database
n NTF—Lotus Notes database design template
n ODB—OpenOffice.org Base
n ORA—Oracle tablespace files sometimes get this extension (also used for configuration files)
n PDB—Palm OS Database
n PDI—Portable Database Image
Policy Guide/Page 233
n PDX—Corel Paradox database management
n PRC—Palm OS resource database
n SQL—Bundled SQL queries
n REL—Sage Retrieve 4GL data file
n RIN—Sage Retrieve 4GL index file
n SDB—StarOffice's StarBase
n UDL—Universal Data Link
n WDB—Microsoft Works Database
Desktop Publishing
n DTP—Greenstreet Publisher, GST PressWorks
n INDD—Adobe InDesign
n MCF—FotoInsight Designer
n PMD—Adobe PageMaker
n PUB—Microsoft Publisher
n FM—Adobe FrameMaker
Disc Images
n ISO—The generic file format for most optical media, including CD-ROM, DVD-ROM, Blu-ray Disc, HD DVD and UMD
n NRG—The proprietary optical media archive format used by Nero applications
n IMG—For archiving MS-DOS formatted floppy disks.
n ADF—Amiga Disk Format, for archiving Amiga floppy disks
n ADZ—The GZip-compressed version of ADF
n DMS—Disk Masher System, a disk-archiving system native to the Amiga
n DSK—For archiving floppy disks from a number of other platforms, including the ZX Spectrum and Amstrad CPC
n D64—An archive of a Commodore 64 floppy disk
n SDI—System Deployment Image, used for archiving and providing "virtual disk" functionality
n MDS—DAEMON tools native disc image file format used for making images from optical CD-ROM, DVD-ROM, HD
DVD or Blu-ray Disc. It comes together with MDF file and can be mounted with DAEMON Tools or Alcohol 120%
software.
n MDX—New DAEMON Tools file format that allows to get one MDX disc image file instead of two (MDF and MDS)

Symantec Web Security Service/Page 234
n DMG—Macintosh disk image files
Executables
The WSS detection of executables involves more than just detecting file extensions; it involves the following methods.
n HTTPFile Extensions n HTTP Response Headers
n Magic Bytes n ContentDispositions
HTTPFile Extensions
8BF APP BPL class COFF
com DCU DOL EAR EGT
ELF jar XPI Mach-O nlm
s1es VAP WAR XBE XCOFF
VBX ocx TLB
HTTPResponse Headers
n application/octet-stream (might cause false-positives)
n
application/x-msdownload
n
application/x-msdos-program
n
(application|image)/(x- | x-ms | x-win- |)(metafile | wmf)
Content Dispositions
ani bat chm cmd com
cur dll exe hta hlp
msi pif reg scr vb
vbs wmf wsc wsf wsh
Fonts
n ABF—Adobe Binary Screen Font
n AFM—Adobe Font Metrics
n BDF—Bitmap Distribution Format
n BMF—ByteMap Font Format
n FNT—Bitmapped Font; Graphical Environment Manager
n FON—Bitmapped Font; Microsoft Windows
n MGF—MicroGrafx Font
n OTF—OpenType Font
Policy Guide/Page 235
n PCF—Portable Compiled Font
n PFA—Printer Font ASCII
n PFB—Printer Font Binary" ; Adobe
n PFM—Printer Font Metrics" ; Adobe
n FOND—Font Description resource" ; Mac OS
n SFD—FontForge spline font database Font
n SNF—Server Normal Format
n TFM—TeX font metric
n TTF—TrueType Font
n TTC—TrueType Font
Gaming
List of common file formats of data for video games on systems that support filesystems, most commonly PC games.
HALO Engine
n MAP—A Level, User Interface, or Sounds
n TAG—An Object
n SAV—A saved game
n LEV—A HALO ZERO Level
TrackMania United/Nations Forever Engine
n CHALLENGE.GBX—(Edited) Challenge files.
n CONSTRUCTIONCAMPAIGN.GBX—Construction campaignes files.
n CONTROLEFFECTMASTER.GBX—Menu parts.
n CONTROLSTYLE.GBX—Menu parts.
n FIDCACHE.GBX—Saved game.
n GBX—Other TrackMania items.
n REPLAY.GBX—Replays of races.
DOOM Engine
n DEH—DeHackEd files to mutate the game executable (not officially part of the DOOM engine)
n DSG—Saved game
n LMP—A lump is an entry in a DOOM wad.
n LMP— Saved demo recording
Symantec Web Security Service/Page 236
n MUS—Music file (usually contained within a WAD file)
n WAD—Data storage (contains music, maps, and textures)
Quake Engine
n BSP—(For Binary space partitioning) compiled map format
n MAP—Raw map format used by editors like GtkRadiant or QuArK
n MDL—Model for an item used in the game
n MD2—Model for an item used in the game
n MD3—Model for an item used in the game
n MD5—Model for an item used in the game
n GLM—Model for an item used in the game
n PAK—Data storage
n PK2—Data storage
n PK3—Used by the Quake II, Quake III Arena and Quake 4 game engines, respectively, to store game data, textures etc.
They are .zip files.
n PK4—Used by the Quake II, Quake III Arena and Quake 4 game engines, respectively, to store game data, textures etc.
They are .zip files.
n dat—General data contained within the .PK3/PK4 files
n roq—Video format
Unreal Engine
n U—Unreal script format
n UAX—Animations format for Unreal Engine 2
n UMX—Map format for Unreal Tournament
n UMX—Music format for Unreal Engine 1
n UNR—Map format for Unreal
n UPK—Package format for cooked content in Unreal Engine 3
n USX—Sound format for Unreal Engine 1 and Unreal Engine 2
n UT2—Map format for Unreal Tournament 2003 and Unreal Tournament 2004
n UT3—Map format for Unreal Tournament 3
n UTX—Music format for Unreal Engine 1 and Unreal Engine 2
n UXX—Cache format. These are files that client downloaded from server (which can be converted to regular formats)
Duke Nukem 3D Engine
Policy Guide/Page 237
n DMO—Save game
n GRP—Data storage
n MAP—Map (usually constructed with BUILD.EXE)
Diablo Engine
n SV—Save Game
n ITM—Item File
Other Formats
n B—Grand Theft Auto saved game files
n BO—Levels on Poing!PC
n DBPF—The Sims 2, DBPF, Package
n GC—Format used by the Steam content management system for file archives.
n IMG—Format used by Renderware-based Grand Theft Auto games for data storage
n MAP—Format used by Halo: Combat Evolved for archive compression, Doom³, and various other games
n OEC—Format used by OE-Cake for scene data storage.
n POD—Format used by Terminal Reality
n REP—Used by Blizzard Entertainment for scenario replays in StarCraft.
n SC4Lot—SimCity (All game plugins use this format, commonly with different file extensions)
n SC4Model—SimCity (All game plugins use this format, commonly with different file extensions)
n SMZIP—Auto extractor for Stepmania songs, themes and announcer packs.
Geographic Information System
n APR—ESRI ArcView 3.3 and earlier project file
n DEM—USGS DEM file format
n E00—ARC/INFO interchange file format
n GeoTIFF—Geographically located raster data
n GPX—XML-based interchange format
n MXD—ESRI ArcGIS project file, 8.0 and higher
n SHP—ESRI shapefile
n TAB—MapInfo Table file format
n DTED—Digital Terrain Elevation Data
n KML—Keyhole Markup Language, XML-based
Symantec Web Security Service/Page 238
Graphic Images/Pictures
Color Palettes
n ACT—Adobe Color Table. Contains a raw color palette and consists of 256 24-bit RGB colour values.
n PAL—Microsoft palette file
Raster Graphics
n ASE—Adobe Swatch
n ART—America Online proprietary format
n BMP—Microsoft Windows Bitmap formatted image
n BLP—Blizzard Entertainment proprietary texture format
n CIT—Intergraph is a monochrome bitmap format
n CPT—Corel PHOTO-PAINT image
n CUT—Dr. Halo image file
n DDS—DirectX texture file
n DIB—Device-Independent Bitmap graphic
n DjVu—DjVu for scanned documents
n EGT—EGT Universal Document, used in EGT SmartSense to compress *.png to yet a smaller file
n Exif—Exchangeable image file format (Exif) is a specification for the image file format used by digital cameras
n GIF—CompuServe's Graphics Interchange Format
n GPL—GIMP Palette, using a textual representation of color names and RGB values
n ICNS—file format use for icons in Mac OS X. Contains bitmap images at multiple resolutions and bitdepths with alpha
channel.
n ICO—A file format used for icons in Microsoft Windows. Contains small bitmap images at multiple resolutions and sizes.
n lbm—(.iff, .ilbm, .lbm)" ; ILBM
n ilbm—(.iff, .ilbm, .lbm)" ; ILBM
n JNG—A single-frame MNG using JPEG compression and possibly an alpha channel.
n JPEG—JFIF (.jpg or .jpeg); a lossy image format widely used to display photographic images.
n JPG—JFIF (.jpg or .jpeg)"; a lossy image format widely used to display photographic images.
n JP2—JPEG2000
n LBM—Deluxe Paint image file
n MAX—ScanSoft PaperPort document
Policy Guide/Page 239
n MIFF—ImageMagick's native file format
n MNG—Multiple Network Graphics, the animated version of PNG
n MSP—A file format used by old versions of Microsoft Paint. Replaced with BMP in Microsoft Windows 3.0
n NITF—A U.S. Government standard commonly used in Intelligence systems
n OTA—A specification designed by Nokia for black and white images for mobile phones
n PBM—Portable bitmap
n PC1—Low resolution, compressed Degas picture file
n PC2—Medium resolution, compressed Degas picture file
n PC3—High resolution, compressed Degas picture file
n PCF—Pixel Coordination Format
n PCX—A lossless format used by ZSoft's PC Paint, popular at one time on DOS systems.
n PDN—Paint.NET image file
n PGM—Portable graymap
n PI1—Low resolution, uncompressed Degas picture file
n PI2—Medium resolution, uncompressed Degas picture file. Also Portrait Innovations encrypted image format.
n PI3—High resolution, uncompressed Degas picture file
n PICT—Apple Macintosh PICT image
n PCT—Apple Macintosh PICT image
n PNG—Portable Network Graphic (lossless, recommended for display and edition of graphic images)
n PNM—Portable anymap graphic bitmap image
n PPM—Portable Pixmap (Pixel Map) image
n PSB—Adobe Photoshop Big image file (for large files)
n PDD—Adobe Photoshop Drawing
n PSD—Adobe Photoshop Drawing
n PSP—Paint Shop Pro image
n PX—Pixel image editor image file
n PXR—Pixar Image Computer image file
n QFX—QuickLink Fax image
n RAW—General term for minimally processed image data (acquired by a digital camera)
n RLE—A run-length encoded image
Symantec Web Security Service/Page 240
n SCT" ; Scitex Continuous Tone image file
n SGI, RGB, INT. BW—Silicon Graphics Image
n tga—Truevision TGA (Targa) image
n targa—Truevision TGA (Targa) image
n icb—Truevision TGA (Targa) image
n vda—Truevision TGA (Targa) image
n vst—Truevision TGA (Targa) image
n pix—Truevision TGA (Targa) image
n TIFF—Tagged Image File Format (usually lossless, but many variants exist, including lossy ones)
n tif—ISO 12234-2; tends to be used as a basis for other formats rather than in its own right.
n XBM—X Window System Bitmap
n XCF—GIMP image (from Gimp's origin at the eXperimental Computing Facility of the University of California)
n XPM—X Window System Pixmap
Vector graphics
n AWG—Ability Draw
n AI—Adobe Illustrator Document
n EPS—Encapsulated Postscript
n CGM—Computer Graphics Metafile an ISO Standard
n CDR—CorelDRAW vector image
n CMX—CorelDRAW vector image
n DXF—ASCII Drawing Interchange file Format, used in AutoCAD and other CAD-programs
n E2D—2-dimensional vector graphics used by the editor which is included in JFire
n EGT—EGT Universal Document, EGT Vector Draw images are used to draw vector to a website
n SVG—Scalable Vector Graphics, employs XML
n STL—Stereo Lithographic data format (see STL (file format)) used by various CAD systems and stereo lithographic
printing machines. See the Computer Aided Design section above.
n wrl—Virtual Reality Modeling Language, for the creation of 3D viewable web images.
n X3D
n V2D—Voucher design used by the voucher management included in JFire
n WMF—Windows Meta File
n EMF—Enhanced (Windows) MetaFile, an extension to WMF
Policy Guide/Page 241
n ART—Xara; Drawing (superseded by XAR)
n XAR—Xara; Drawing
3D graphics
n 3DMF—QuickDraw 3D Metafile (.3dmf)
n 3DS—Legacy 3D Studio Model (.3ds)
n AC—AC3D Model (.ac)
n AN8—Anim8or Model (.an8)
n AOI—Art of Illusion Model (.aoi)
n B3D—Blitz3D Model (.b3d)
n BLEND—Blender (.blend)
n BLOCK—Blender encrypted blend files (.block)
n C4D—Cinema 4D (.c4d)
n Cal3D—Cal3D (.cal3d)
n CCP4—X-ray crystallography voxels (electron density)
n CFL—Compressed File Library (.cfl)
n COB—Caligari Object (.cob)
n CORE3D—Coreona 3D Coreona 3D Virtual File(.core3d)
n CTM—OpenCTM (.ctm)
n DAE—COLLADA (.dae)
n DFF—RenderWare binary stream, commonly used by Grand Theft Auto III-era games as well as other RenderWare
titles
n DTS—Torque Game Engine (.dts)
n EGG—Panda3D Engine
n FACT—Electric Image (.fac)
n FBX—Autodesk FBX (.fbx)
n G—BRL-CAD geometry (.g)
n GLM—Ghoul Mesh (.glm)
n LWO—Lightwave Object (.lwo)
n LWS—Lightwave Scene (.lws)
n LXO—Luxology Modo (software) file (.lxo)
n MA—Autodesk Maya ASCII File (.ma)
Symantec Web Security Service/Page 242
n MAX—Autodesk 3D Studio Max file (.max)
n MB—Autodesk Maya Binary File (.mb)
n MD2—Quake 2 model format (.md2)
n MD3—Quake 3 model format (.md3)
n MDX—Blizzard Entertainment's own model format (.mdx)
n MESH—New York University(.m)
n MESH—Meshwork Model (.mesh)
n MM3D—Misfit Model 3d (.mm3d)
n MRC—Voxels in cryo-electron microscopy
n NIF—Gamebryo NetImmerse File (.nif)
n OBJ—OBJ (.obj)
n OFF—OFF Object file format (.off)
n PRC—Adobe PRC (embedded in PDF files)
n POV—POV-Ray Document (.pov)
n RWX—RenderWare Object (.rwx)
n SIA—Nevercenter Silo Object (.sia)
n SIB—Nevercenter Silo Object (.sib)
n SKP—Google Sketchup file (.skp)
n SLDASM—SolidWorks Assembly Document (.sldasm)
n SLDPRT—SolidWorks Part Document (.sldprt)
n SMD—Valve's format. (.smd)
n U3D—Universal 3D file format (.u3d)
n WINGS—Wings3D (.wings)
n X—DirectX 3D Model (.x)
n X3D—Extensible 3D (.x3d)
n Z3D—Zmodeler (.z3d)
Policy Guide/Page 243
Miscellaneous
Other
n AXD—Cookie extensions found in temporary internet folder
n AXX—Encrypted file, created with Axcrypt
n BAK—Backup file
n BDF—Binary Data Format; raw data from recovered blocks of unallocated space on a hard drive
n CREDX—CredX Dat File
n DUPX—DuupeCheck database management tool project file
n GA3—Graphical Analysis 3
n GED—GEDCOM, (GEnealogical Data COMmunication) file format for exchanging genealogical data between different
genealogy software.
n HLP—Windows help file
n IGC—Flight tracks downloaded from GPS devices in the FAI's prescribed format
n INI—Ini file used by many applications to store configuration
n INF—Similar file format to INI; used to install device drivers under Windows, inter alia.
n KMC—Tests made with KatzReview's MegaCrammer
n LNK—Binary format file, stores shortcuts under MS Windows 95 and later
n LSM—LSMaker script file (program using layered .jpg to create special effects; specifically designed to render
lightsabers from the Star Wars universe) (.lsm)
n PIF—Used for running MS-DOS programs under Windows
n POR—
Portable
SPSS files, readable by PSPP
n PXZ—Compressed file to exchange media elements with PSALMO
n RISE—File containing RISE generated information model evolution
n TOPC—TopicCrunch SEO Project file holding keywords, domain and search engine settings (ASCII);
n TOS—Character file from The Only Sheet
n TMP—Temporary file
n URL—INI format file, used by Internet Explorer to save Favorites
n ZED—My Heritage Family Tree
Symantec Web Security Service/Page 244
Cursors
n ANI—Animated Cursor
n CUR—Cursor Files
Financial Records
n TAX—TurboTax File
n YNAB—YNAB File
n MYO—MYOB Limited (Windows) File
n MYOB—MYOB Limited (Mac) File
Office Docs
Documents
n ABW—AbiWord document
n ACL—MS Word AutoCorrect List
n AFP—Advanced Function Presentation
n ANS—ANSI text with Layout
n ASC—ASCII text with Layout
n AWW—Ability Write
n CSV—ASCII text encoded as Comma Separated Values, used in most spreadsheets such as Microsoft Excel or by most
database management systems
n CWK—ClarisWorks / AppleWorks document
n DOC—Microsoft Word document
n DOCX—Office Open XML Text document or Microsoft Office Word 2007 for Windows/2008 for Mac
n DOT—Microsoft Word document template
n DOTX—Office Open XML Text document template
n EGT—EGT Universal Document
n FTM—Fielded Text Meta
n FTX—Fielded Text (Declared)
n HTML—HyperText Markup Language (.html, .htm)
n HWP—Haansoft(Hancom) Hangul Word Processor document
n HWPML—Haansoft(Hancom) Hangul Word Processor Markup Language document
n LWP—Lotus Word Pro
Policy Guide/Page 245
n MCW—Microsoft Word for Macintosh (versions 4.0; 5.1)
n NB—Mathematica Notebook
n NBP—Mathematica Player Notebook
n ODM—OpenDocument Master document
n ODT—OpenDocument Text document
n OTT—OpenDocument Text document template
n PAGES—Apple Pages document
n PAP—Papyrus word processor document
n PDAX—Portable Document Archive (PDA) document index file
n PDF—Portable Document Format
n Radix-64
n RTF—Rich Text document
n SDW—StarWriter text document, used in earlier versions of StarOffice
n STW—StarOffice/OpenOffice.org/NeoOffice text document template
n SXW—StarOffice/OpenOffice.org/NeoOffice text document
n TeX—Typesetting system
n Texinfo—GNU Project
n Troff
n TXT—ASCII or Unicode plaintext
n UOF—Uniform Office Format
n UOML—UniqueObject Markup Language (UOML) is a XML-based markup language; uniqueobject.com
n WPD—WordPerfect document
n WPS—Microsoft Works document
n WPT—Microsoft Works document template
n WRD—WordIt! Document
n WRF—ThinkFree Write
n WRI—Microsoft Write document
n XHTML, xht—eXtensible Hyper-Text Markup Language
n XML—eXtensible Markup Language
Mathematical MarkupLanguage (MML)
n MathML—Mathematical Markup Language (.mml)
Symantec Web Security Service/Page 246
Page DescriptionLanguage
n DVI
n EGT—Universal Document can be used to store css type styles (*.egt)
n PLD
n PCL
n PDF—Portable Document Format
n ps—PostScript
n SNP—Microsoft Access Report Snapshot
n XPS
n XSL-FO—Formatting Objects
n CSS
n XSLT—XML Style Sheet (.xslt, .xsl)
n XSL—XML Style Sheet (.xslt, .xsl)
n TPL—Web template (.tpl)
Personal Information Manager
n MSG—Microsoft Outlook task manager
n ORG—Lotus Organizer PIM package
n PST—Microsoft Outlook e-mail communication
n SC2—Microsoft Schedule+ calendar
Presentation
n KEY—Apple Keynote Presentation
n NB—Mathematica Slideshow
n NBP—Mathematica Player slideshow
n ODP—OpenDocument Presentation
n OTP—OpenDocument Presentation template
n POT—Microsoft PowerPoint template
n PPS—Microsoft PowerPoint Show
n PPT—Microsoft PowerPoint Presentation
n PPTX—Office Open XML Presentation
n PRZ—Lotus Freelance Graphics
n SDD—StarOffice's StarImpress
Policy Guide/Page 247
n SHF—ThinkFree Show
n SHOW—Haansoft(Hancom) Presentation software document
n SHW—Corel Presentations slide show creation
n SSPSS—SongShow Plus Slide Show
n STI—OpenOffice.org 1.url.extension=Presentation template
n SXI—OpenOffice.org 1.url.extension=Presentation
n WATCH—Dataton Watchout Presentation
Project Management Software
n MPP—Microsoft Project
Formats of files used in software for bibliographic information (citation) management.
n bib—BibTeX
n enl—EndNote
n ris—Research Information Systems RIS (file format)
Spreadsheet
n 123—Lotus 1-2-3
n AWS—Ability Spreadsheet
n CLF—ThinkFree Calc
n CELL—Haansoft(Hancom) SpreadSheet software document
n CSV—Comma-Separated Values
n numbers—An Apple Numbers Spreadsheet file
n gnumeric—Gnumeric spreadsheet, a gziped XML file
n ODS—OpenDocument spreadsheet
n OTS—OpenDocument spreadsheet template
n QPW—Quattro Pro spreadsheet
n SDC—StarOffice/OpenOffice.org StarCalc Spreadsheet
n SLK—SYLK (SYmbolic LinK)
n STC—StarOffice/OpenOffice.org
n SXC—StarOffice/OpenOffice.org 1.url.extension=Spreadsheet
n TAB—Tab-Delimited Columns; also TSV (Tab-Separated Values)
n TXT—Tab-Delimited Columns
n VC—Visicalc
Symantec Web Security Service/Page 248
n WK1—Lotus 1-2-3 up to version 2.01
n WK3—Lotus 1-2-3 version 3.0
n WK4—Lotus 1-2-3 version 4.0
n WKS—Lotus 1-2-3
n WKS—Microsoft Works
n WQ1—Quattro Pro DOS version
n XLK—Microsoft Excel worksheet backup
n XLS—Microsoft Excel worksheet sheet (97-2003)
n XLSB—Microsoft Excel binary workbook
n XLSM—Microsoft Excel Macro-enabled workbook
n XLSX—Office Open XML worksheet sheet
n XLR—Microsoft Works version 6.0
n XLT—Microsoft Excel worksheet template
n XLTM—Microsoft Excel Macro-enabled worksheet template
n XLW—Microsoft Excel worksheet workspace (version 4.0)
Tabulated data
n tab
n CSV—Comma-Separated Values
n db—Databank format; accessible by many economet
Scripts
n AHK—AutoHotkey script file
n APPLESCRIPT—See SCPT.
n AS—Adobe Flash ActionScript File
n AU3—AutoIt version 3
n BAT—Batch file
n BAS—QBasic & QuickBASIC
n CMD—Batch file
n EGG—Chicken
n EGT—EGT Asterisk Application Source File, EGT Universal Document
n HTA—HTML Application
Policy Guide/Page 249
n IBI—Icarus script
n ICI—ICI
n ITCL—Itcl
n JS—JavaScript and JScript
n JSFL—Adobe JavaScript language
n LUA—Lua
n M—Mathematica package file
n MRC—mIRC Script
n NCF—NetWare Command File (scripting for Novell's NetWare OS)
n NUT—Squirrel
n PHP—PHP
n PHP?—PHP (? = version number)
n PL—Perl
n PM—Perl module
n PS1—Windows PowerShell shell script
n PS1XML—Windows PowerShell format and type definitions
n PSC1—Windows PowerShell console file
n PSD1—Windows PowerShell data file
n PSM1—Windows PowerShell module file
n PY—Python
n PYC—Python
n PYO—Python
n R—R scripts
n RB—Ruby
n RDP—RDP connection
n SCPT—Applescript
n SCPTD—See SCPT.
n SDL—State Description Language
n SH—Shell script
n TCL—Tcl
Symantec Web Security Service/Page 250
n VBS—Visual Basic Script
Source Code
Object Code, Executable Files, Shared and Dynamically-Linked Libraries
n 8BF—Files are plugins for some photo editing programs including Adobe Photoshop, Paint Shop Pro, GIMP and Helicon
Filter.
n APP—Apple application program executable file
n BPL—A Win32 PE file created with Borland Delphi or C++Builder containing a package.
n Class—Files; used in Java
n COFF—(No suffix for executable image, .o for object file) UNIX Common Object File Format, now often superseded by
ELF
n COM—Files; commands used in DOS
n DCU—Files; Delphi compiled unit
n DOL—The file format used by the Gamecube and Wii, short for Dolphin the codename of the Gamecube.
n EAR—Files; archives of Java enterprise applications
n EGT—A basic Universal Document and also Launches the EGT SmartSense executable file.
n ELF—(No suffix for executable image, .o for object files, .so for shared object files); Used in many modern Unix and Unix-
like systems, including Solaris, other System V Release 4 derivatives, Linux, and BSD
n JAR—Files; archives of Java class files
n XPI—A PKZIP archive that can be run by Mozilla Web browsers to install software. (.xpi)
n Mach-O—(No suffix for executable image, .o for object files, .dylib and .bundle for shared object files); Mach-based
systems, notably native format of Mac OS X
n nlm—NetWare Loadable Module (.NLM); the native 32-bit binaries compiled for Novell's NetWare Operating System
(versions 3 and newer)
n s1es—Executable used for S1ES learning system.
n vap—Value Added Process (.VAP); the native 16-bit binaries compiled for Novell's NetWare Operating System (version 2,
NetWare 286, Advanced NetWare, etc.)
n WAR—Files;archives of Java Web applications
n XBE—Xbox executable
n XCOFF—(No suffix for executable image, .o for object files, .a for shared object files); Extended COFF, used in AIX
Object Extensions
n VBX—Visual Basic Extensions
n OCX—Object Control Extensions
Policy Guide/Page 251
n TLB—Windows Type Library
Source Code for Computer Programs
n ADA, ADB, 2.ADA—Ada (body) source
n ADA, ADB— Ada (body) source
n ;ADS, 1.ADA—Ada (specification) source
n ADS—Ada (specification) source
n ASM, S—Assembly Language source
n BAS—BASIC, Visual Basic module
n BB—Blitz3D
n BMX—BlitzMax
n C—C source
n CLS—Visual Basic class
n COB, CBL—Cobol source
n CPP, CC, CXX, C—C++ source
n CS—C# source
n CSPROJ—C# project (Visual Studio .NET)
n D—D source
n DBA—DarkBASIC source
n DBPro—DarkBASIC Professional project
n E—Eiffel source
n EFS—EGT Forever Source File
n EGT—EGT Asterisk Source File, could be J, C#, VB.net, EF 2.0 (EGT Forever)
n EL—Emacs Lisp source
n FOR—Fortran source
n FTN—Fortran source
n F—Fortran source
n F77—Fortran source
n F90—Fortran source
n FRM—Visual Basic form
n FRX—Visual Basic form stash file (binary form file)
n GED—Game Maker Extension Editable file as of version 7.0
Symantec Web Security Service/Page 252
n GM6—Game Maker Editable file as of version 6.x
n GMD—Game Maker Editable file up to version 5.x
n GMK—Game Maker Editable file as of version 7.0
n GML—Game Maker Language script file
n H—C/C++ header file
n HPP—C++ header file
n HXX—C++ header file
n HS—Haskell source
n INC—Turbo Pascal included source
n JAVA—Java source
n L—Lex source
n LISP—Common Lisp source
n M—Objective-C source
n M—MATLAB
n M—Mathematica
n M4—m4 source
n ML—Standard ML / Objective CAML source
n N—Nemerle source
n PAS—Pascal source (DPR for projects)
n P—Parser source
n PIV—Pivot stickfigure animator
n PL—Perl
n PRG—db, clipper, Microsoft FoxPro, harbour and Xbase
n PY—Python programming language source
n RESX—Resource file for .NET applications
n RC, RC2—Resource script files to generate resources for .NET applications
n SCI, SCE—Scilab
n SCM—Scheme source
n SKB, SKC—Sage Retrieve 4GL Common Area (Main and Amended backup)
n SKD—Sage Retrieve 4GL Database
Policy Guide/Page 253
n SKF, SKG—Sage Retrieve 4GL File Layouts (Main and Amended backup)
n SKI—Sage Retrieve 4GL Instructions
n SKK—Sage Retrieve 4GL Report Generator
n SKM—Sage Retrieve 4GL Menu
n SKO—Sage Retrieve 4GL Program
n SKP—Sage Retrieve 4GL Print Layouts (Main and Amended backup)
n SKS—Sage Retrieve 4GL Screen Layouts (Main and Amended backup)
n SKQ—Sage Retrieve 4GL Print Layouts (Main and Amended backup)
n SKT—Sage Retrieve 4GL Screen Layouts (Main and Amended backup)
n SKZ—Sage Retrieve 4GL Security File
n SLN—Visual Studio solution
n SPIN—Spin source (for Parallax Propeller microcontrollers)
n STK—Stickfigure file for Pivot stickfigure animator
n VAP—Visual Studio Analyzer project
n VB—Visual Basic.NET source
n VIP—Visual Basic project
n VBP—Visual Basic project
n VBG—Visual Studio compatible project group
n VBPROJ—Visual Basic.NET project
n VCPROJ—Visual C++ project
n VDPROJ—Visual Studio deployment project
n Y—YACC source
VideoFiles
Video File Formats
n AAF—Mostly intended to hold edit decisions and rendering information, but can also contain compressed media
essence)
n 3GP—The most common video format for cell phones
n GIF—Animated GIF (simple animation)
n ASF—Container (enables any form of compression to be used; MPEG-4 is common; video in ASF-containers is also
called Windows Media Video (WMV))
Symantec Web Security Service/Page 254
n AVCHD—Advanced Video Codec High Definition
n AVI—Container (a shell, which enables any form of compression to be used)
n CAM—An MSN webcam log file
n DAT—Video standard data file (automatically created when we attempted to burn as video file on the CD)
n DSH
n FLV—Flash video (encoded to run in a flash animation)
n M1V—Video
n M2V
n FLA—Macromedia Flash (for producing)
n FLR—Text file that contains scripts extracted from SWF by a free ActionScript decompiler named FLARE
n SOL—Adobe Flash shared object ("Flash cookie")
n M4V—File format for videos for iPods and PlayStation Portables developed by Apple
n mkv—Matroska is a container format, which enables any video format such as MPEG-4 ASP or AVC to be used along
with other content such as subtitles and detailed meta information
n WRAP—MediaForge (*.wrap)
n MNG—Mainly simple animation containing PNG and JPEG objects, often somewhat more complex than animated GIF
n mov—Container which enables any form of compression to be used; Sorenson codec is the most common; QTCH is the
filetype for cached video and audio streams
n MPEG—.mpeg, .mpg, .mpe
n MPG—.mpeg, .mpg, .mpe
n MPE—.mpeg, .mpg, .mpe
n MP4—Multimedia container (most often used for Sony's PlayStation Portable and Apple's iPod)
n MXF—Material Exchange Format (standardized wrapper format for audio/visual material developed by SMPTE)
n ROQ—Used by Quake 3
n NSV—Nullsoft Streaming Video (media container designed for streaming video content over the Internet)
n Ogg—Container, multimedia
n RM—RealMedia
n SVI—Samsung video format for portable players
n SMI—SAMI Caption file (HTML like subtitle for movie files)
n SWF—Macromedia Flash (for viewing)
n WMV—Windows Media Video (See ASF)
Policy Guide/Page 255
Video Editing & Production formats
n FCP—Final Cut Pro project file
n MSWMM—Windows Movie Maker project file
n PPJ—Adobe Premiere Pro video editing file
n IMOVIEPROJ—iMovie project file
n VEG, VEG-BAK—Sony Vegas project file
n SUF—Sony camera configuration file (setup.suf) produced by XDCAM-EX camcorders
Virtual Machines
Microsoft Virtual PC/Virtual Server
n VFD—Virtual Floppy Disk (.vfd)
n VHD—Virtual Hard Disk (.vhd)
n VUD—Virtual Undo Disk (.vud)
n VMC—Virtual Machine Configuration (.vmc)
n VSV—Virtual Machine Saved State (.vsv)
EMC VMware ESX/GSX/Workstation/Player
n LOG—Virtual Machine Logfile (.log)
n VMDK—Virtual Machine Disk (.vmdk, .dsk)
n NVRAM—Virtual Machine BIOS (.nvram)
n VMEM—Virtual Machine paging file (.vmem)
n VMSD—Virtual Machine snapshot metadata (.vmsd)
n VMSN—Virtual Machine snapshot (.vmsn)
n VMSS—Virtual Machine suspended state (.vmss, .std)
n STD—Virtual Machine suspended state (.vmss, .std)
n VMTM—Virtual Machine team data (.vmtm)
n VMX—Virtual Machine configuration (.vmx, .cfg)
n VMXF—Virtual Machine team configuration (.vmxf)
Virtualbox
n VDI—VirtualBox Virtual Disk Image (.vdi)
Symantec Web Security Service/Page 256
Parallels Workstation
n HDD—Virtual Machine hard disk (.hdd)
n PVS—Virtual Machine preferences/configuration (.pvs)
n SAV—Virtual Machine saved state (.sav)


